Executive Summary
When CrowdStrike flagged a potential MFA bypass using legacy client authentication, it appeared to be a classic security compromise. Two user accounts were authenticating via outdated "BAV2ROPC" protocols from various IP addresses, including AWS cloud infrastructure. However, Dropzone AI's investigation revealed legitimate business activity: both users belonged to a directory group named "LegacyAuthException-AuthenticatedSMTP," indicating sanctioned legacy authentication for business-critical systems. The key differentiators were consistent historical login patterns over weeks, proper group assignments, and a mix of internal and documented cloud IP addresses. This case demonstrates how context and historical analysis distinguish genuine threats from operational reality.
Introduction
Some alerts scream "breach." This one whispered it. It looked like a textbook MFA bypass using legacy client authentication. But after a fast, deep dive, Dropzone’s AI SOC analyst found that this wasn't an attack—just outdated, sanctioned behavior. Here's what tipped the scales.
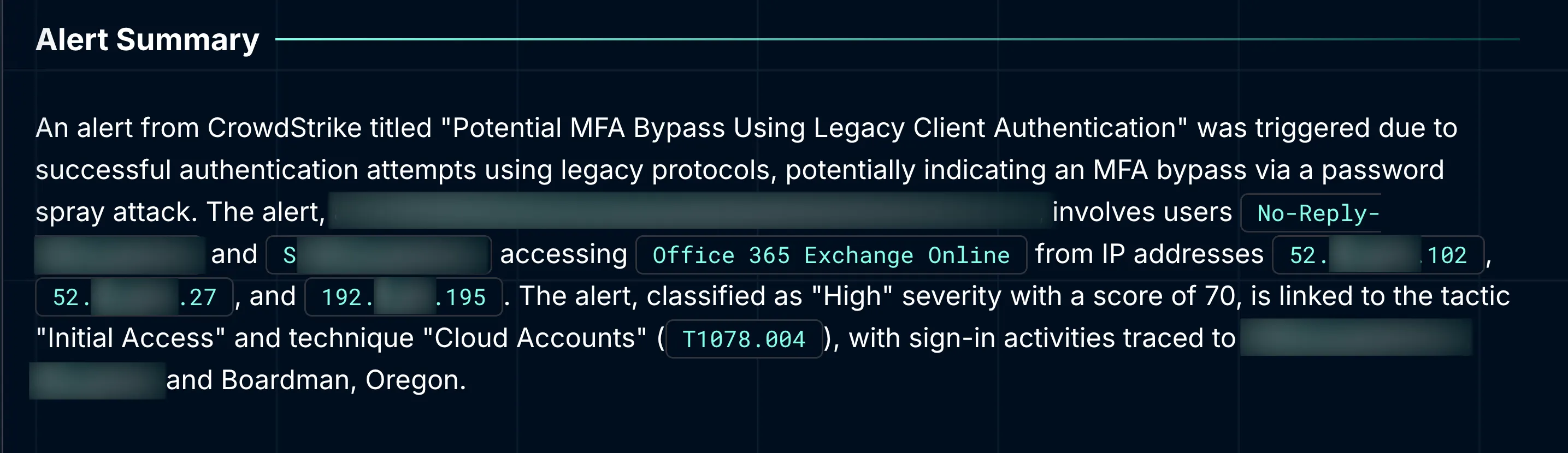
CrowdStrike flagged an incident as "Potential MFA Bypass Using Legacy Client Authentication." The alert centered on two accounts: User A (s**)** and User B (no-reply-****). The concern? Both users had successfully authenticated using legacy protocols from a variety of IP addresses. The user agent used in each case was "BAV2ROPC"—a well-known legacy authentication flow associated with Basic Authentication and Resource Owner Password Credentials.
