Imagine that you had a tool shed filled with top-of-the-line equipment. You could conceivably build or fix anything. The right tool for the job makes that job so much easier, but it also helps if you are familiar with how to use that tool. The best tools won’t help unless you have the expertise to go along with them. Similarly, when analyzing security alerts, analysts are faced with a wide range of data sources that could contain relevant information to aid in the investigation. And each of these investigations requires specific types of data. Some examples:
- “We suspect someone has stolen credentials for an AWS IAM user and need to analyze access.”
- “We’re analyzing some phishing activity. What URLs did this email alias click on within the last five weeks and what IPs did they resolve to?”
- “What’s our exposure to a new exploit that uses the Remote Desktop Protocol (RDP)?”
- “We have some intelligence from our ISAC that includes some IoCs and need to hunt for them in our environment.”
- “Our EDR detected command-and-control malware on this endpoint and we need to investigate network activity.”
To get answers, security analysts need to know which data source contains relevant information, and how to extract the necessary information from a number of fragmented tools and data sets. For example, in any particular investigation, a security analyst may need to investigate network traffic using VPC flow logs, correlate process hashes by referencing our threat intelligence platform, run device forensics using EDR, look up user data using Okta, or query AWS CloudTrail logs using the AWS CLI.
All this takes time, especially if you’re unfamiliar with the tools (or even a bit rusty). No one is an expert at everything, and often the only time many staff touch their security tooling is when there’s an incident, so it can be hard to remember all the ins and outs! There’s the problem of getting the data—remembering the query syntax and the data schema—and then being able to interpret the results. No one enjoys scrolling through pages of packets in Wireshark. And it’s worse when you need to correlate data from multiple log sources to reconstruct what happened. Finally, these can sometimes be stressful situations where answers are needed urgently. Time is of the essence!
AI SOC Analyst Has Entered the Chat
The Dropzone AI SOC Analyst chatbot was designed to help security analysts quickly field unpredictable, ad hoc security investigations. The chatbot enables human analysts to use natural-language queries that synthesize data from multiple security and IT tools to quickly get answers.
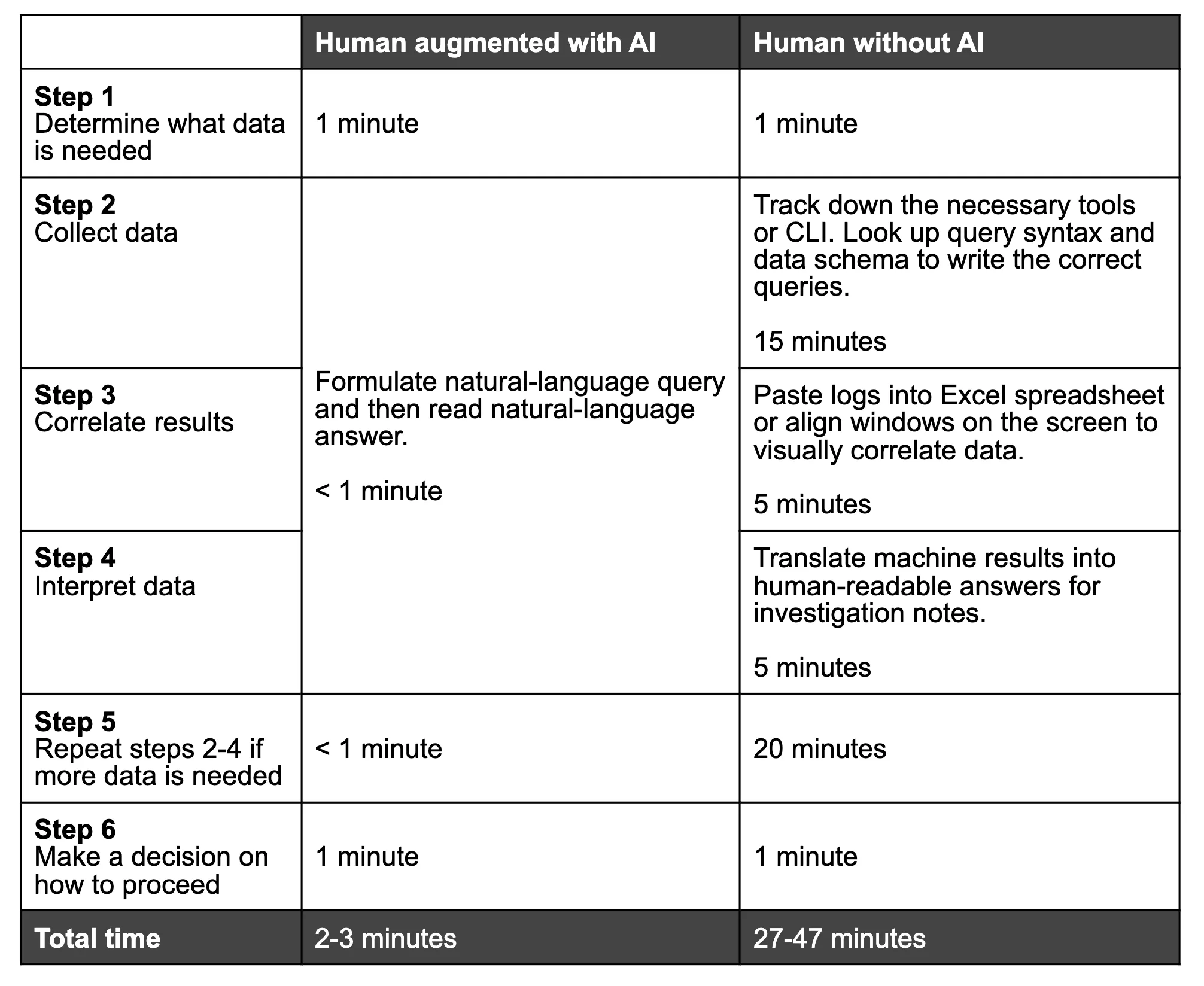
Let’s compare the time required for an AI-augmented workflow with a traditional workflow:
The AI Analyst chatbot is one feature of the Dropzone platform, which augments SOC teams enabling them to do more, faster. Dropzone can do initial triage of alert queues, speed up incident response, and lower the barrier for threat hunting.
Want to see what it looks like? Take the tour (previewed below), showing how the AI Analyst chatbot generates Splunk queries and then summarizes the results.
How Agentic AI for the SOC Works
Unlike scripts and pre-built queries, our AI SOC Analyst is designed to handle a wide variety of investigative questions without any pre-programming. It connects to APIs for your internal tooling, such as the Active Directory, AWS CLI, ServiceNow, and Splunk; can query public threat intel tools such as VirusTotal; and also knows how to use open-source tools like NMAP and Wireshark. The AI adapts to data available in your systems, such as learning the schema of logs under different Splunk indices.
