Key Takeaways
- Tool use is the foundation of real investigations. SOC AI must query SIEMs, pivot across EDR, and validate identity systems, just as analysts do.
- Shallow integrations that merely transfer data fail to replicate analyst reasoning and leave gaps in investigations.
- Dropzone AI trains agents to operate tools like human analysts, delivering context-rich findings that analysts can trust.
Introduction
In cybersecurity, "integration" is often reduced to little more than an API call, but connecting to a tool is not the same as knowing how to use it effectively.
Analysts don't just pull logs, they learn data schemas and query languages in SIEMs, cross-reference identity systems, and dig through EDR telemetry until they find answers that matter. Dropzone’s AI SOC Analyst was built to replicate those expert analyst techniques.
Our AI SOC agents aren't just familiar with your tools; they're pre-trained to operate them like an analyst would, adapting to your unique environment. This post explains how we train our AI SOC agents to think and act in this manner, and why it makes such a significant difference for modern SOCs.
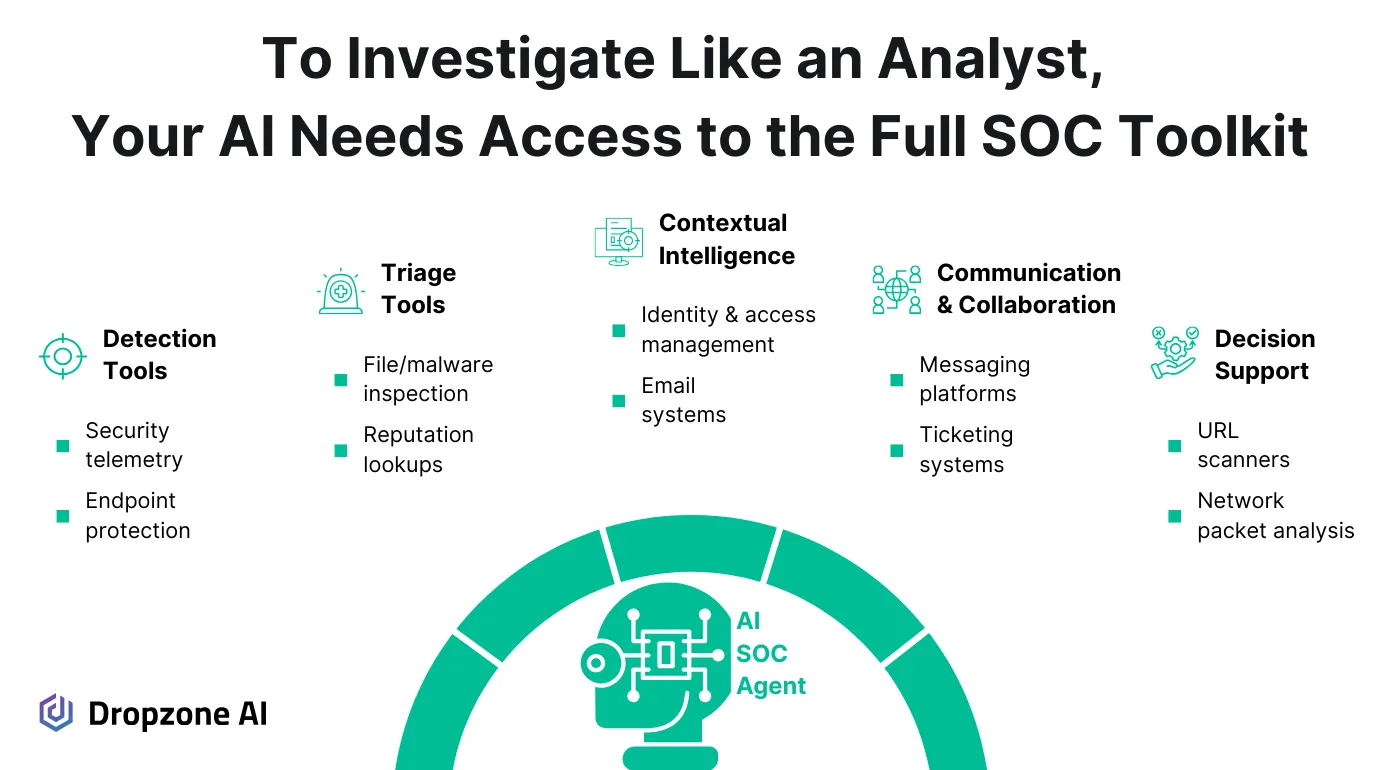
Why AI SOC Agents Need More Than Simple Integrations
How AI SOC Agents Should Actually Use Security Tools vs. Data Pipes
Traditional security automation often stops at "integration." They connect to a SIEM, pull down some data, possibly normalize it, and then push it elsewhere.
That kind of setup can be useful, but it doesn't make the system any smarter. You wouldn't call it "using the tool" in the same way an analyst does; it's more like tapping into a feed and moving on.
Dropzone takes it further: our AI SOC agents don't just connect to a tool; they learn how to operate it effectively. This pre-training involves:
- Learning the documentation; or how to use the tool expertly
- Scanning the deployment to understand what data is available
- Understanding what types of questions can be answered with a particular tool
It also means shaping their behavior to mirror what a seasoned analyst would actually do during an investigation. That's a significant shift because instead of an agent acting like a data courier, it behaves like an investigator. It pivots, cross-references, and validates.
The difference is clear in the outcome: context-rich findings rather than raw, disconnected logs.
