Phishing investigations - A chink in the armor
In this ever-evolving threat landscape, phishing is still the #1 cybercrime and a major threat to organizations. Phishing attacks have soared, a staggering 150% increase since 2019. Attack techniques are getting increasingly sophisticated with threat actors successfully impersonating legitimate companies and individuals.
As generative AI tools become more widespread, the potential for phishing attacks to become more persuasive and harder to detect is highly likely, posing a significant threat. Infact, a study in 2023 saw a 135% increase in malicious email campaigns with advanced linguistics, pronunciation and sentence structures suggesting that these threats are already here.
Protecting organizations from phishing is hard. Investigating these evasive phishing tactics and distinguishing between what’s malicious and what’s not is nuanced and takes time. But time is not a luxury that SOC teams usually have. For example, when responding to a phishing email alert analyst will typically execute this playbook.
- Examine the email - Extract the header data, inspect IP address and domain, conduct a reputation check using threat intel sources
- Examine the content of the email and any image attachments
- Run reputation analysis on embedded links and urls against threat intel sources
- Detonate/run attachments through sandbox
- Inspect users inbox, systems and assess the extent of the impact within the organization
To run this process, analysts need to log into multiple tools -secure email gateways, various threat intel feeds, open source tools, SIEM, sandboxes to name a few - often in parallel and switching between portals to extract information, collect context and enrich data. All of these steps are manual, error prone, and can be time consuming. It is estimated that it takes a SOC analyst an average of 27 minutes to manually triage and investigate a single phishing email.
Furthermore, SOC teams receive an average of 4,484 alerts daily and phishing makes up the largest portion of SOC alerts. The high volume of phishing alerts, riddled with false positives (with reported highs of up to 60% of alerts), creates alert fatigue and delays timely response to real threats. With these interconnected problems, thorough incident investigations and 100% coverage simply has remained a pipe dream for SOC teams so far.
Previously, SOC teams essentially had two choices. Hire more analysts or hire more developers to write playbooks to automate email investigations. Neither of these options are scalable. However, with recent advancements in generative AI, SOC teams can offload such analysis without hiring additional humans or writing playbooks. Generative AI systems can be trained to replicate the thought processes and techniques of analysts, help prioritize alerts, and augment the work of SOC teams.
In order to accurately and autonomously analyze phishing alerts, it is critical that the AI system meets the following key requirements:
- Pre-training: The system should be pre-trained and as a result, knows how to investigate phishing emails from day one of deployment rather than learning from human analysts after deployment.
- Extensive integrations with existing security tools: It should seamlessly integrate with customer’s existing tools so it can tap into organization-specific data, understand context and identify with improved precision.
- Human-in-the-loop: It should be built with a human-in-the-loop mindset. Transparency is key. Every single action, investigation, and deduction should be traceable to real data, not black box algorithms. The system should be able to prove its action and avoid hallucinating to maintain trust and confidence.
These above mentioned criteria is precisely what guides Dropzone’s approach to autonomous alert investigations.
Automate phishing investigations and reduce MTTR with Dropzone AI
Dropzone helps SOC teams leverage the power of pre-trained AI security analysts to perform autonomous alert investigations. The AI analysts mimic expert human analysts’ decision-making process, understand your team and company’s context, and adapt to an ever-changing threat landscape to thoroughly and autonomously investigate all alerts.
Investigating phishing email with Dropzone AI (with real life example)
This section below shows in detail how Dropzone’s AI security analyst conducts a complete end-to-end investigation flagging emails for phishing attempts and taking many steps beyond reputation checks using a real email example.
Here is an email that an employee of the company <thisisrealcompany> received that looked suspicious and flagged it. This was sent to the security team for review.
