Introduction
AI is transforming how security teams operate, especially inside the SOC. Tasks like alert triage, enrichment, and context gathering are being handed off to machines, and that shift is helping teams reduce burnout and move faster. But as automation becomes the norm, there’s a growing gap in how junior analysts get trained. When entry-level tasks are no longer manual, where does early-career talent build real investigation experience? In this article, you’ll learn why AI shouldn’t just be a force multiplier for speed, but also support the next generation of analysts by becoming part of the mentorship model.
Key Takeaways
- AI automation creates a training gap for junior analysts
- COACH by Dropzone AI provides real-time mentorship during live investigations
- COACH is a free Chrome web browser extension that augments human mentor relationships
- Teams see 70% faster analyst onboarding with AI guidance
- Zero data retention ensures enterprise security compliance
What is AI-Powered SOC Training?
AI-powered SOC training uses artificial intelligence to mentor junior security analysts during real alert investigations. Without replacing human learning, AI tools provide:
- Real-time explanations of why alerts triggered
- Guided investigation workflows with best practices
- Context from past investigations and attack patterns
- Instant answers without waiting for senior analyst availability
This approach helps analysts learn 3x faster while maintaining operational efficiency.
Automation Is Real — But So Is the Need for a Talent Pipeline
AI is starting to do the heavy lifting in many SOCs now, it’s sorting low-fidelity alerts, enriching telemetry, correlating context across tools, and closing out false positives faster than humans can.
