Introduction
AI is already reshaping how cyberattacks are carried out, from phishing to malware development, threat actors use generative AI to move faster, evade detection, and overwhelm traditional defenses. Security teams are pressured to respond, but headcount and tooling alone can’t keep pace. The solution lies in adopting AI on the defender side tools that reason, triage, and scale alongside your existing stack. This article will cover how attackers are operationalizing AI today, why this shift changes cyber risk economics, and how AI can help SOCs respond with speed, context, and confidence.
By the Numbers
- 12,000+ cyber incidents analyzed showing AI usage (Google DeepMind, 2025)
- 50%+ click-through rates on AI-generated phishing (DeepMind Research)
- 90% reduction in investigation time with AI SOC analysts (Dropzone AI)
- 10X increase in alert handling capacity without adding headcount
How Attackers Are Weaponizing AI
The use of AI in offensive cyber operations is no longer theoretical. Both researchers and real-world intelligence teams have observed its role in amplifying attack speed, scale, and impact. According to Google DeepMind’s analysis of over 12,000 cyber incidents, attackers already use large language models (LLMs) across multiple stages of the attack chain from reconnaissance and payload development to evasion and persistence tactics.
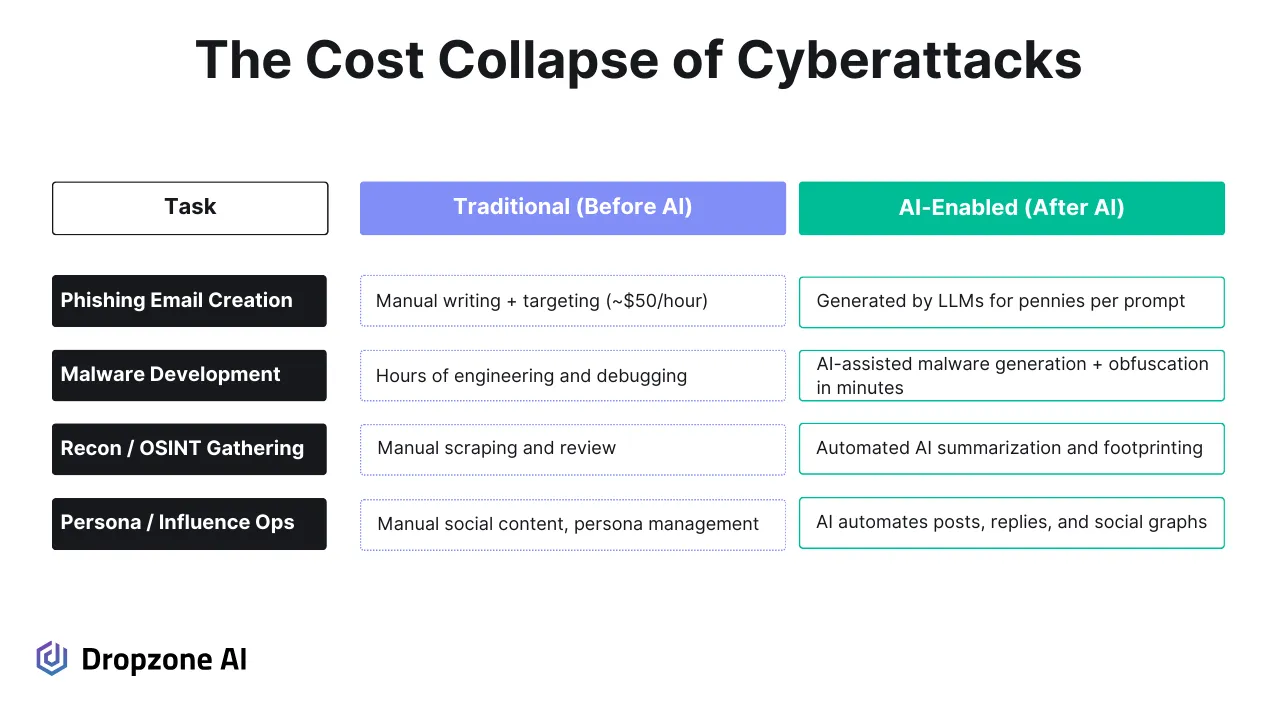
Phishing remains one of the most accessible and effective avenues for attack. AI-generated emails are now context-aware and linguistically polished, making them harder to distinguish from legitimate communications. DeepMind’s findings, supported by other evaluations, show that attackers generate thousands of personalized phishing variants at scale, with click-through rates often exceeding 50%. LLMs tailor tone and content by pulling data from OSINT sources, drastically improving engagement and bypassing traditional spam filters.
