Dropzone AI + Splunk Integration: Automate Alert Investigations
Why Dropzone AI
Why Automate Splunk ES Investigations with Dropzone AI
Investigate every Splunk detection in minutes
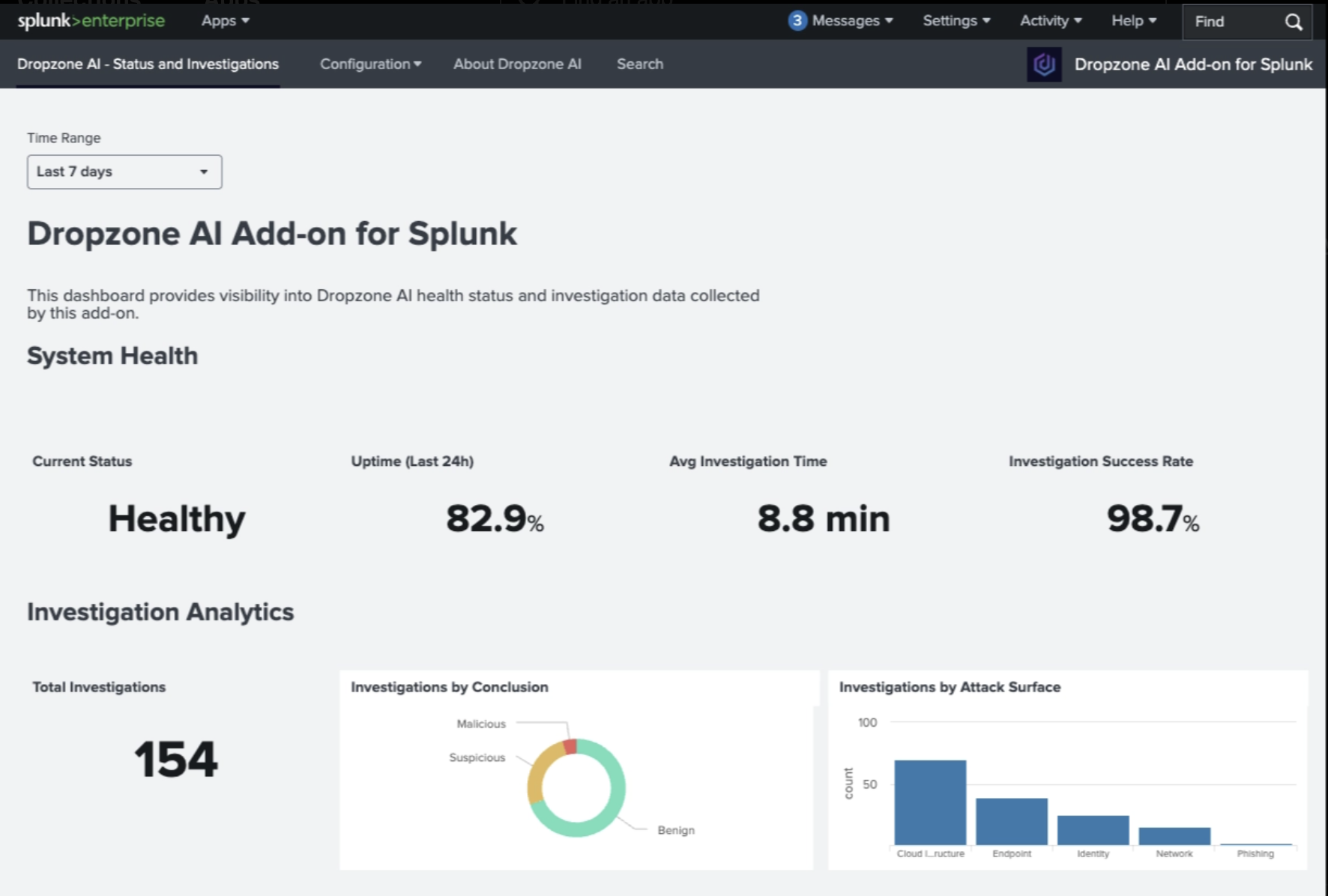
Dropzone AI integrates directly with Splunk Enterprise Security (ES) to automate security alert investigations, reducing Mean Time to Conclusion (MTTC) by 90%. Every Splunk detection receives autonomous investigation within minutes.
Unlike generic AI SOC tools, Dropzone is purpose-built for Splunk through integration with the Common Information Model (CIM). It uses optimized queries and learns your team's specific CIM usage, adapting to your indexes, macros, and query structures without impacting Splunk performance.

Speed up Mean-Time-to-Conclusion (MTTC) with AI automation.
The Dropzone AI SOC analyst immediately starts investigations when alerts hit the SOC queue, delivering conclusions in minutes. Our integration is configurable to your environment, fine-tuning which indexes to query, which macros to use, and query structure (vital because every enterprise uses Splunk uniquely).
Dropzone continuously learns your patterns, investigating alerts the way your expert analysts do. It seamlessly integrates with Windows Event Logs, Okta, AWS CloudTrail, and other data sources to gather context for investigations. Finally, teams can quickly investigate 100% of their alerts.
Automated Splunk ES Investigation: Real-World Example
Step 1
Alert Detection:
Splunk detects a potentially malicious PowerShell process execution and sends the alert to Dropzone AI for triage and investigation.
Step 2
Hypothesis Formation:
Dropzone formulates a hypothesis, as a human analyst would, then determines investigation steps. Using Splunk's CIM and optimized data model queries, it efficiently gathers relevant context.
Step 3
Contextual Analysis:
The AI SOC analyst investigates the user who initiated the script, discovering they are a developer. The investigation also reveals Git operations consistent with developer activity.
Step 4
Threat Assessment:
Performance-optimized Splunk searches find no calls to external sources to initiate the script (a key malicious indicator).
Step 5
Conclusion:
Dropzone concludes the alert is a false positive, saving SOC time. Investigation details are stored in Context Memory.
Step 6
Step 7
Complete Alert Coverage:
Every Splunk alert receives rigorous investigation automatically through purpose-built integration.
Instant Investigation Response:
Investigations start immediately via Splunk's REST API, shrinking MTTC by 90%.
Optimized for Performance:
Dropzone leverages Splunk's CIM and data models for cost-effective queries, preventing dangerous searches.
Configurable to Your Environment:
Fine-tune indexes, macros, and query structures to match your Splunk usage with continuous learning.










