In the daily grind of cybersecurity monitoring, distinguishing real threats from false alarms can be tricky. Each alert is like Schrödinger’s cat inside a box—you don’t know if it’s benign or malicious until you investigate. This typically takes 15-20 minutes of a human analysts’ time. Dropzone’s AI SOC analyst replicates the techniques of expert analysts to investigate each alert as soon as it hits the queue.
Process Injection: Benign or Malicious?
Recently, Dropzone’s AI SOC analyst faced a particularly tricky alert. A CrowdStrike alert indicated potential malicious activity involving process injection through a Dell installer executable. Was this a well-disguised threat actor maneuver, or simply Dell’s legitimate software update mechanism working quietly in the background? Follow along as we dissect Dropzone AI's methodology to unravel this puzzle.
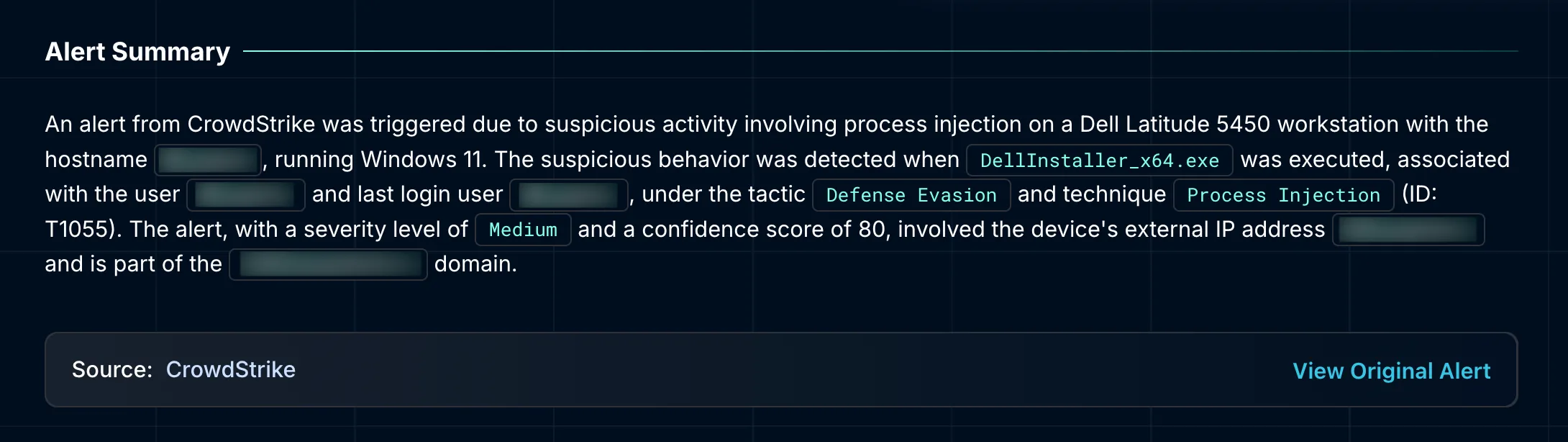
Alert Investigation Steps
The investigation started with the alert summary. Dropzone AI immediately recognized the context: a workstation running Windows 11, showing an alert involving defense evasion tactics classified under MITRE ATT&CK technique T1055, known as "Process Injection". At a glance, the alert involved the execution of a specific file named DellInstaller_x64.exe, flagged here for its suspicious activity during a silent software install.
Delving deeper, Dropzone AI examined the suspicious process details. Observing the command line arguments closely (DellInstaller_x64.exe /s /log=C:\ProgramData\dell\drivers\****\DUPLogDir 0 /appxonly), Dropzone AI interpreted these flags methodically. The /s indicated silent installation, suggesting an automated updater scenario rather than a manual user-triggered install. The detailed logging location and the use of /appxonly for restricted application-level installations further built a case toward legitimacy, albeit cautiously since silent installers could also mask malicious intent.
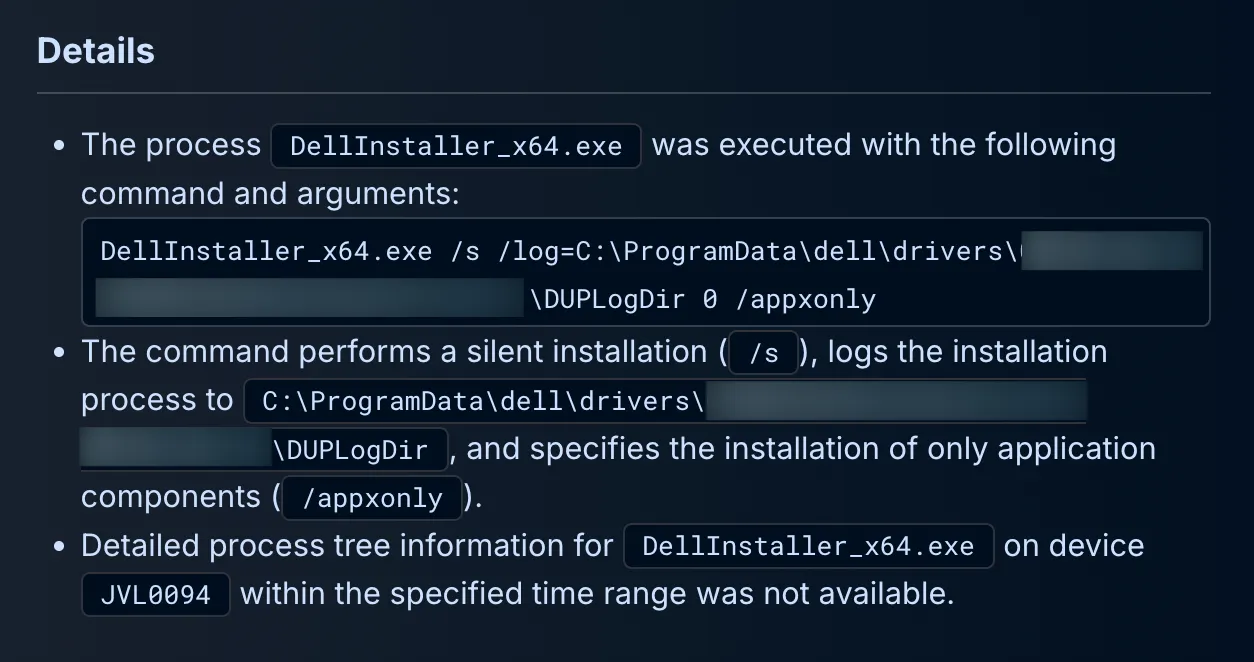
Knowing commands alone aren't proof of legitimacy, Dropzone AI then turned attention to the broader process tree. Detailed analysis revealed a standard sequence starting from common system-level processes: wininit.exe, leading to services.exe, then branching out into ServiceShell.exe, which communicated with clearly identifiable Dell domains (downloads.dell.com and dellupdater.dell.com). This network activity demonstrated routine update procedures typical of legitimate vendor software installations. The key finding that ServiceShell.exe routinely accessed these known Dell update domains over secure ports was a strong indicator of benign activity.