Reconnaissance has become faster and more thorough. To build target profiles, LLMs can parse and summarize technical documentation, public datasets, leaked credentials, and software repositories. This accelerates infrastructure fingerprinting, surfacing likely misconfigurations or vulnerable services. MITRE’s OCCULT framework further supports this, measuring how modern LLMs are increasingly capable of perceiving environment state, planning attack sequences, and modifying tactics in response to feedback.
Malware development is also seeing a transformation. Attackers use LLMs to draft or refactor malicious code, test for detection, and introduce minor polymorphic changes, evading signature-based tools. DeepMind’s research highlights AI’s ability to assist in crafting obfuscated payloads and embedding evasion logic tuned to specific environments.
Beyond technical intrusion, adversaries are using AI for influence operations. LLMs are now deployed to create fake personas, manage large-scale disinformation campaigns, and auto-generate convincing engagement (e.g., comments, reviews, or posts) to boost credibility. DeepMind flagged this trend as one of the most accessible vectors for lower-resourced threat actors looking to shape perception or conduct social engineering at scale.
Why This Changes the Economics of Cybercrime
One of the biggest shifts introduced by AI is how it fundamentally alters the cost model of cybercrime, making it more profitable and therefore encouraging more activity in this area. Just like cryptocurrency made ransomware more profitable and thereby encouraged the growth of the ransomware cybercrime economy, we will see AI automation encouraging greater scale and speed for cybercrime in general.
In the past, certain attack phases like discovering zero-days, crafting tailored phishing lures, or obfuscating custom malware were prohibitively expensive in both time and skill. These activities required highly trained specialists, long timelines, and access to purpose-built infrastructure. Now, that bottleneck is rapidly disappearing. According to the DeepMind team, the biggest risk frontier AI poses in cybersecurity is the potential to “dramatically change the costs associated with stages of the cyberattack chain” that were traditionally time-consuming or out of reach for most attackers.
We're already seeing this in action. AI can now automate large portions of vulnerability research, summarizing code paths, testing for edge-case input, and identifying misconfigurations that normally take weeks to uncover manually. It’s not just about saving effort, it’s making previously inaccessible capabilities widely available. A basic prompt fed into a capable model can generate multiple payload or phishing email variants with minimal tuning. This dramatically reduces the expertise barrier, expanding the pool of threat actors capable of conducting multi-phase attacks.
This shift doesn’t just increase attack volume, it changes how defenders must think about scale. As AI lowers the cost of reconnaissance, weaponization, and delivery, we’ll see more attacks launched and more often with adaptive behaviors. These aren’t just noisy scans or recycled malware; they're personalized campaigns that mutate with every iteration.
SOCs are already dealing with alert fatigue, and now they’re being hit with faster, more evasive attacks often driven by models that reason in ways traditional detection systems weren’t designed to handle. Without rethinking how investigations scale, teams won’t just fall behind, they’ll drown in noise they can't sort fast enough to act on.
How AI for Blue Teams Can Close the Gap
Defender-side AI is becoming a necessity, not just to reduce overhead, but to address the speed and scale at which adversaries are operating with AI augmentation. Traditional SOC workflows built around static detection logic and manual triage are insufficient.