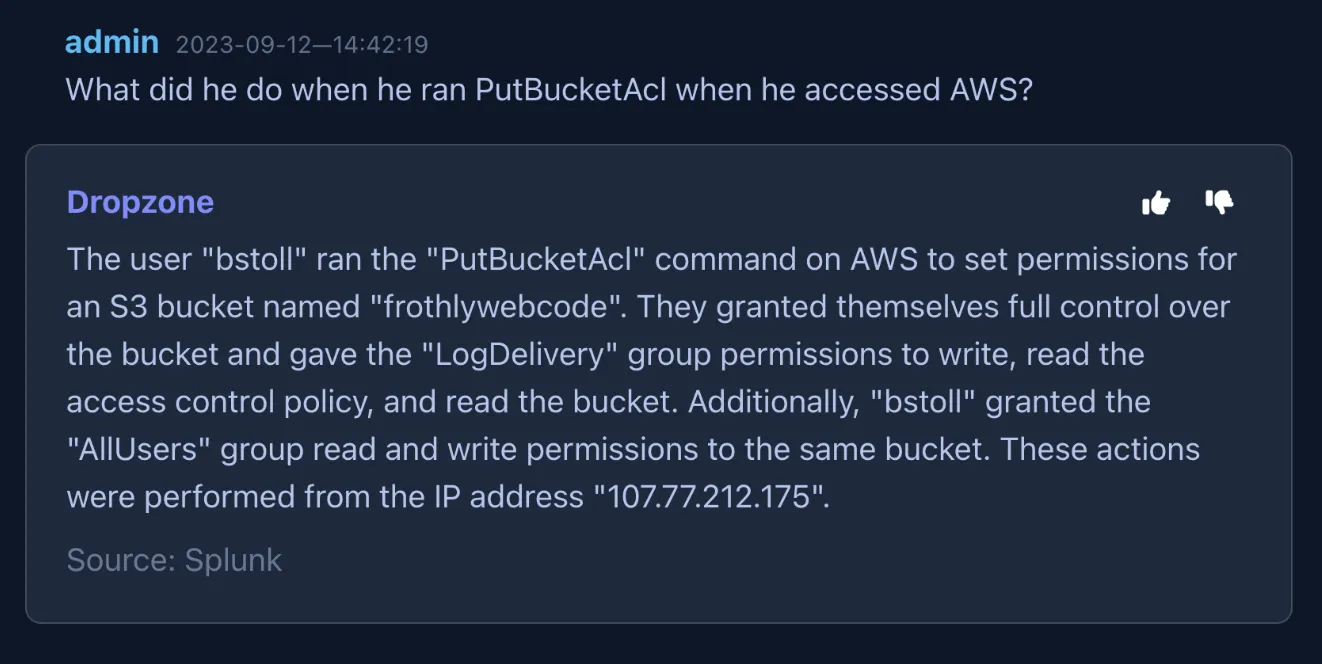
When you form a query, the AI Analyst chatbot knows what data resides where and how to sequentially pull the appropriate data. The chatbot parses the results (which can be quite voluminous) and formulates a succinct natural language response. In the screenshot below, you can see how the chatbot is able to parse a PCAP to enumerate the details of a SQL injection attack.

Improve the Analyst Experience, Improve your Security
Offloading the technical hows of data gathering and comprehsnion can help alleviate some of the stress that analysts feel, especially in high-stakes situations. The reality is that your analysts cannot be expert at everything. It can be difficult to remember the ins-and-outs of each tool—the query syntax, the data schema, and then having to parse the results. The Dropzone AI Analyst chatbot can dramatically cut the time required for each unplanned, ad hoc investigation. Say that each analyst on your team spends two hours each day collecting and synthesizing data for investigations, and that the chatbot can reduce that effort by 75%, that would be 7:30 hours saved each week, or 30 hours a month.
Saving time means:
- Higher quality alert triage - Your analysts can cut through their alert queues faster without cutting corners. Dropzone AI can improve the level of detail and consideration given to each case.
- Faster and more accurate incident response - Analysts are able to quickly gather the relevant data to understand the scope and severity of an incident—quickly arriving at the actions needed for containment and remediation.
Isn’t Every Vendor Building a Chatbot?
Unlike other security chatbots, the Dropzone AI Analyst chatbot works excellently across security tools and datasets from different vendors, including open-source tooling. You don’t want to be working with five different chatbots! Dropzone can integrate with vendor-specific chatbots or the underlying APIs to collect the needed data in the correct sequence and then synthesize the results.
Dropzone AI is also more flexible than traditional playbook-based automation, which is constrained to the tasks that you knew to program ahead of time. Analysts’ real-world tasks are varied and most times there is no playbook that works. The AI Analyst chatbot can help with these one-time tasks that you probably don’t need to write a script or saved query for.
Want this for your SOC? Request a demo or take a test drive.
.webp)