Introduction: The Growing Crisis in Security Operations
Security Operations Centers (SOCs) face an unprecedented challenge in today's threat landscape. The volume, sophistication, and velocity of cyber threats have outpaced human capacity to respond effectively. As digital infrastructure expands and attack surfaces grow, security teams find themselves overwhelmed by alerts while threat actors operate at machine speed.
Key statistics highlighting this security operations crisis:
- The average enterprise SOC receives over 10,000 alerts daily
- Security analysts typically spend 30-40 minutes investigating each alert manually
- 68% of security teams report experiencing alert fatigue and burnout
- Organizations take an average of 280 days to identify and contain a data breach
- Over 50% of confirmed security incidents go uninvestigated due to resource constraints
This widening gap between threat detection and effective response creates significant business risk. While traditional manual incident response approaches formed the foundation of security operations, they simply cannot scale to address today's threat landscape. The solution? Incident response automation powered by AI SOC Analysts that work 24/7 alongside human SOC teams.
Understanding Incident Response Automation
What Is Incident Response Automation?
Incident response automation uses advanced technologies to autonomously detect, investigate, and remediate security threats without requiring continuous human intervention. Unlike traditional manual processes that rely heavily on human analysts, modern incident response automation leverages AI SOC Analysts, machine learning, and orchestration to dramatically accelerate response times and standardize security operations.
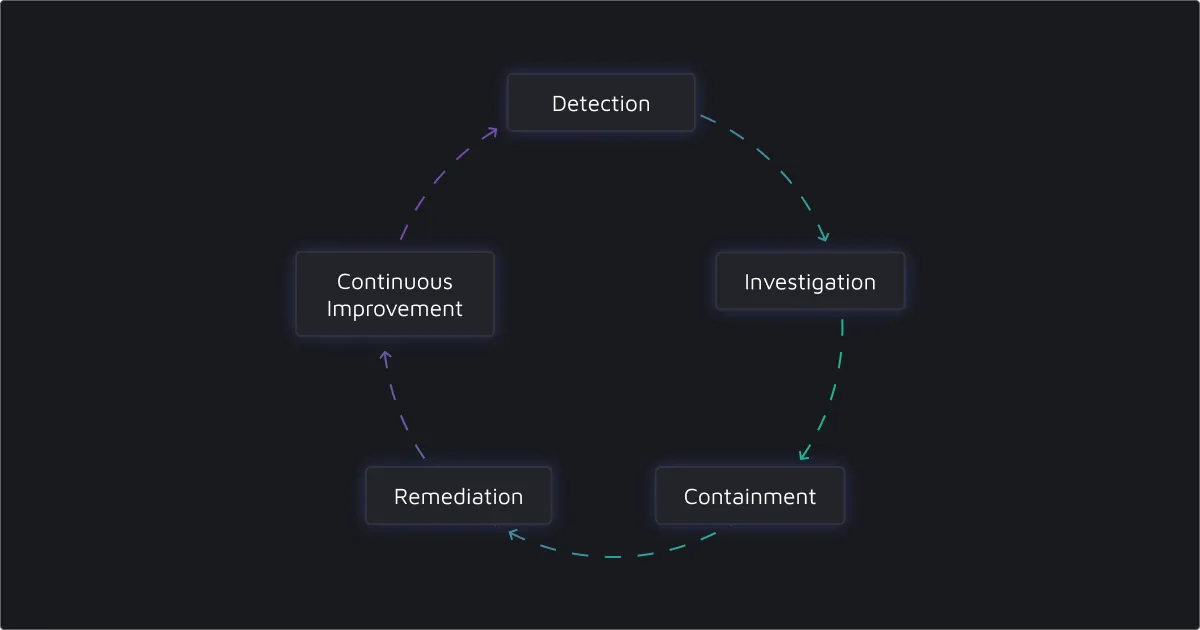
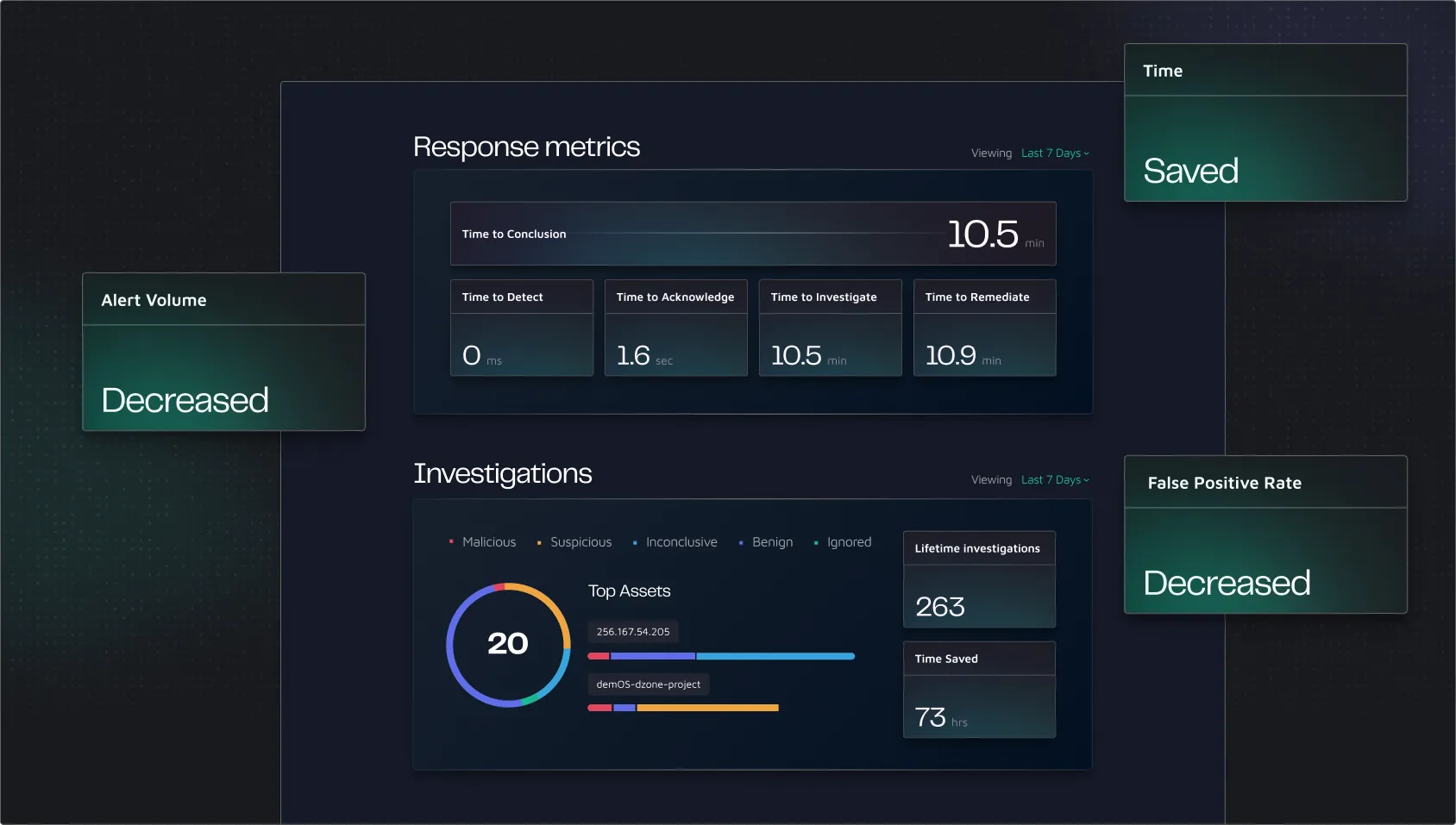
The Evolution of SOC Metrics: From MTTR to MTTC
As security automation evolves, so do the metrics we use to measure SOC effectiveness. Traditional metrics like Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) provide valuable insights but only from specific angles.
Mean Time to Conclusion (MTTC) offers a more comprehensive measurement of the entire alert triage process—from detection to final decision. Unlike MTTR, which focuses solely on incidents requiring immediate action, MTTC applies to all alerts, whether benign or potentially malicious. This inclusivity makes MTTC a more accurate reflection of SOC effectiveness.
