Key Takeaways
- Dropzone pre-trains agents on each SOC's environment mapping schemas, learning queries, and adapting to unique deployments.
- Agents practice investigative workflows, including tracing processes, correlating SIEM and identity data, and refining queries when answers fall short.
- The architecture is vendor-agnostic and secure, so agents operate across mixed environments, just like humans.
Introduction
Security teams are well aware of the problem: SOCs are inundated with alerts, and the challenge isn't a lack of data; it's determining which alerts are significant and investigating them effectively. What separates a quick dismissal from a serious escalation is the ability to reason through evidence, not just collect it.
In this article, we walk through how the Dropzone AI SOC analyst investigates a suspicious login, from the initial alert to forming hypotheses, gathering and interpreting evidence, and finally reaching a confident conclusion. This process demonstrates how context-rich investigations provide SOC teams with both the speed and accuracy they can trust.
How Does the AI SOC Agent Frame the Investigation?
How Are Alerts Initially Classified?
An investigation often begins with a simple trigger. In this example, the SOC receives an alert for multiple failed login attempts. The Dropzone AI SOC analyst first determines the type of event it's examining, classifying the incident as an identity-related issue.
Once the event is labeled correctly, the system translates the login failures into a problem space. This shift from raw data to an organized case is what gives the agent room to think and investigate like an analyst would.
What Hypotheses Does the AI Agent Build?
With the case defined, the agent lays out hypotheses for why the alert might be malicious (a true positive) or benign (a false positive). Was this simply a user mistyping their password repeatedly? Could it be an automated brute-force attempt? Or is it an early indicator that the account itself may already be compromised? Each hypothesis represents a distinct scenario with different investigative implications.
The agent converts those hypotheses into an investigative plan. Key questions to answer:
- Which user account is involved, and what are their role and permissions?
- How many failed attempts occurred, and over what timeframe?
- Were attempts from one IP or multiple geographies?
- What user agent and metadata are present: is this normal behavior?
- Did the account eventually succeed in logging in, and from where?
- Did they log into other services with the same IP and user combination?
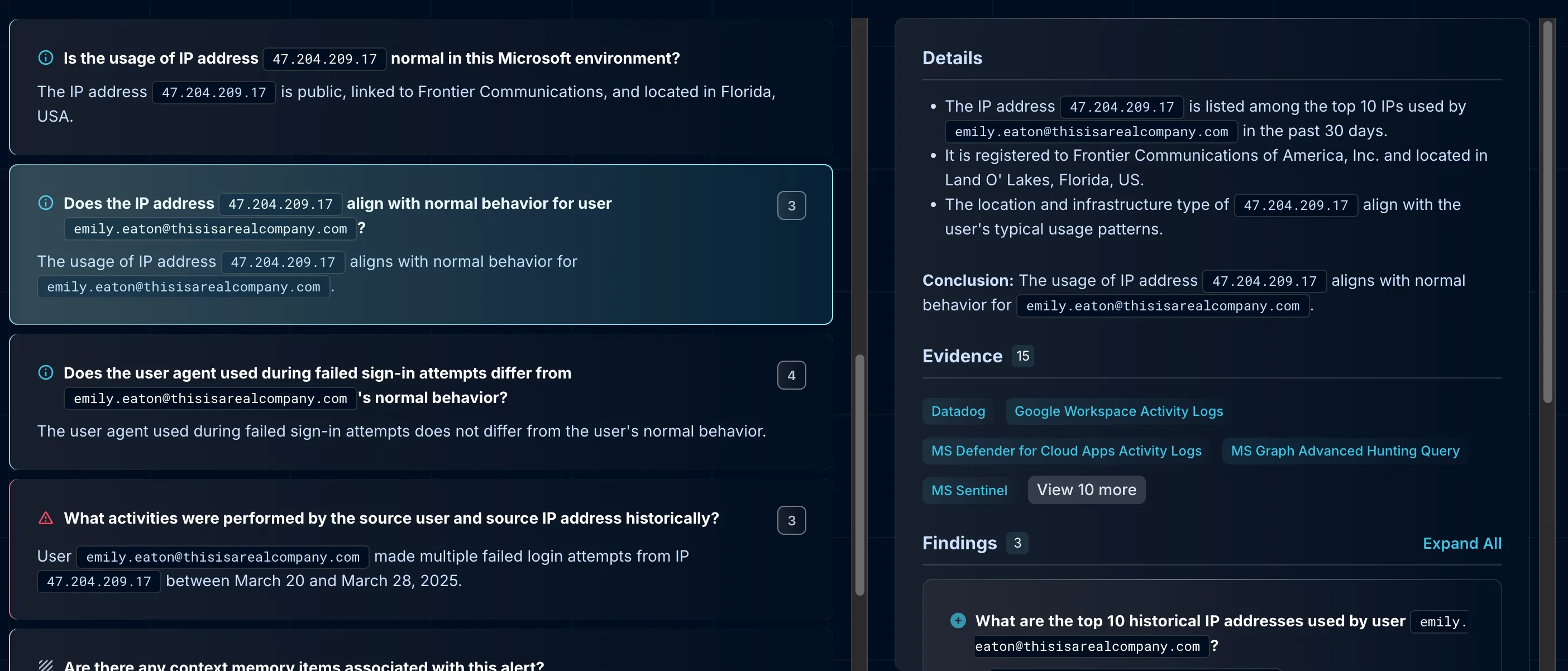
Framing these types of investigative questions early ensures the investigation is aimed at ruling scenarios in or out, just as a seasoned analyst would.
How Does the AI Agent Gather and Analyze Evidence?
Which Tools Does the AI Agent Query?
