Executive Summary
Dropzone AI integrates with AWS GuardDuty to autonomously investigate alerts in real-time, pulling context from CloudTrail and other AWS services to deliver decision-ready reports in minutes instead of hours. This integration requires no playbooks or custom code, works 24/7, and continuously learns from your environment to improve accuracy over time.
Introduction
AWS GuardDuty provides critical threat detection across your AWS environment, surfacing everything from unauthorized access attempts to signs of data exfiltration. However, identifying threats is only the first step in investigating them, and that is where the real work begins.
Security teams are often left sifting through a flood of GuardDuty findings, trying to determine which alerts represent real threats and which are benign. Manual triage takes time, strains resources, and increases the risk of missing something critical.
That's where Dropzone AI comes in. By integrating directly with GuardDuty, Dropzone is an autonomous AI SOC analyst that investigates every alert the moment it fires. No playbooks or prompts required. No alerts waiting in the queue. Just fast, accurate, evidence-backed conclusions delivered in minutes.
Autonomous Investigations for Every AWS GuardDuty Alert
Dropzone AI doesn't just receive alerts from GuardDuty; it investigates every alert like a seasoned analyst would. The moment a GuardDuty finding is generated, Dropzone launches a full investigation automatically, without relying on human input or prewritten playbooks.
The AI reasons to form a hypothesis about the alert, pulls contextual evidence from AWS services like CloudTrail, IAM, and S3 with targeted queries to understand what happened, when, and whether it truly poses a risk. The AI SOC analyst correlates behavioral patterns, historical baselines, and organizational knowledge to form a hypothesis and then tests that hypothesis across your cloud environment.
Each alert kicks off a dynamic, context-aware workflow. Here's how it works:
- Trigger & Ingestion - A GuardDuty alert, like an unusual spike in S3 downloads—is sent to your SIEM or cloud-native monitoring platform.
- Hypothesis Generation - Dropzone forms an initial hypothesis about the nature of the alert. Is it an exfiltration attempt? Misuse of credentials? Or something else entirely?
- Context Gathering - The AI queries CloudTrail, IAM logs, and other AWS telemetry to gather event-level details. For example, it pulls container or user IDs, access times, and target resource metadata.
- Behavioral Analysis- It evaluates user or entity behavior against historical baselines. Has this IAM role accessed this S3 bucket before? Is this download volume unusual?
- Root Cause Determination - In a recent case, Dropzone traced abnormal S3 access back to a scheduled backup process, allowing it to dismiss the alert as a false positive accurately and automatically.
- Evidence Compilation - All queries, raw data, and investigation steps are logged as immutable evidence, allowing human analysts to instantly audit or validate the AI's logic.
- Report Delivery - The system produces a decision-ready report summarizing the alert, key findings, supporting evidence, and recommended subsequent actions.
This end-to-end investigation usually takes just a few minutes versus the 15–30 minutes a human analyst would need to chase it down manually. At scale, your team can stop spending nights and weekends triaging cloud alerts and start focusing on the threats that matter.
How the Integration Works
The integration between Dropzone AI and AWS GuardDuty is designed to feel less like wiring tools together and more like adding a cloud-native analyst to your security team, one that never sleeps.
Once connected via AWS APIs, Dropzone begins ingesting GuardDuty cloud security findings in real time. But it doesn't stop at ingestion. Behind the scenes, the AI immediately launches an autonomous investigation querying services like CloudTrail, IAM, and S3 to gather the evidence needed to understand what's happening and why the alert was triggered.
This is where Dropzone starts connecting the dots: it traces user actions, checks access logs, evaluates behavior against historical patterns, and references institutional knowledge like past tickets or known safe behaviors. The AI builds out the full context, forming and testing hypotheses to determine whether the alert is a real threat or just a false alarm.
The result isn't just a raw export of logs or a generic summary. It's a fully formed investigation with an executive overview, supporting evidence, contextual risk analysis, and recommended next steps. It is delivered in a structured, decision-ready format that is ready for your team to validate or take action immediately.
Because this process starts the moment the alert arrives, there's no need to assign it manually or wait for someone to pick it up. Dropzone operates continuously, investigating every GuardDuty finding consistently and speedily. What used to take 20–30 minutes now happens in under 10 without draining your team's time or attention.
Key Benefits for Security & DevOps Teams
Pairing Dropzone AI with AWS GuardDuty transforms how security and DevOps teams handle cloud security alerts. Instead of alert queues piling up, every GuardDuty finding is investigated instantly and intelligently. Dropzone doesn't just automate; it reasons learns, and adapts, delivering decision-ready reports within minutes and freeing your analysts to focus on what truly matters: stopping real threats.