Curiously, the process tree included an execution of a PowerShell script launched via the command powershell.exe -ExecutionPolicy ByPass. Typically, bypassing execution restrictions could be alarming. However, contextual enrichment showed that this script was part of the legitimate Intel graphics driver update, another standardized vendor installation activity. Dropzone AI reasoned that the controlled and vendor-specific context reduced the likelihood of malicious intent significantly.
Further bolstering this assessment, Dropzone AI scrutinized file reputation data. The executable DellInstaller_x64.exe, with the specific SHA-256 hash ***2a1a49, possessed a neutral reputation and displayed a valid digital signature from Dell Technologies Inc. Comprehensive scanning from VirusTotal confirmed no malware detections in all 73 security vendor databases queried. Sandbox behavior analysis further validated the executable’s benign characteristics.
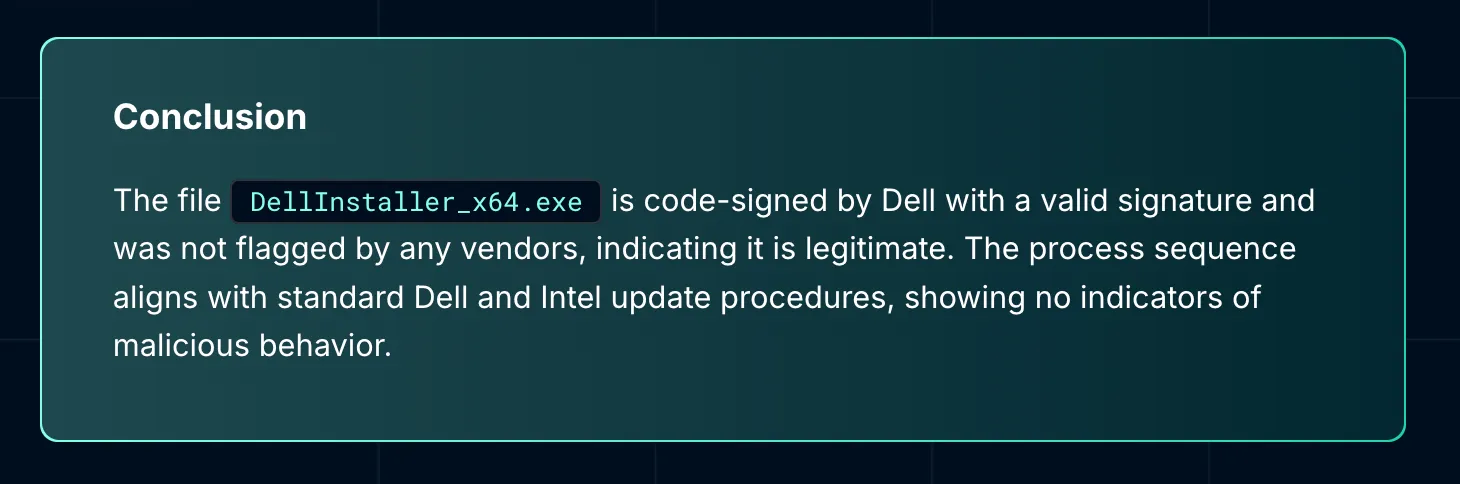
Combining all these elements, Dropzone AI concluded confidently: The file and processes in question aligned with legitimate Dell and Intel update procedures. The initial suspicion of malicious process injection activity was disproven by thorough examination of file reputation, network behavior, process commands, and reliable vendor context.
Takeaway for SOCs
Most cybersecurity alerts are not fired because you’ve been targeted by a sophisticated attacker. But the reality is that you need to do your due diligence to investigate these alerts, many of which will turn out to be false positives. Many, like this scenario involving a Dell software update, arise simply from trusted vendors performing updates with legitimate techniques that occasionally look similar to behaviors used by attackers.
Enjoyed this deep dive? Interested to see how Dropzone AI handles other types of alerts and scenarios? Check out Dropzone AI's demo gallery for alert investigations on suspicious process behaviors, privilege escalation attempts, or network anomalies! There's always something new to learn about differentiating real threats from harmless software operations.