MTTC captures every step in the alert triage process:
- Detection of a suspicious event
- Processing and acknowledging the alert
- Investigation (whether automated or manual)
- Final decision-making and conclusion
By accounting for each step from detection to final decision, MTTC provides insights into both the speed and overall efficiency of the triage process, offering a complete view of SOC performance.
Manual vs. Automated Incident Response: A Comparison
Incident response automation doesn't replace human expertise—it amplifies it. By handling repetitive, time-consuming tasks with AI SOC Analysts, automation frees security professionals to focus on strategic initiatives, complex threat hunting, and high-level decision-making that machines cannot perform.
How Incident Response Automation Works: The Core Process
Automated incident response follows a systematic approach that mirrors the cognitive process of expert security analysts but executes at machine speed. With AI SOC Analysts as the foundation, the process includes:
1. Incident Detection and Triage
The automated incident response process begins when security monitoring tools identify potential threats through:
- Anomaly detection – Identifying behaviors that deviate from established baselines
- Signature matching – Recognizing known patterns of malicious activity
- Behavioral analysis – Spotting suspicious user or system activities
- Threat intelligence correlation – Matching observed activity against known threat indicators
Once detected, AI-powered systems automatically evaluate the severity and priority of each alert, applying contextual factors such as:
- Asset criticality and potential business impact
- Threat intelligence relevance and confidence
- Historical patterns and environmental context
- User behavior analytics and risk scoring
This automated triage process eliminates the bottleneck of manual alert review and ensures that no potential threats slip through the cracks due to alert fatigue or resource constraints.
2. Investigation and Enrichment
After triage, the automated system performs in-depth investigation by:
- Gathering contextual data – Collecting relevant logs, network traffic, endpoint data
- Cross-system correlation – Connecting related events across security tools
- Threat intelligence enrichment – Adding context from internal and external sources
- Timeline construction – Building a chronological view of the potential incident
- Impact assessment – Determining the scope and potential damage
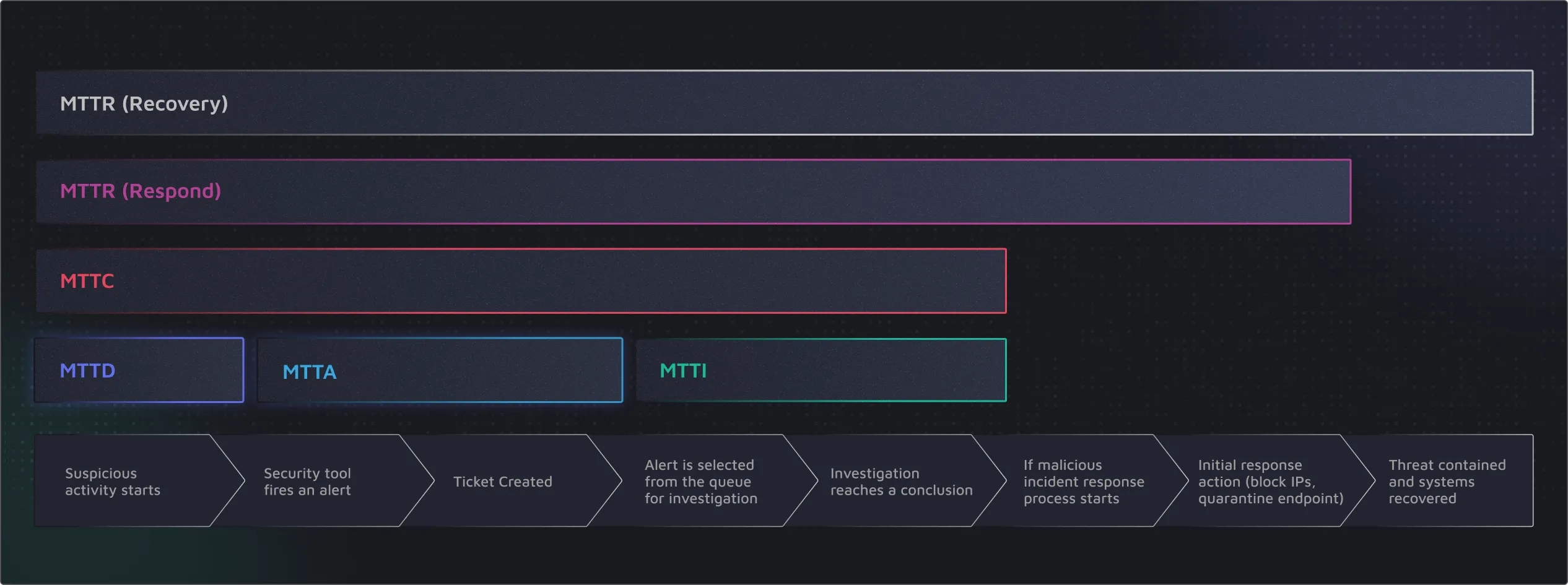
This investigation phase, which typically takes a human analyst 20-40 minutes per alert, can be completed by AI systems in seconds to minutes, dramatically reducing Mean Time to Investigate (MTTI).