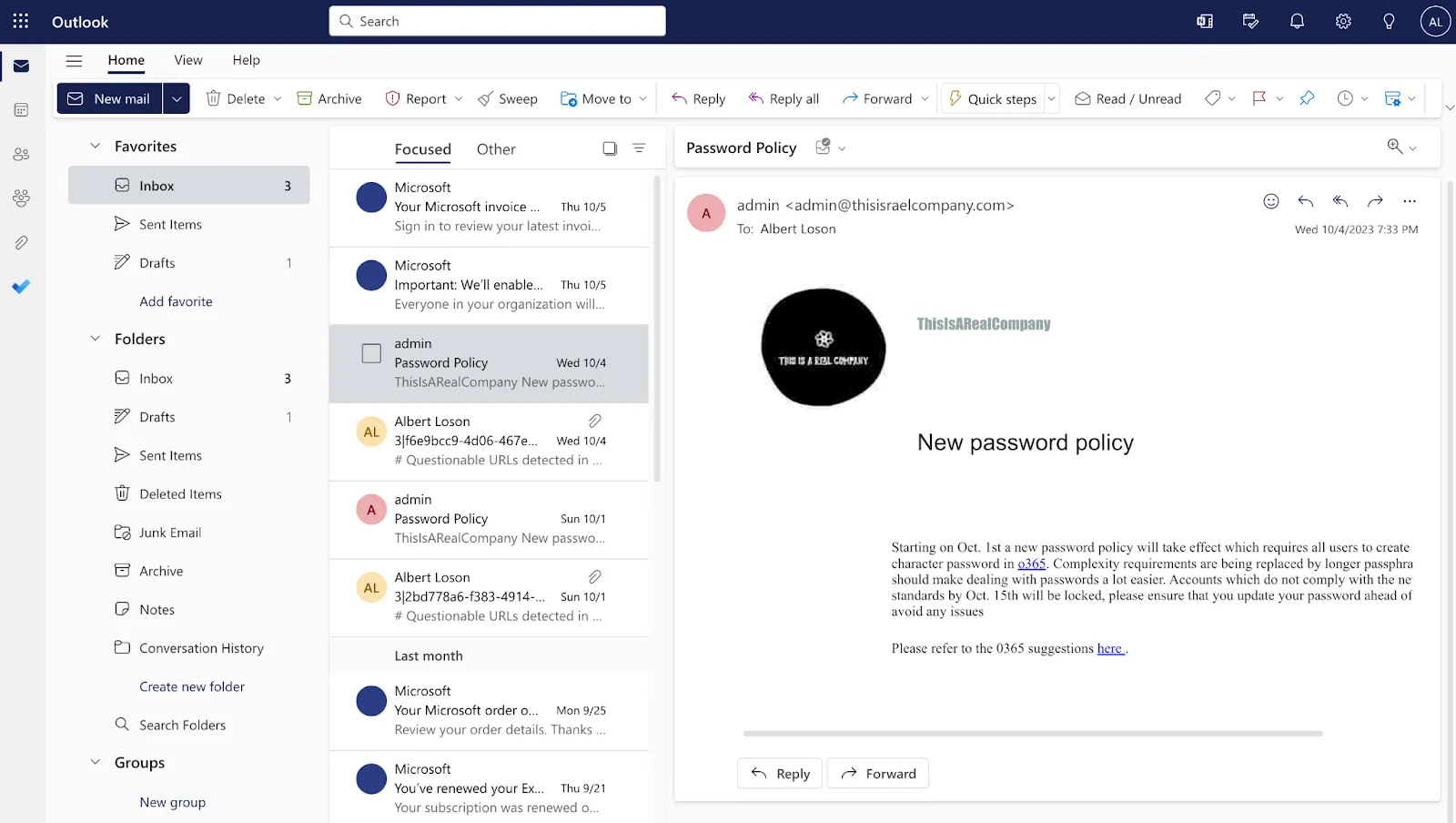
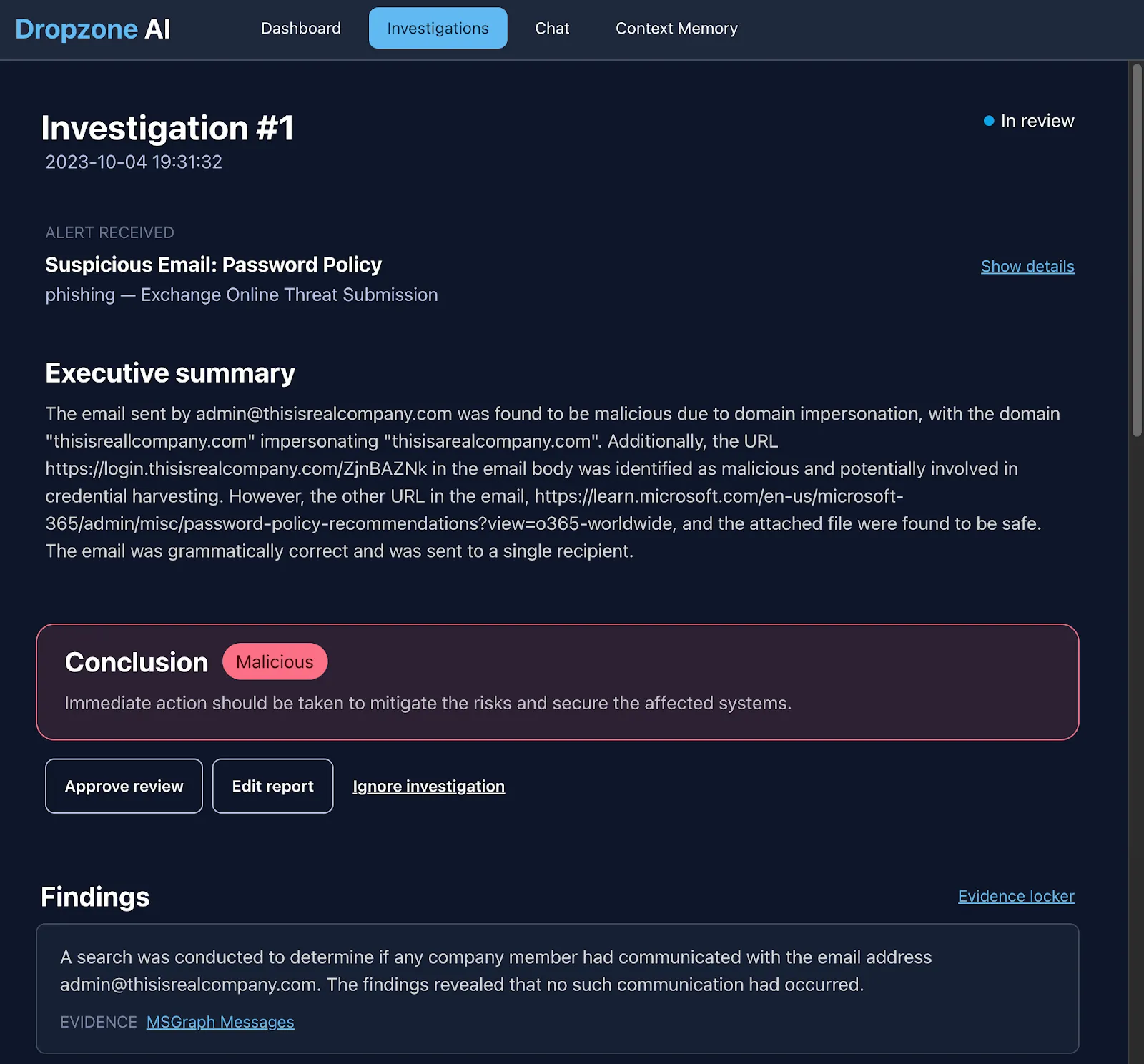
Integrated seamlessly into Exchange Online, Dropzone immediately picked up this review and conducted a detailed investigation mimicking the techniques of a Tier 1 analyst and swiftly flagged this as malicious in just 4 mins with absolutely no human intervention, clicks or playbooks. And the output is a comprehensive report, with conclusion, executive summary, and step by step process that Dropzone used to arrive at the conclusion that it is a malicious email.