Now that the case is framed, the AI SOC analyst collects data to form findings. For this particular investigation, the agent queries multiple systems:
SIEM Analysis:
- Login events for the account in question
- Timeline of failures and successes
- Source IPs and authentication attempts
- Error codes and their context
Identity & Authentication Systems:
- SaaS business tool authentication details
- Geographic anomalies in login patterns
- Historical IP and user agent combinations
- MFA usage patterns for this device and IP
Enrichment Systems:
- IP reputation checks
- Geographic consistency analysis
- Known threat actor associations
- Historical behavioral baselines
.webp)
Each data source adds important context. If the same IP and user combination have been used successfully across services historically, it's likely legitimate. Successful MFA authentication with this device, user agent, and IP combination further indicates a false positive.
How Do Agents Adapt to Different SIEM Environments?
The types of queries that an AI SOC analyst uses aren't generic ones copied across deployments. They're adapted to match the schema and field names of the specific SIEM deployments.
In one SIEM, a failed login might be labeled status=401, while in another it could be logged as failureReason=invalidCredentials. Dropzone's AI SOC agent learns those differences in advance and tailors its questions accordingly. This prevents wasted searches and ensures that results are returned in a usable form.
The point is not just to run fast, but to run deep. Agents pivot through the evidence with purpose, aligning queries to the investigative hypotheses formed earlier. Each result is weighed in terms of what it confirms, what it rules out, and what new questions it raises.
An AI SOC analyst knows how to use your tools just like one of your expert analysts. That methodical movement through SIEM, identity, EDR, and enrichment systems delivers both speed and depth, making the investigation efficient without sacrificing accuracy.
How Does the Agent Reach a Final Verdict?
How Are Findings Transformed into a Narrative?
Once the evidence has been gathered, the agent shifts from collecting findings to assembling a coherent account of what actually happened.
The login trail shows multiple failed attempts, followed by a successful authentication with MFA. The combination of user, IP address, and user agent match previous successful login attempts to other online portals. IP reputation checks reveal no association with malicious activity, and EDR telemetry confirms that no suspicious processes or privilege escalation attempts occurred after login.
Each piece of evidence is placed in sequence, creating a timeline that explains the event rather than just listing the raw signals. The AI agent isn't pushing disconnected results back to the human analyst; it's connecting them into a structured narrative that shows what was tested, what was confirmed, and what was ruled out.
That transformation from raw data to context provides human analysts with a report they can quickly read, understand, and trust.
How Does the Agent Test Each Hypothesis?
With the evidence organized, the investigation tests each hypothesis against findings:
Brute-force attack hypothesis:
- Unlikely: low volume of login failures
- Clean IP reputation
- No automation indicators
Compromised account hypothesis:
- Unsupported: post-login activity normal
- No privilege escalation attempts
- No suspicious process execution
User error hypothesis:
- Fully consistent: eventual successful login with MFA
- Matches historical user behavior
- Same device and user agent as previous sessions
By running through each explanation and weighing it against findings, the agent reaches a confident conclusion: the case is benign.
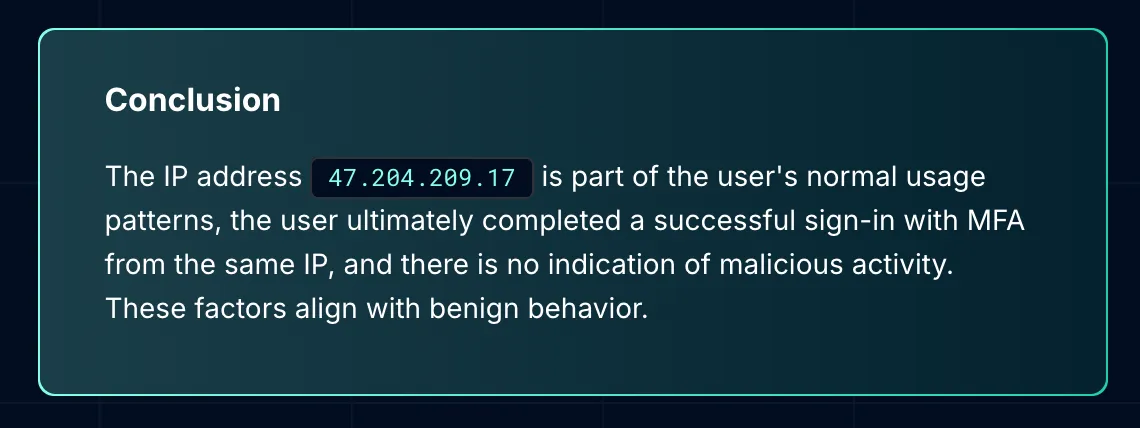
The final output is not just a list of queries and logs; it's a context-rich incident report. It tells the story of the event, explains why specific paths were ruled out, and documents the reasoning behind the verdict.
Analysts receive not only the data but also the investigative logic, making it easier to validate, document, and move forward without unnecessary escalations.
Conclusion
The difference with Dropzone AI SOC analysts is that they don't stop at pulling data and enriching it. They think, question, and connect evidence from multiple tools and systems in the same way an experienced analyst would.
Dropzone's strength comes from the ability to:
- Reason across tools and test alternative explanations
- Present clear stories backed by evidence
- Deliver context-rich verdicts analysts can trust
The impact is tangible:
- Faster mean time to resolution (MTTR)
- Fewer false positives escalated
- Higher confidence in conclusions
- Investigation quality that matches senior analysts
Dropzone's AI SOC analyst doesn't just accelerate investigations—it raises their quality. See Dropzone agents investigate real cases. Explore the demo gallery or take our self-guided demo (a live environment where you can play around in the product).