3. Containment and Response
Based on investigation findings, automated incident response systems can execute predefined response playbooks to:
- Isolate affected endpoints or network segments
- Block malicious IP addresses or domains
- Revoke compromised credentials
- Kill malicious processes
- Remove or quarantine malware
These containment actions can be fully automated for known threat patterns or presented as recommendations requiring human approval for more complex scenarios, creating a hybrid human-machine approach that balances speed with control.
4. Remediation and Recovery
The final operational phase focuses on restoring affected systems to normal operations:
- Deploying patches or configuration changes
- Restoring systems from clean backups
- Implementing additional security controls
- Restarting services or systems in a secure state
- Verifying successful remediation
Automated remediation ensures consistent, thorough recovery processes that minimize the chance of recurrence while dramatically reducing mean time to remediate (MTTR).
5. Continuous Improvement Loop
Unlike manual processes that often end after remediation, AI-driven automated incident response creates a continuous improvement cycle:
- Incident documentation – Creating comprehensive case records automatically
- Pattern identification – Recognizing trends across multiple incidents
- Feedback incorporation – Learning from each response to improve future actions
- Playbook refinement – Continuously updating response procedures based on outcomes
- Threat hunting enablement – Using incident data to proactively search for similar threats
This continuous improvement loop transforms security operations from reactive to proactive, with each incident making the system more effective at preventing and responding to future threats.
Key Benefits of Incident Response Automation
1. Dramatically Reduced Response Times
Incident response automation significantly accelerates every phase of the incident lifecycle:
- Mean Time to Detect (MTTD) – Reduced through continuous monitoring and immediate alert processing
- Mean Time to Acknowledge (MTTA) – Virtually eliminated as alerts are instantly processed
- Mean Time to Investigate (MTTI) – Reduced from 30+ minutes to seconds/minutes
- Mean Time to Remediate (MTTR) – Decreased through automated playbooks
- Mean Time to Conclusion (MTTC) – Comprehensive improvement across the entire process
This acceleration transforms security operations from a race against time to a proactive stance that stays ahead of evolving threats.
2. Comprehensive Alert Coverage
Unlike manual processes that inevitably lead to alert triage and prioritization (and thus missed threats), incident response automation provides:
- Complete evaluation of every security alert
- Consistent application of investigation procedures
- Elimination of "alert fatigue" and human burnout
- Standardized documentation for compliance and analysis
- Reduced risk of overlooking subtle indicators of compromise
This comprehensive coverage closes the gap between alerts generated and alerts properly investigated—a critical vulnerability in many security operations programs.
3. Enhanced Analyst Productivity and Focus
By automating routine tasks, security teams can dramatically improve their operational efficiency:
- Analysts spend less time on routine alert triage
- Complex investigations benefit from AI-gathered context and evidence
- Security experts can focus on strategic improvements instead of repetitive tasks
- Team capabilities effectively scale without additional headcount
- New analysts become productive faster with AI assistance and standardized processes
This focus shift transforms the SOC from a reactive alert-processing center to a proactive security intelligence operation that drives continuous improvement.
4. Consistent Response Quality
Incident response automation eliminates the variability inherent in manual processes:
- Every alert receives the same thoroughness of investigation
- Response procedures execute identically every time
- Documentation quality remains consistent regardless of workload
- Compliance requirements are systematically addressed
- Knowledge is institutionalized rather than siloed in individual analysts
This consistency ensures that security operations maintain high-quality standards even during incident surges or staff transitions.