Relationship analysis: First, Dropzone looked for the existence of an established relationship with this sender by analyzing Exchange Online email history of the organization.
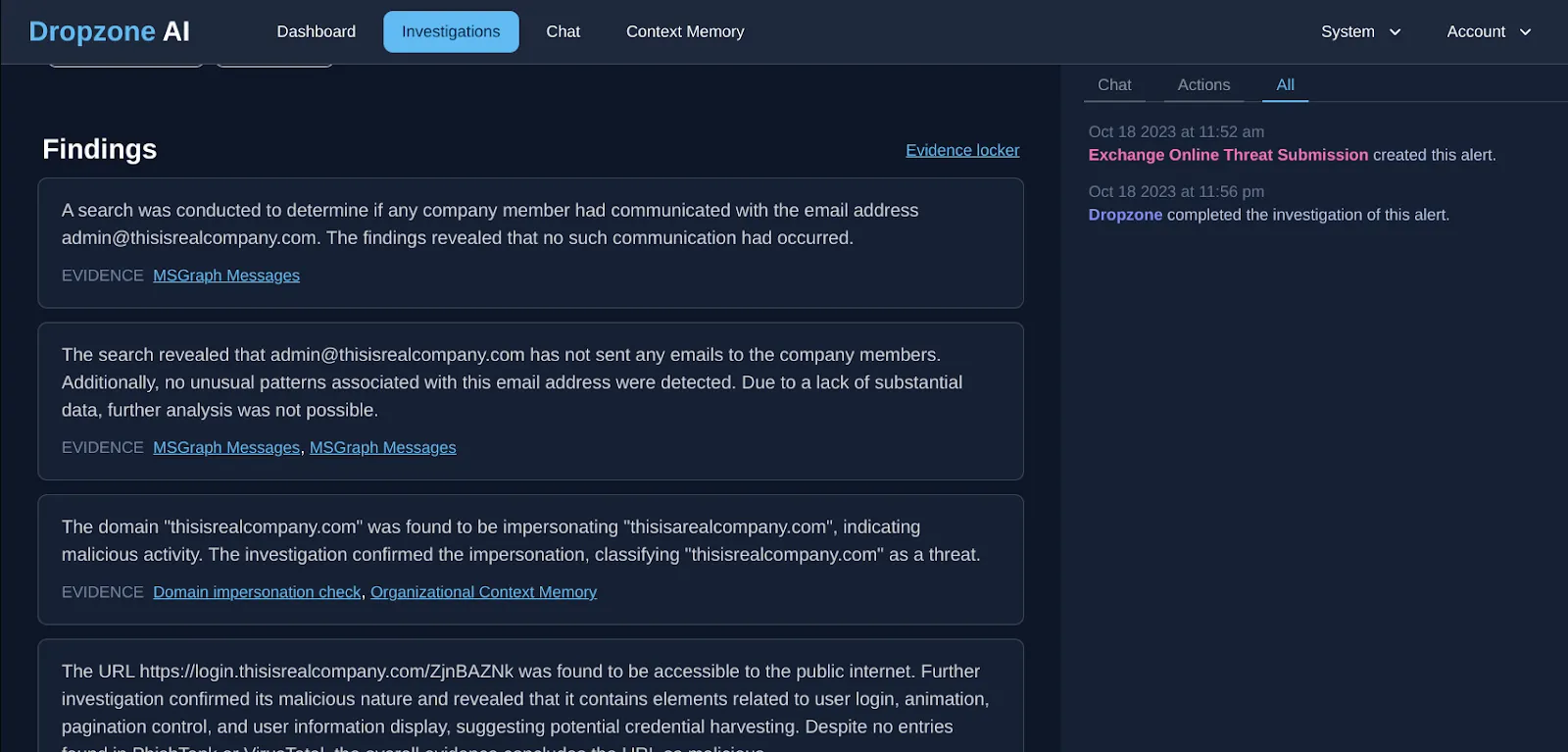
Domain impersonation analysis: Next, the system conducted a domain impersonation check and confirmed the domain “thisisrealcompany.com” impersonating with receiver’s domain name “thisisarealcompany.com” indicating malicious activity
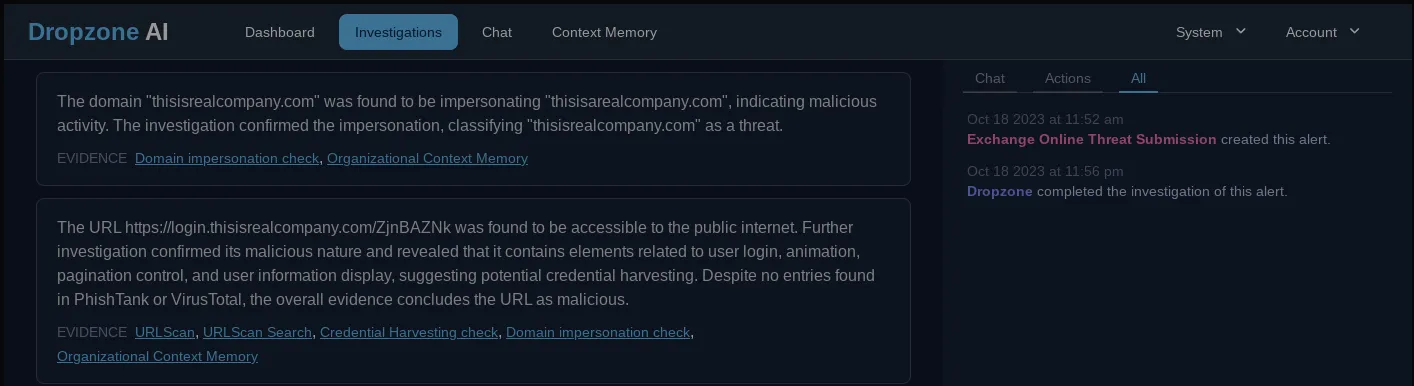
URL analysis: Then, the system conducted a URL scan that led to a login page and a detailed examination of the page that showed evidence of potential credential harvesting. Note how this URL is not known to scanning services PhishTank and VirusTotal. Since it is very common for attackers not to resume domains or URLs in targeted attacks, these are unlikely to show up on any reputation or threat intelligence sources. As a result, a traditional email analysis enrichment or AI analyst relying on these services would have missed this detail.