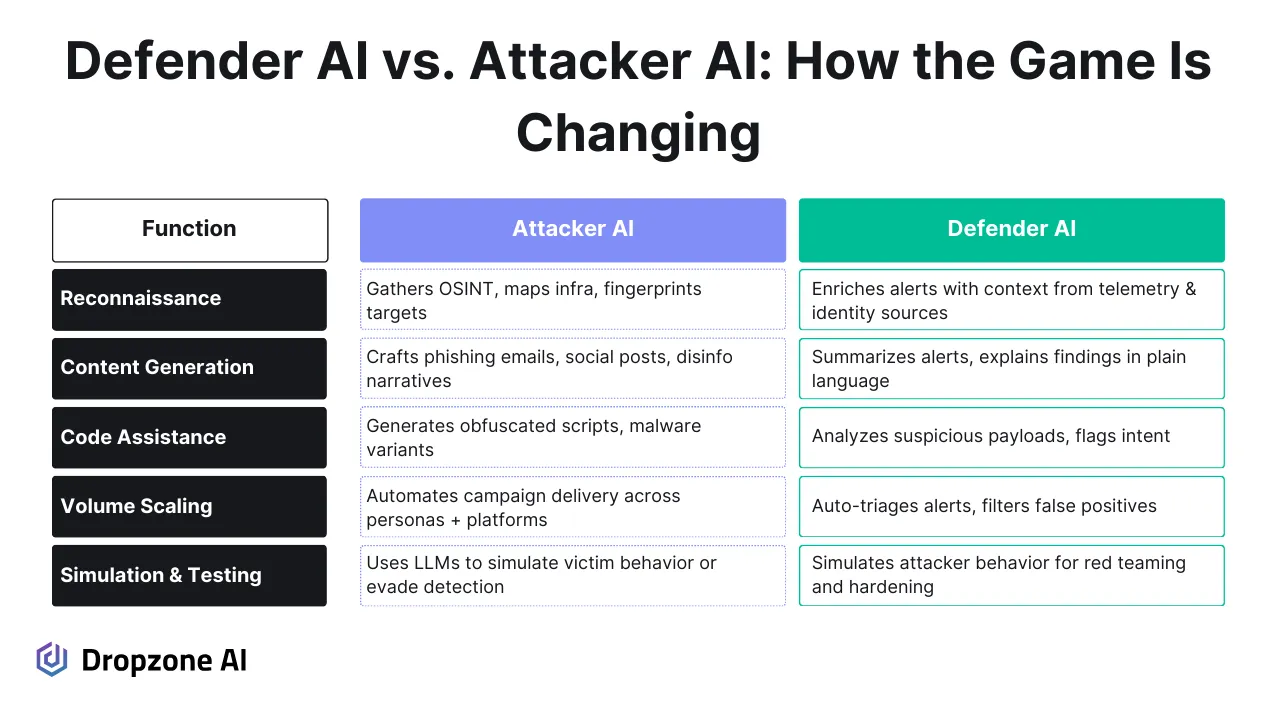
Research from Google DeepMind and MITRE shows that LLM-assisted threat actors can move faster across the kill chain, particularly in early-stage reconnaissance, delivery, and lateral movement phases. This shift demands automated systems that can adapt and reason in real time.
Dropzone AI is designed to provide cybersecurity defense teams (blue teams) with AI-powered SOC capabilities. Dropzone’s AI SOC Analyst integrates with existing security stacks, SIEMs, EDRs, identity platforms, and cloud telemetry, and autonomously conducts full-scope investigations. This means it pulls and correlates signals across domains, enriching alerts and interrogating telemetry for behavioral patterns, privilege misuse, and suspicious escalation paths. The AI SOC agent checks authentication patterns for anomalies, evaluates account roles and permission changes, analyzes process trees, and investigates access behavior based on historical norms. It also verifies with users whether access or file sharing activity was legitimate, if needed.
Dropzone AI SOC Analysts are software and do not need to sleep, and are perfect for providing resource-constrained teams with 24/7 triage capability, reducing reliance on overnight staffing while maintaining investigative coverage during off-hours. The result is a SOC operation that scales response without scaling headcount, and adapts to attacker innovation without constant re-architecture.
Weaponizing LLMs for Cyber Defense
Attackers aren’t waiting to test the limits of AI, they’re using it to scale faster and hit harder. If defenders don’t adapt, they’ll always be a step behind. Dropzone AI is on a mission to change the asymmetry in cybersecurity so that it favors defenders. Our aim is to equip blue teams with an army of AI SOC agents that help them to operate with speed, accuracy, and scale.
AI promises to make cybercrime much more profitable and we can expect to see attacks ramp up as criminals learn how to use these technologies more effectively. It’s imperative for defenders to leverage AI to improve their own capabilities, and one of the biggest areas for improvement is in alert triage and investigation. This is routine work that can now be reliably automated with multi–agent systems like Dropzone AI.
This is how modern security teams can close the gap, automating triage, enriching context, and giving analysts room to focus on what matters. Dropzone AI gives you that capability out of the box, without needing to rip and replace your tools. Book a demo to see how it works in your environment and why teams using Dropzone are already scaling smarter.