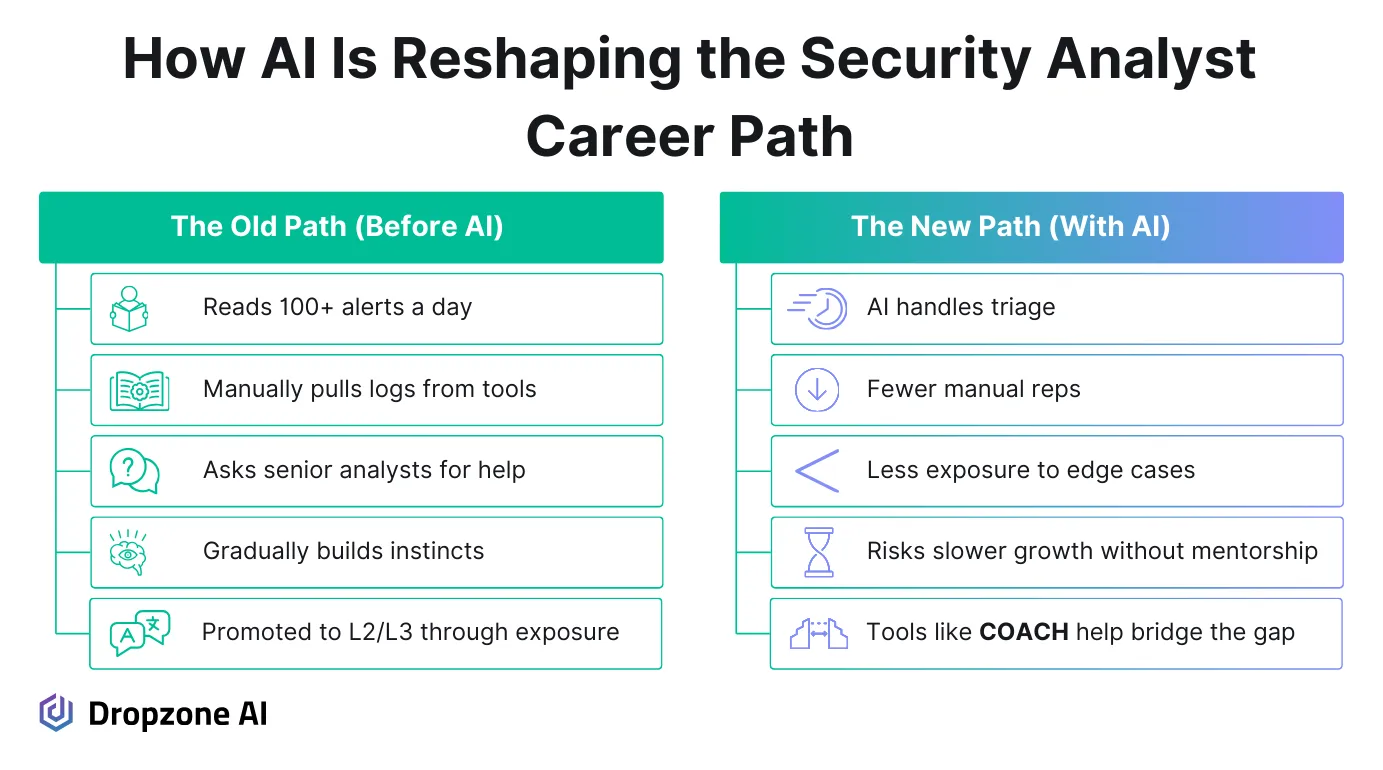
That’s been a win for speed and scale, especially when teams are short-staffed or manage large environments. But here’s the catch: Junior analysts used to do that exact work type of Level 1 or Tier 1 triage work. Without it, they miss the hands-on exposure that builds technical confidence.
Before AI automation, early-career analysts were reading raw logs, pivoting through EDR timelines, mapping user behavior in identity systems, and slowly learning how to separate noise from signal. They weren’t just teaching tools but developing pattern recognition, asking shrewd questions, and getting familiar with edge cases that don’t appear in training materials. That kind of experience compounds over time. When it disappears from day-to-day workflows, it’s easy to lose track of how someone goes from L1 to L3.
Security leaders can’t ignore this gap. If new analysts don’t have access to the messy, repetitive side of detection and triage, they won’t be ready when it’s time to step into incident command, tune detection logic, or lead threat hunts.
The reality is that we still need people who can operate under pressure, understand the systems behind the alerts, and reason through gray-area decisions. Automation can speed things up, but it doesn’t replace the need for real technical skills growth. We need to build systems that support both.
AI Can Be a Mentorship Layer — Not Just an Automation Engine
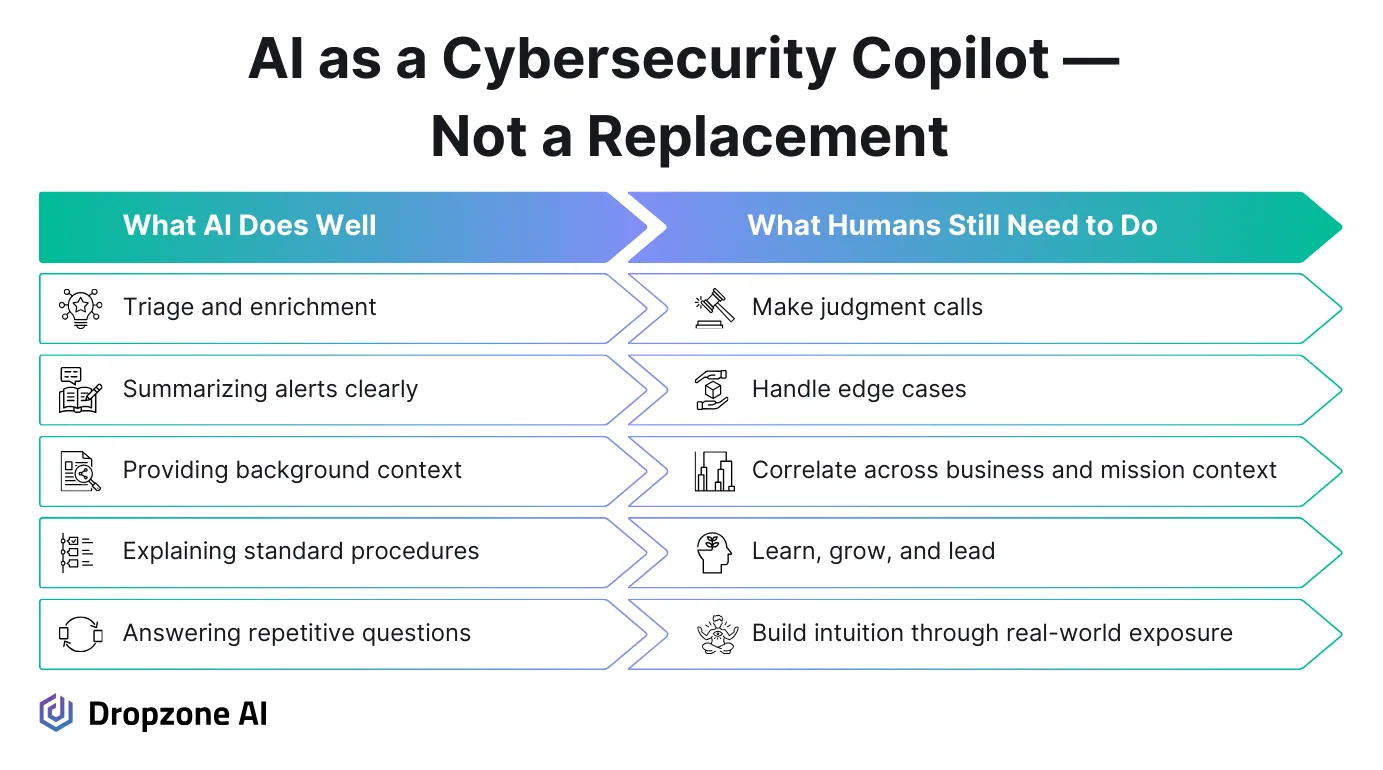