5. Improved Threat Intelligence Utilization
Automated systems can leverage threat intelligence at a scale impossible for human analysts:
- Real-time correlation of indicators across massive data sets
- Automatic incorporation of emerging threat data into detection and response
- Cross-organization intelligence sharing and collaboration
- Continuous refinement of detection and response based on new intelligence
- Pattern recognition across historical incidents and current alerts
This enhanced intelligence utilization transforms how organizations detect and respond to emerging threats, moving from reactive to predictive security operations.
Real-World Impact: Digital Insurance Company Transformation
A rapidly growing digital insurance company serving nearly 2 million customers faced significant challenges with manual alert management. Their SOC team struggled with:
- High volume of security alerts overwhelming their existing team
- Time-consuming manual investigation processes
- Need for continuous 24/7 monitoring
- Limited bandwidth for strategic security work
- Growth constraints due to fixed budgets
- High rate of false positives
After implementing AI SOC analysts, the company experienced:
- Reduced manual workload, allowing SOC analysts to focus on high-value tasks
- Substantial cost savings by eliminating the need for additional headcount
- Continuous 24/7 monitoring with no alerts missed
- Significant reduction in false positives
- Increased accuracy in threat detection
- Improved confidence in security operations
As the company's security team noted: "Dropzone saves you and your team so much time from redundant tasks that no one wants to do. It gives you an accurate analysis of data sources that you would never think of looking through. It allows you to solve critical problems that you and your team don't have the bandwidth to solve."
Choosing the Right Automation Approach: SOAR vs. AI SOC Analysts
When implementing incident response automation, organizations typically choose between two approaches:
Traditional SOAR Platforms
Security Orchestration, Automation and Response (SOAR) platforms offer:
- Playbook-based automation – Using predefined workflows and decision trees
- Integration capabilities – Connecting diverse security tools
- Case management – Tracking incidents through their lifecycle
- Team collaboration – Facilitating coordinated response
However, traditional SOAR approaches have significant limitations:
- Require extensive playbook development and maintenance
- Rely on predefined rules that can't adapt to novel threats
- Need continuous updates to remain effective
- Cannot truly reason through complex, ambiguous situations
- Demand significant engineering resources to develop and maintain
The SANS 2024 SOC Survey found that automation emerged as the top barrier to effective SOC operations, ranked higher than staffing issues, reflecting how urgent the need for more advanced automation has become.
AI SOC Analysts for Incident Response Automation
Modern AI SOC Analyst solutions like Dropzone AI offer a fundamentally different approach to incident response automation:
- Autonomous reasoning – Using AI to investigate alerts like an expert analyst
- Adaptive learning – Continuously improving through experience
- Contextual understanding – Considering organizational environment in analysis
- Minimal configuration – Working effectively without extensive playbook development
- True investigative automation – Going beyond basic orchestration
According to the ISC2 2024 Cybersecurity Workforce Study, 67% of professionals reported staffing shortages in their security teams, with budget limitations cited as the number one reason behind both talent and skills shortages. AI SOC Analysts provide significantly higher ROI for incident response automation, particularly for organizations without dedicated SOAR engineering teams.
Unlike SOAR platforms that require constant maintenance and updates, AI SOC Analysts can adapt to new threats and continuously improve their detection and response capabilities through machine learning. This represents a paradigm shift in how security teams approach automation.