Attachment analysis: The system conducted a thorough attachment analysis in addition to the security vendors' analysis and investigated for factors such as contacted domains, IPs and other malicious behavior before concluding that the attached file was safe.
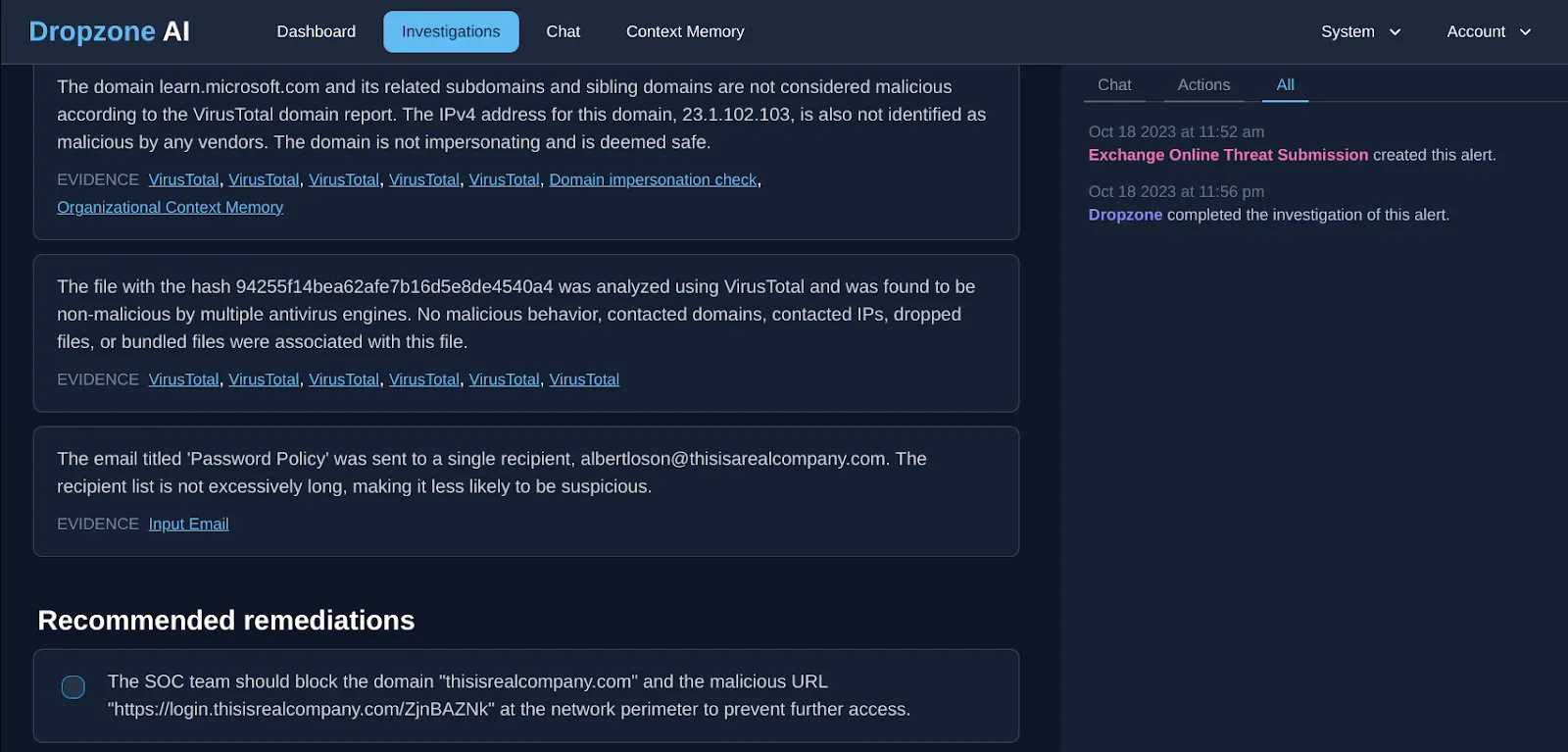
Finally, it wrapped up the phishing investigation with remediation recommendations for the SOC analyst.

All in a matter of minutes compared to a manual investigation that would have taken about 20 minutes.
What if you could make 100% alert coverage a reality?
Help your analysts reach their full potential by automating time consuming investigation grunt work and fast forward investigation time. Request a demo or take a test drive today!