Training AI SOC Agents to Think Like Security Analysts
AI SOC agents require more than just a login; they must recognize and utilize the same investigative patterns that human analysts rely on. That's what we focus on when building our AI SOC agents. We use the OSCAR investigative methodology to ensure that our AI SOC agents follow best practices.
We don't just give them access; we train them how to use tools to:
- Query logs to analyze historical baseline behavior
- Use malware analysis tools to see if an executable is malicious
- Safely browse a suspect link to confirm phishing
- Analyze a network packet capture to look for the exploitation of a vulnerability
- Look for specific patterns in EDR telemetry
- Cross-check an identity service when something doesn't add up
This doesn't just involve bolting rules onto an integration; it teaches agents to conduct an investigation in the same manner as an analyst would.
They learn which questions matter in different contexts, how to refine queries when the first answer isn't enough, and how to interpret the different quirks of outputs from one deployment to another.
When agents are trained this way, they're not just processing alerts faster. They're actually investigating—connecting dots, asking the right follow-up questions, and producing results that security teams can act on with confidence.
That's what turns "integration" into real autonomous task completion. When AI SOC agents can use tools in the same way an expert human can, teams see alerts resolved more quickly, with less noise reaching human analysts.
How Dropzone AI Trains AI SOC Agents for Tool Mastery
Learning the Shape of Your Environment
No two SOCs look alike, even when organizations run the same SIEM platform. The data structures, naming conventions, and indexing strategies can vary significantly, making a cookie-cutter integration ineffective.
Our AI SOC agents handle this upfront. Before agents begin working on alerts, they:
- Scan your SIEM to map the schema
- Catalog available data
- Understand how your specific environment is wired together
That early mapping matters; it enables agents to ask meaningful questions against your data model, rather than relying on generic queries that may or may not yield the correct results.
A Splunk environment that uses custom indexes for authentication logs will appear quite different from one that consolidates them into a default index.
This isn't limited to SIEMs. Agents also examine connected tools, such as:
- EDR platforms
- Identity providers
- Directory services
- Email servers
- Ticketing systems
They build a picture of what information exists and how to retrieve it effectively.
Instead of treating every deployment as interchangeable, we train our agents to operate as though they were dropped into your SOC and expected to contribute from the very first day.
.webp)
Customizing AI SOC Agent Behavior for Real Investigations
Once an agent understands the shape of the data, they need to know how to investigate it effectively. That's where our training becomes far more than API access.
Agents are taught to ask the kinds of investigative questions that analysts ask in real workflows:
- "Which accounts touched this endpoint before it was flagged?"
- "What processes spawned from this parent binary?"
- "Which users authenticated from this IP during the timeframe in question?"
The difference is that these questions aren't just templates; they're tuned to your environment.
If your SIEM logs use src_ip while your identity store refers to the same field as sourceAddress, the agent is aware of the translation. If one deployment enriches logs with geo-IP data and another doesn't, the agent adjusts its queries and expectations accordingly.
That nuance is what makes them reliable rather than brittle.
When an investigation unfolds, this preparation shows. Instead of stopping at surface-level correlation, agents pivot across data sources the way a skilled analyst would:
- Tightening queries
- Building historical baselines
- Checking files, IPs, and domains against reputation services
Whether they're working in Splunk, Sentinel, or a custom build, they know how to operate in your tool stack with precision. That's what makes the difference between AI that only automates and AI that actually investigates.
The payoff is fewer missed signals and investigations that move at the pace your SOC needs.
Vendor-Agnostic AI SOC Agent Architecture: Built for Enterprise Security
Built for Mixed Environments
Modern SOCs rarely live in a single-vendor world. Teams often run a mix of tools and systems for:
- Data lake, data pipeline, and SIEM
- Endpoint security
- Identity security
- Cloud security
- Network security
- Productivity tools like Google Workspace or Microsoft 365
- Identity and access management
- … and other security tools and business systems
Each of these represent important potential sources of context for an alert investigation.
Dropzone's architecture is designed to thrive in that mixed stack reality. AI SOC agents interact with tools in a vendor-agnostic way, treating each one as a source of data and investigative power rather than a product with a specific logo.
That independence matters when deployments change over time. Adding a new SIEM or swapping an EDR doesn't break the system; agents adapt the way an analyst would.
This means Dropzone supports the natural evolution of a SOC without forcing teams into a single ecosystem or rigid framework.
Security and Control by Design
Flexibility is only one side of the equation; the architecture must also meet the security expectations of teams that handle sensitive investigations daily.
We built it with that in mind. Unlike protocols that rely on third-party chains, our AI SOC agents own the entire decision-making loop internally:
- No investigation steps are exposed to the open internet
- No external broker is required to maintain the system's operation
- Every decision remains within your controlled environment
This design provides security teams with what they truly want: control, performance, and auditability.
Agents operate within a contained environment that the organization governs directly. Every decision and query is traceable, every action is logged.
The result is an architecture that supports modern AI-driven investigation without sacrificing the operational trust that SOCs demand. This gives leaders confidence that AI-driven investigations improve MTTR without adding new security risks.
Conclusion
For SOCs, the real test of AI isn't how many integrations it can list, but whether it can effectively utilize those tools during an investigation. Tool use should be the baseline, not an added feature.
Dropzone's AI SOC agents are trained to work inside your stack with the same investigative discipline your team relies on every day, querying, pivoting, and validating until the answers hold up.
That's what makes them more than just automated workflows; it makes them true partners who can think and act like analysts, providing your security team with both speed and depth where it matters most.
Want to see Dropzone AI in action? Explore our demo gallery or take our self-guided demo for a spin (it’s a live environment you can play with).