The SOC Bottleneck: Traditional vs. AI Augmented
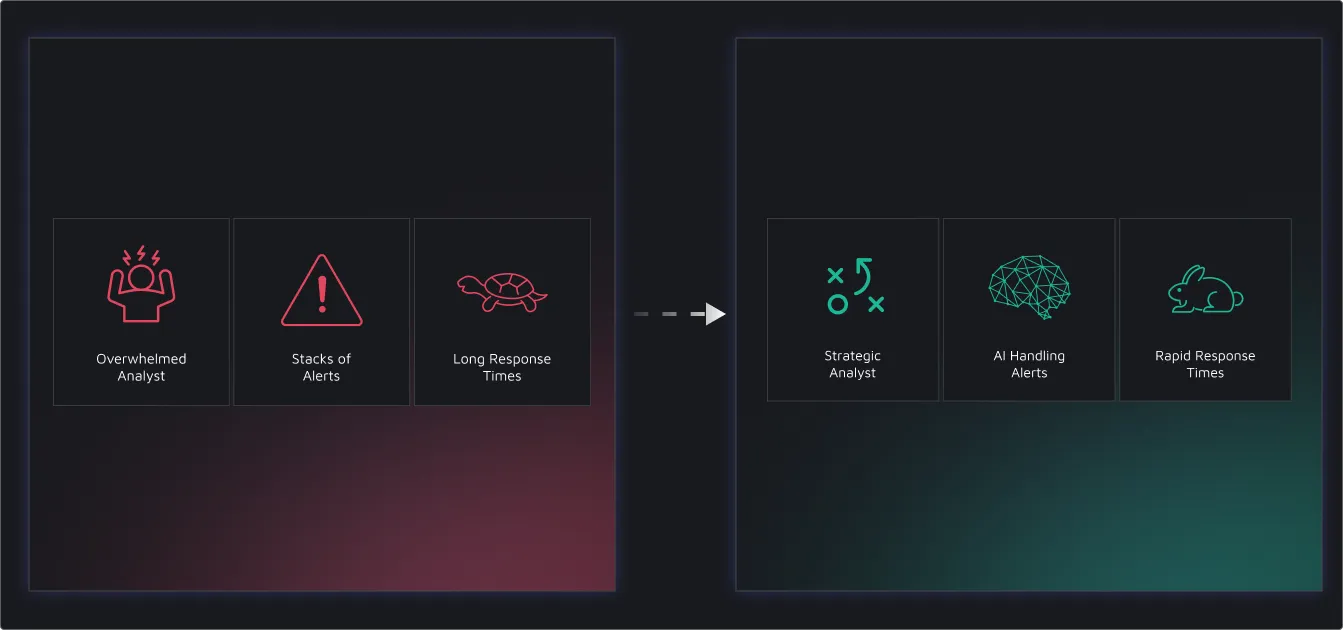
Traditional SOC Challenges:
- Manual Triage at Scale – Every alert requires a human analyst to investigate, even low-value ones
- Repetitive Workload – Analysts spend hours chasing false positives and stitching together data
- Inconsistent Depth – Investigation quality varies across staff and shift coverage
- Scaling Requires More Headcount – Growth means hiring, training, and retaining more analysts
AI-Augmented SOC Advantages:
- Automated First Response – AI handles alert triage on its own, reaching conclusions in minutes
- Analysts Focus on What Matters – Humans work on threat hunting, engineering, and response—not false positives
- Consistent, Repeatable Investigations – AI delivers structured reports every time, with context and conclusions
- Scale with AI, Not Headcount – Handle more alerts without growing headcount or burnout.
Implementing Incident Response Automation: A Strategic Approach
Successful implementation of incident response automation requires a thoughtful, phased approach:
Phase 1: Assessment and Preparation
- Document current processes – Map existing response workflows and procedures
- Identify automation opportunities – Pinpoint high-volume, repetitive tasks
- Define success metrics – Establish baseline measurements for improvement
- Evaluate technology options – Select incident response automation solutions with AI SOC Analyst capabilities
- Prepare the team – Address cultural changes and skill development needs
Phase 2: Initial Implementation
- Start with low-risk, high-volume use cases – Begin with common alert types
- Deploy in observation mode – Run automation alongside manual processes
- Validate outputs – Confirm automated investigation accuracy
- Refine processes – Adjust based on initial performance
- Document wins – Capture early successes and lessons learned
Phase 3: Expansion and Enhancement
- Increase automation scope – Add more complex use cases and alert types
- Integrate additional data sources – Enhance contextual analysis capabilities
- Implement automated remediation – Move from investigation to response
- Develop custom playbooks – Address organization-specific scenarios
- Enable cross-platform orchestration – Coordinate response across security tools
Phase 4: Optimization and Transformation
- Implement AI-driven improvements – Deploy machine learning for continuous enhancement
- Develop predictive capabilities – Move from reactive to proactive security operations
- Integrate threat hunting – Use AI SOC Analyst insights to drive proactive threat discovery
- Expand business integration – Connect security operations to business processes
- Measure and communicate value – Demonstrate ROI through improved metrics
Measuring Success: SOC Metrics That Matter
To effectively evaluate the impact of incident response automation, security teams should track these key performance indicators:
- MTTC (Mean Time to Conclusion) – Key measure of investigative capacity
- MTTR (Time to Respond) – Signals speed and workflow friction
- Escalation Rate – Insight into alert fidelity and analyst workload
- False Positive Rate – Crucial for assessing tool tuning and alert quality
- Analyst Time Allocation – Tracks shift from reactive triage to proactive tasks
- Alerts-to-Incidents Conversion Ratio – Helps assess signal-to-noise quality
According to Gartner's March 2025 report "A Journey Guide to Building a Security Operations Center," SOC maturity is a journey from reactive alert handling to proactive exposure management. Teams in the early stages benefit from tools that standardize investigations and reduce manual overhead, while more advanced SOCs look to scale without growing headcount.