AI doesn’t have to replace people; it can help them grow faster. When integrated thoughtfully, AI can provide ongoing support for junior analysts by offering context, guidance, and real-time feedback. Rather than simply handing off tasks, AI can explain why a specific alert was triggered by referencing past investigations, identifying attack patterns, and correlating telemetry from SIEM, EDR, cloud, and identity tools, so junior analysts learn in the flow of work. It’s like getting investigative coaching embedded directly into the workflow.
This kind of AI interaction matters, especially for newer team members still building their investigative instincts. Instead of waiting for a senior analyst to be available or skipping the question entirely, they can query the AI to understand an alert and receive guidance. That level of access helps remove friction from the learning process without slowing down the broader team.
Over time, this builds technical confidence and autonomy. Junior analysts can ramp up faster because they engage with real incidents while getting structured input. It’s a way to scale knowledge transfer without requiring constant 1:1 mentorship. The work still gets done, but the analyst walks away with more understanding than they had before. That’s how we create depth in the pipeline by giving newer analysts the right support while doing the job.
Meet COACH - An AI Mentorship Tool for Junior Analysts
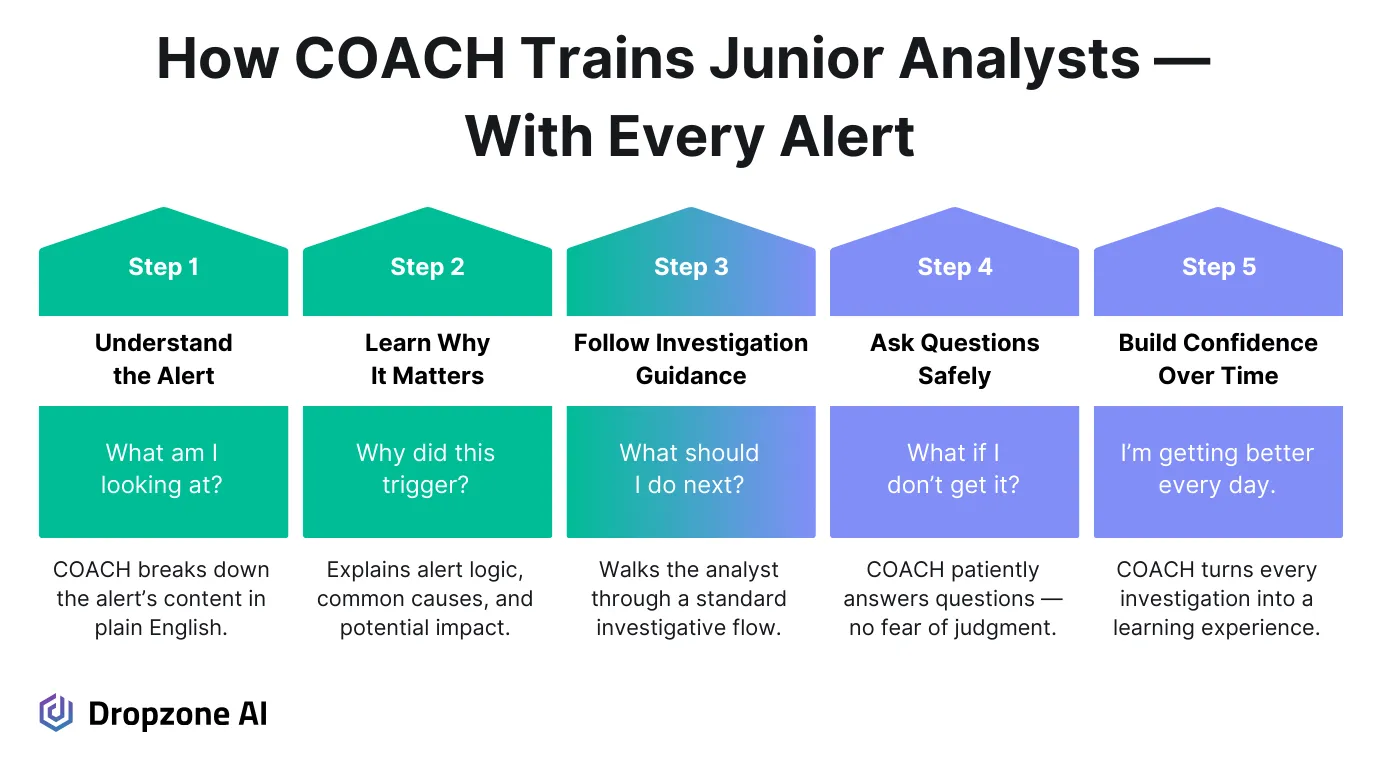
COACH by Dropzone AI is a free Chrome extension built for security analysts who are still building their skills and confidence. It provides advice on the alerts you're already working on, whether from GuardDuty, CrowdStrike, or other sources, and walks you through them in real time.
COACH explains the alert, clarifies why it was triggered, and walks analysts through the investigation process. The free web extension offers hypothesis on why an alert might be malicious or benign, and guides them with next steps for investigation. This breaks things down clearly without oversimplifying, helping you better understand real-world incidents as they unfold.
The free web extension is built around a repeatable investigation methodology that helps analysts move from signal to decision more clearly. It walks you through common steps like separating false positives, reviewing context from linked telemetry, and identifying potential escalation paths. It gives you structure without hand-holding and doesn’t require custom setup or backend access. It has zero data retention, so it’s safe to use without worrying about leaking sensitive data.
Security leads appreciate COACH because it lightens the mentorship burden without lowering the bar. It accelerates onboarding, reinforces good investigative habits, and helps junior analysts start contributing faster. Instead of waiting months for people to gain fluency, teams get earlier traction and more consistent skill development while focusing on actual alerts.
Oh, did we mention that it’s free?
The Impact of AI-Powered Training
By the Numbers:
- 10,000+ daily alerts handled by modern SOCs
- 70% faster analyst onboarding with COACH
- 3x improvement in investigation accuracy for junior analysts
Conclusion
Security teams don’t just need more automation; they need a smarter way to build and retain analyst talent in parallel. That’s where tools like COACH help organizations use AI to teach, not just automate, to give junior analysts real-world experience without overwhelming senior staff or slowing operations. Dropzone AI is building toward that future, where every alert is both a response opportunity and a learning opportunity. What are you waiting for? Download it now and give it a try.