Initial Indicators
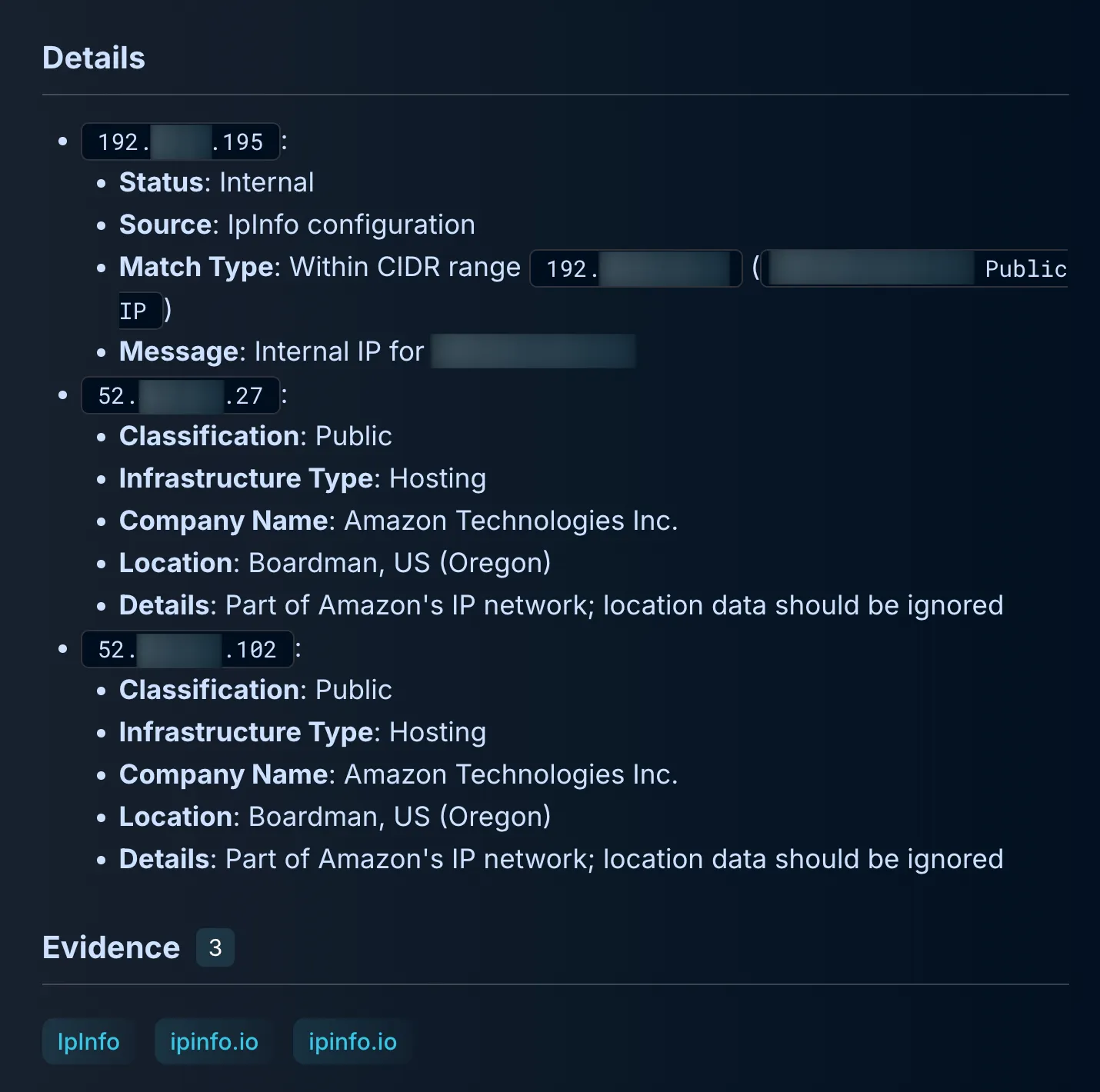
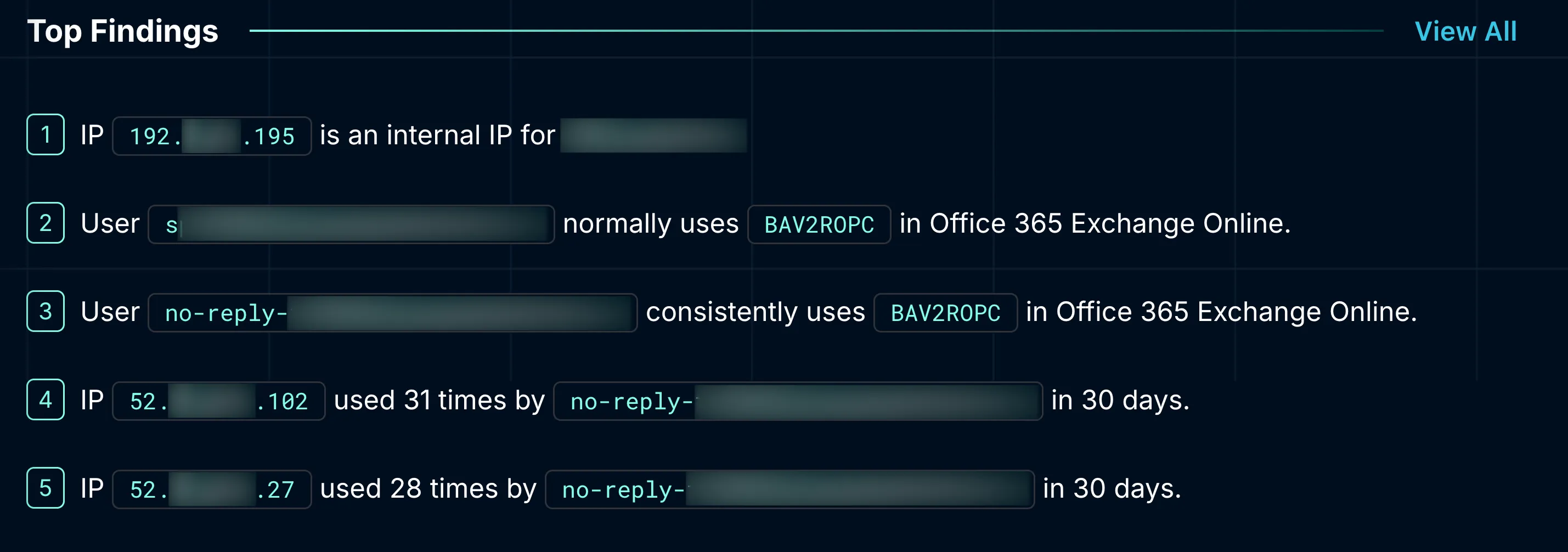
Right away, enriching the involved IP addresses was prioritized. Dropzone found the context:
- 192.X.X.195: Part of an CIDR block owned and operated by the organization.
- 52.x.x.102 and 52.x.x.27: Belonged to Amazon Web Services’ public cloud infrastructure.
On the surface, cloud-based IPs from a public provider like AWS can look risky. They're frequently abused in attacks and allow threat actors to blend into legitimate-looking traffic. But raw IP alone doesn’t make something malicious. The AI SOC analyst knew to look deeper.
What the User History Added to the Investigation