- Faster Cloud Alert Investigations - Traditional triage of GuardDuty alerts can take 20–40 minutes per finding. With Dropzone AI, investigations begin when the alert hits automatically, pulling logs, assessing context, and delivering results in under 10 minutes. This dramatically cuts down the Mean Time to Acknowledge (MTTA) and accelerates the Mean Time to Respond (MTTR).
- Noise Reduction & False Positive Elimination - Dropzone doesn't just react to alerts—it reasons through them. It checks behavioral baselines, correlates identity data, and references prior case history to determine which findings are meaningful. The result: fewer escalations, less noise, and more confidence in what makes it through.
- No Playbooks or Custom Logic Required - Forget fragile scripts or endless SOAR playbook tuning. Dropzone adapts dynamically to your AWS environment and learns from each investigation, delivering high-quality results without requiring pre-defined logic or constant maintenance.
- Always-On, Autonomous Investigations - Dropzone works 24/7, investigating alerts at 2 AM just as reliably as it does at noon. Whether your team is online, out of the office, or dealing with other priorities, every GuardDuty finding gets the same rapid, thorough attention.
- Deep, Native AWS Integration - Dropzone connects directly to GuardDuty and other AWS services like CloudTrail and IAM. It queries telemetry, pulls contextual insights, and builds a complete picture of each alert using native data; no extra connectors or middleware is needed.
- Clear, Decision-Ready Reports - Each investigation ends with a concise, structured report. Analysts receive a summary of the alert, a breakdown of the evidence, and actionable recommendations, and no more chasing down logs or digging through CloudTrail manually.
What Makes This Integration Different?
Most tools claim to "automate" alert responses and rely on brittle rules or rigid SOAR playbooks. They follow static instructions: if X, do Y. That's fine for known, repetitive tasks such as policy-based responses, but it breaks down fast when real-world complexity enters the picture. Common alert investigations like unusual logins can take many twists and turns that would befuddle a playbook-based response.
Dropzone AI takes an entirely different approach.
It doesn't follow playbooks, but reasons through alerts.
Each GuardDuty finding is treated as a unique cloud security investigation to consider, just like a human analyst would treat it. Dropzone uses recursive reasoning to analyze the alert, pulling data from CloudTrail logs, IAM roles, user behavior, and prior investigations across your AWS environment. It dynamically adjusts its investigation path based on what it finds.
There are no scripts to maintain. No logic trees to update. No "if-then" workflows to troubleshoot.
And unlike most automation tools, Dropzone learns on the job. It builds institutional memory from your past incidents and from user feedback. Over time, it gets more accurate and better at filtering noise so that you can spend your time on real threats instead of false positives.
That gives security teams something rare in cloud security: adaptive intelligence. It's not just automation. Your AI SOC analyst is an AI teammate that evolves with your environment, delivering consistency, precision, and context-aware investigations at scale.
When the noise doesn't stop, and the cloud never sleeps, Dropzone AI ensures your GuardDuty alerts are more than just signals. They're answers.
Setup & Deployment: Fast, Simple, Lightweight
Integrating Dropzone AI with AWS GuardDuty is designed to be frictionless. There's no complex scripting, no playbooks to build, and no long onboarding cycles. In under 30 minutes, you'll have a fully operational AI SOC analyst investigating cloud alerts on your behalf. Read the Dropzone AI documentation for integrating with AWS.
Authentication Process
Authenticate Securely - Dropzone connects to your AWS environment using secure API credentials or OAuth. It's read-only by default, ensuring a safe, minimal-access footprint. Once authenticated, findings are pulled from GuardDuty.
Configuration Options
Define Alert Scope - Not every GuardDuty finding needs investigation. Dropzone allows you to specify which alerts to prioritize privilege escalation attempts, unusual data access, or EC2 instance anomalies.
Deployment Steps
Enable Autonomous Investigations - As soon as the integration is active, Dropzone investigates real-time alerts. Each GuardDuty finding triggers an end-to-end workflow gathering data from AWS services, checking with reputation services, looking up user and account roles in business systems, correlating indicators from other security tools, and producing a structured, decision-ready report without manual steps.
Ongoing Optimization
Train & Optimize - Dropzone learns from your environment. As analysts provide feedback and resolve cases, the system builds organizational memory, refining its reasoning and reducing false positives over time. It just works on Day 1, and gets smarter every day.
Whether you're a lean team under pressure or an enterprise looking to scale your response capabilities, Dropzone makes bringing AI investigation into your AWS security stack easy without breaking workflows or budgets.