Build vs. Buy: The Smarter AI SOC Analyst Path
Organizations considering incident response automation often face the build vs. buy decision. Building an in-house AI system for SOC automation can drain time, budget, and technical capacity without guaranteeing results. Teams would need to assemble ML engineers, security SMEs, prompt engineers, and LLM ops specialists to stand up a basic system, then invest months (or longer) in training, tuning, and validating it before it can reliably investigate alerts.
Pre-built AI SOC Analyst solutions offer a proven, high-impact path forward for enterprises that want AI benefits without the cost, complexity, and delay of building from scratch. Calculate your potential savings.
Conclusion: The Future of Security Operations
As the threat landscape continues to evolve at machine speed, incident response automation isn't merely an efficiency improvement, it's becoming a fundamental security requirement. Organizations that leverage AI SOC Analysts through automation gain a critical advantage: the ability to detect, investigate, and respond to threats at a scale and speed that matches modern attack methodologies.
The future of security operations belongs to hybrid human-AI teams where incident response automation handles the volume, velocity, and routine aspects of security response, while human experts focus on strategy, complex decision-making, and continuous improvement. This symbiotic relationship creates security operations capabilities far beyond what either humans or machines could achieve independently.
By implementing incident response automation with AI SOC Analysts today, security leaders can transform their operations from overwhelmed and reactive to efficient and proactive, dramatically reducing organizational risk while maximizing the impact of limited security resources.
Ready to Transform Your Security Operations?Discover how Dropzone AI can help your organization overcome the challenges of alert overload, analyst burnout, and the cybersecurity skills gap. Our autonomous AI SOC analysts work alongside your human team to ensure every alert receives thorough investigation and timely resolution. Schedule a demo today to see how Dropzone AI can enhance your security operations center and help protect your critical assets from evolving threats.
FAQs
Yes, when properly implemented. Modern incident response automation platforms operate with strict permissions, audit logging, and approval workflows for critical actions. The security risk of not implementing automation (missed incidents, slow response) typically far outweighs the minimal risk of automated response.
No. AI SOC Analysts augment human capability rather than replacing it. Security professionals shift their focus from routine tasks to strategic work, complex decision-making, and improving security posture. Organizations implementing incident response automation typically maintain or increase their security headcount while dramatically expanding their effective capacity.
Most organizations see a 70-90% reduction in mean time to respond after implementing incident response automation with AI SOC Analysts. The exact improvement depends on your current processes, alert volume, and the specific solution implemented. For high-volume alert types like phishing, the improvement can exceed 95%.
Today's advanced incident response automation solutions can handle most common security alerts, including:
- Phishing attacks
- Malware detection
- User account anomalies
- Data exfiltration attempts
- Network intrusion attempts
- Cloud security alerts
- Endpoint security alerts
The most sophisticated incident response automation platforms can investigate virtually any alert type that would traditionally require a human analyst.
Incident response automation typically strengthens compliance posture by:
- Ensuring consistent, documented response to all security events
- Maintaining comprehensive incident records automatically
- Enforcing standardized procedures aligned with compliance requirements
- Providing detailed audit trails for all response actions
- Reducing the risk of missing reportable security incidents
Most organizations find that incident response automation significantly reduces compliance effort while improving coverage.