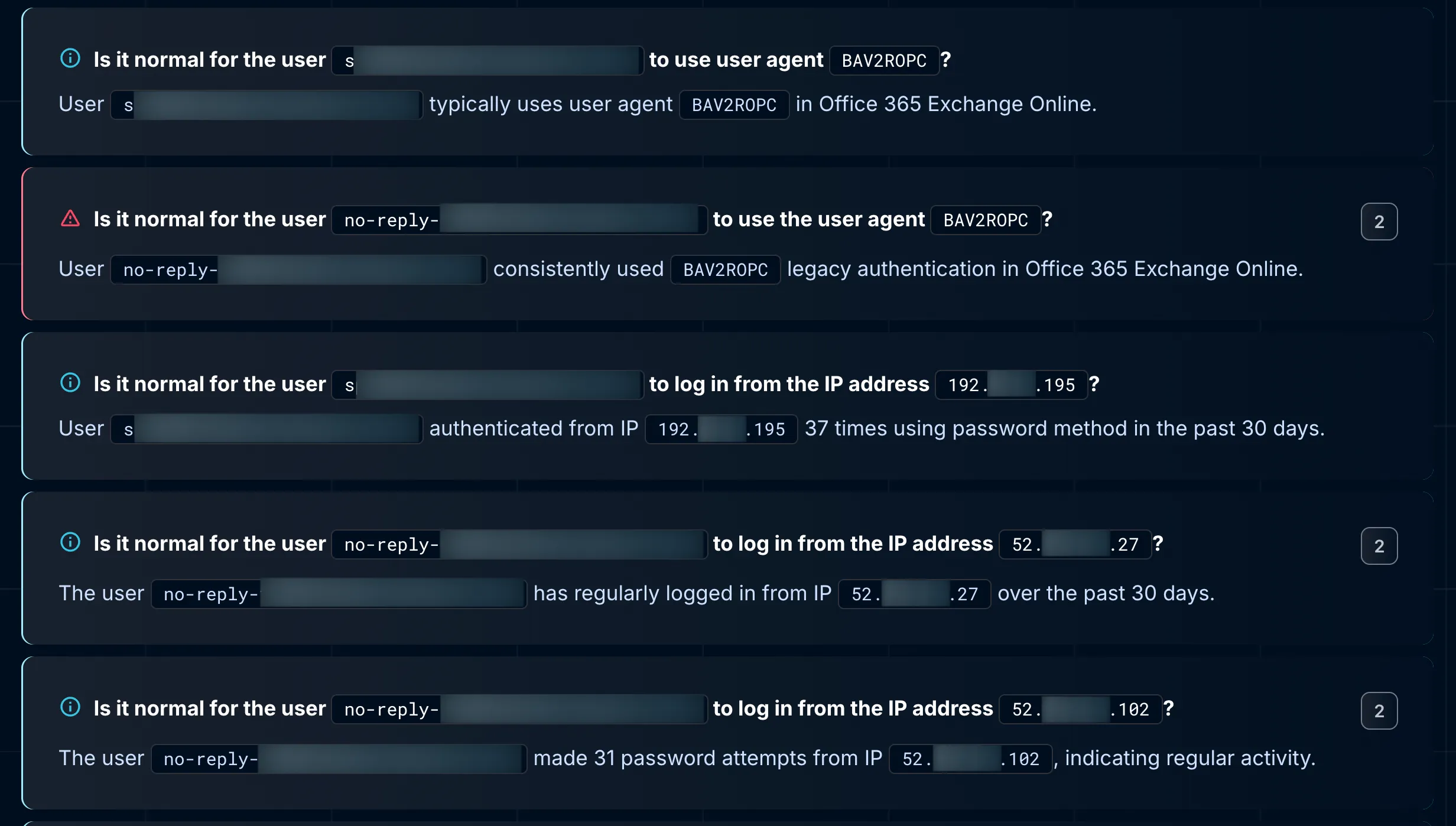
Dropzone pulled user behavior logs and began to trace patterns. The results were illuminating.
User A:
- Logged in 37 times from the same internal IP using "BAV2ROPC."
- The behavior was consistent, recurring almost daily over a full month.
User B:
- Used two separate AWS-based IPs.
- Recorded 31 logins from 52.x.x.102 and 28 logins from 52.x.x.27.
- The agent was always the same, with no sign of escalation or deviation.
If this had been a threat actor, they were behaving like the most punctual employee in the company.
The Context That Closed the Case
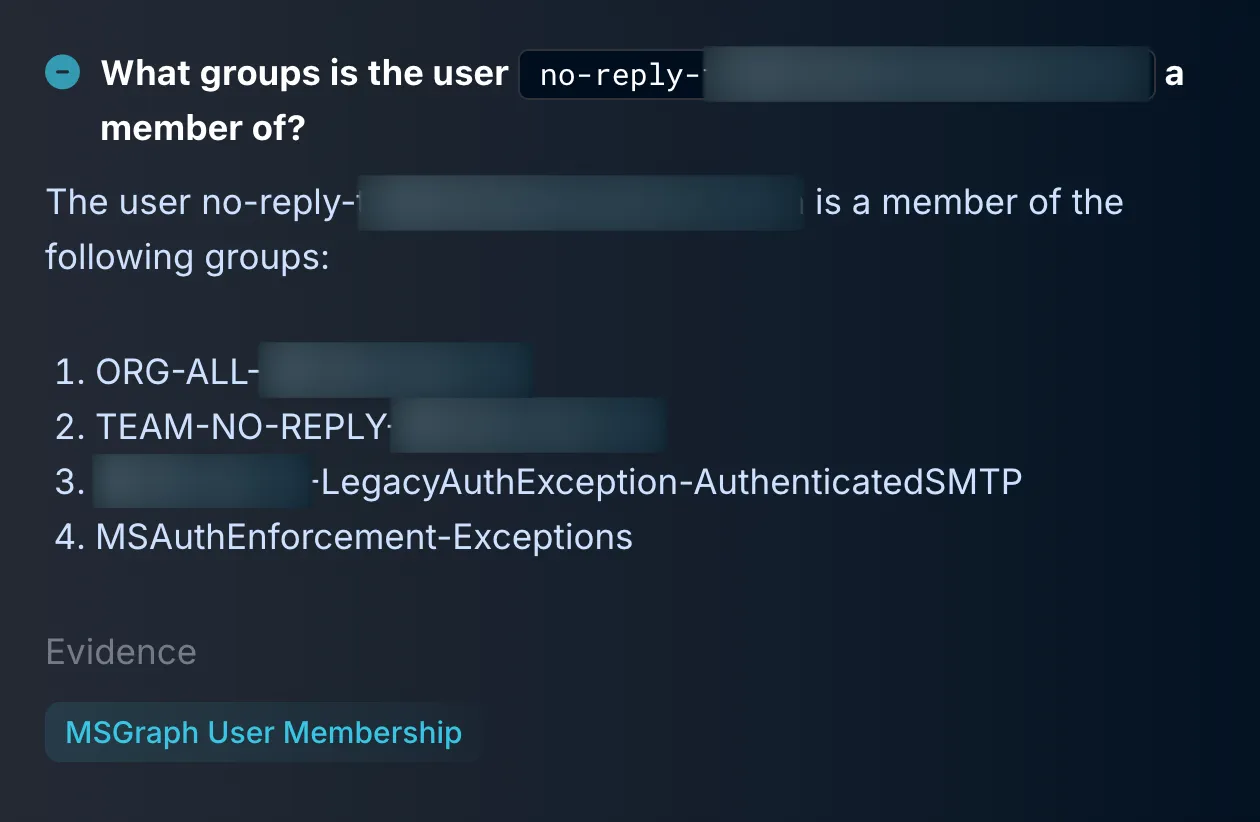
The tipping point came from user group analysis. Both users belonged to a directory group named something like ***-LegacyAuthException-AuthenticatedSMTP. That name isn’t subtle—it pointed directly to a known and accepted business exception.
These users were allowed to bypass modern authentication policies due to legacy system requirements. Likely a mail relay, scan-to-email service, or proprietary app that didn’t yet support OAuth. Yes, legacy authentication is inherently less secure. Microsoft has made clear recommendations to deprecate it. But sanctioned use of older protocols still exists in many environments, particularly those with deeply embedded infrastructure.
This wasn’t a breach. It was technical debt playing out predictably.
Analyst Takeaways
When faced with a suspicious alert, a good analyst doesn't just look for what's different. They look for what makes sense. In the above case, we can learn from the Dropzone AI SOC analyst:
- Check your groups. Naming conventions often reveal intent. "Exception" groups are worth tracking closely.
- Validate history. If a user has been logging in with the same pattern for weeks or months, the behavior is likely expected.
- Know your CIDRs. Recognizing your own IP space versus public cloud helps triage faster.
- User agent consistency matters. Yes, user agents can be spoofed, but consistent use is a valuable piece of evidence alongside other indicators. Repetition suggests routine.