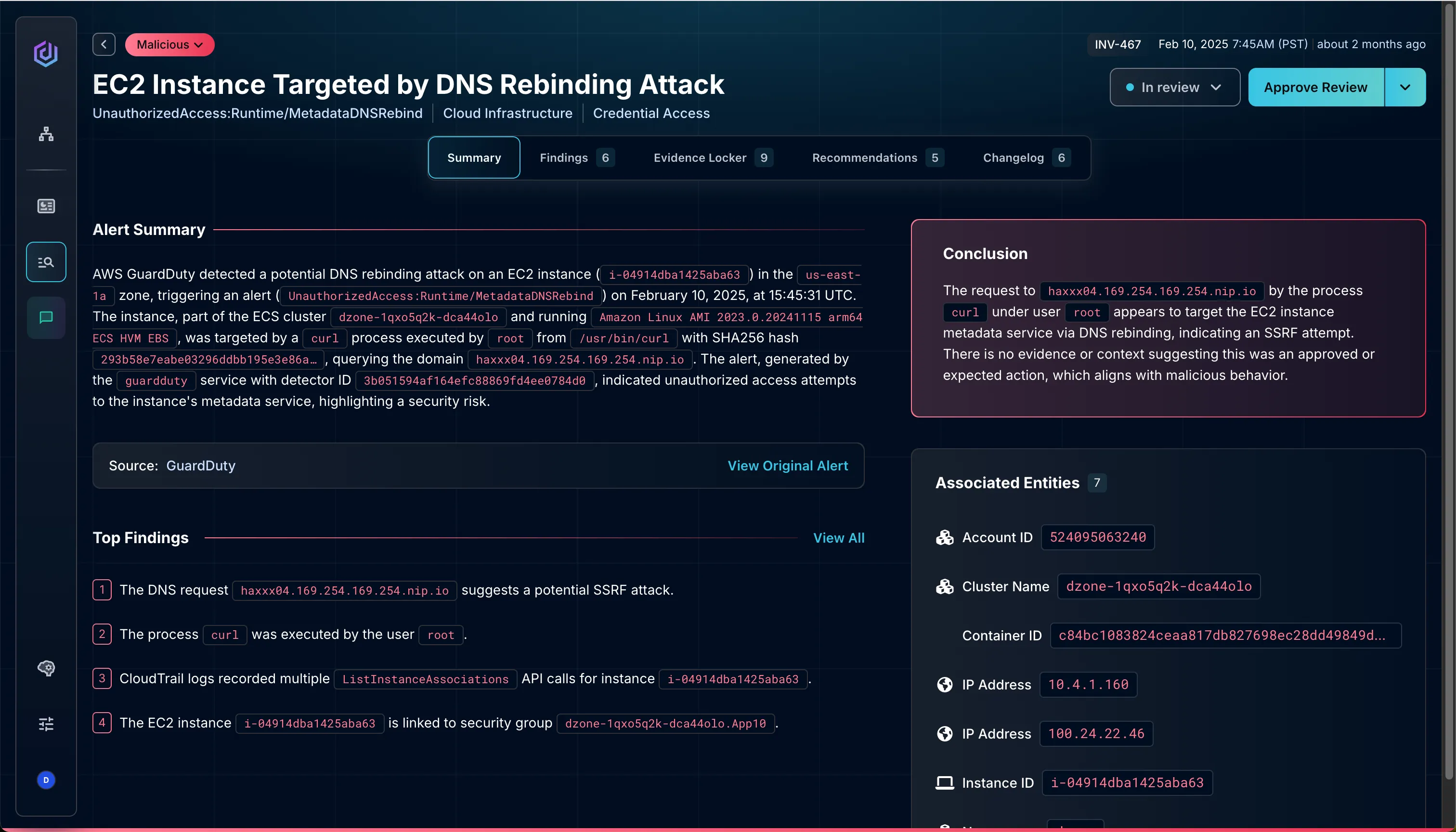
Final Thoughts & Next Steps
Integrating Dropzone AI with AWS GuardDuty moves your security team beyond basic detection into real, scalable investigation.
Instead of alert queues piling up, every GuardDuty finding is investigated within minutes. Dropzone doesn't just automate; it reasons learns, and adapts, delivering decision-ready reports within minutes and freeing your analysts to focus on what truly matters: stopping real threats.
By cutting down MTTA and accelerating every step of the incident workflow, Dropzone ensures that your cloud security operations are always one step ahead—even when your team is offline.
Whether you're running lean, scaling fast, or simply tired of chasing noise, Dropzone is your AI teammate in the cloud. No playbooks, no delays, and no alerts left behind.
Curious how it works in action? Schedule a demo or experience our AI SOC analyst through our self-guided demo to see how Dropzone AI can investigate your AWS alerts.