Alert Investigation Verdict: Benign
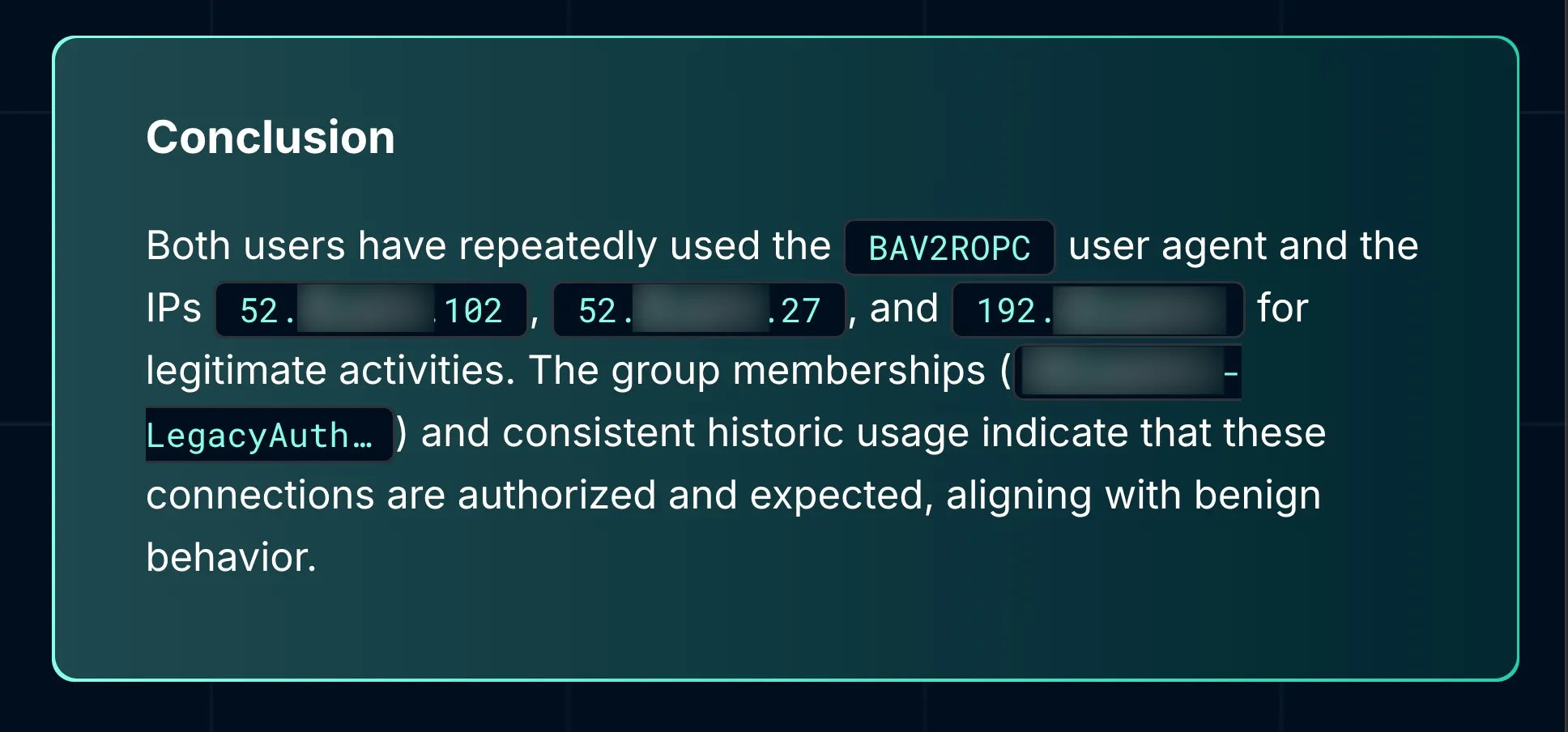
Ultimately, this alert did what it was supposed to: it surfaced something that could be risky. But during the investigation, the supporting evidence told a different story. Everything lined up—IP history, group assignment, user behavior, and organizational policy.
This wasn’t noise. It was a call to double-check policy exceptions, reassess your roadmap for modern authentication adoption, and make sure legacy paths are still being monitored. But it wasn’t a compromise.
When legacy auth is part of your reality, your context becomes your best defense.
More Investigations Like This
This case wasn’t a breach, but many others are. Knowing the difference requires experience, context, and speed. Dropzone AI brings all three to the table.
Explore the Dropzone AI Demo Gallery to see real-world investigations involving:
- Initial Access alerts
- Cloud Account Compromise
- Suspicious Login Patterns
- Abused Service Accounts
Dropzone AI helps you analyze faster, eliminate false positives, and focus on the threats that matter. Want to see more real-world investigations performed by the Dropzone AI SOC analyst? Check out these previous AI SOC Diary entries:
- Silent Threat or Software Update? Decoding a Suspicious Dell Installer Alert
- Unmasking the Relay: Navigating Alerts Triggered by Anonymized IP Services
- How Dropzone AI Cracked a Tricky VPN Logon Alert—and Why Context Matters