Key Takeaways
- AI Handles: Alert triage, log analysis, data correlation, pattern recognition
- Humans Handle: Tier 2 escalations, incident response, threat hunting, program improvements
- Time Savings: 85-90% reduction in routine task time
- Best Practice: Use AI for scale, humans for judgment
- Implementation: Start with alert triage, expand to adjacent areas
Introduction
Maintaining a SOC, you know how exhausting it can be to keep up with endless alerts, constant log analysis, and repetitive investigations. It’s easy to get bogged down in routine tasks, leading to burnout and missed opportunities to improve your security posture. AI can help by automating repetitive work, reducing alert fatigue, and speeding up investigations.
But AI is not here to replace you. Knowing what AI can handle and where your expertise is still necessary helps you get the most out of AI SOC tools. This article breaks down what AI can automate, where human skills are essential, and how you can create a more efficient SOC by combining both.
What AI Can Automate in the SOC Today
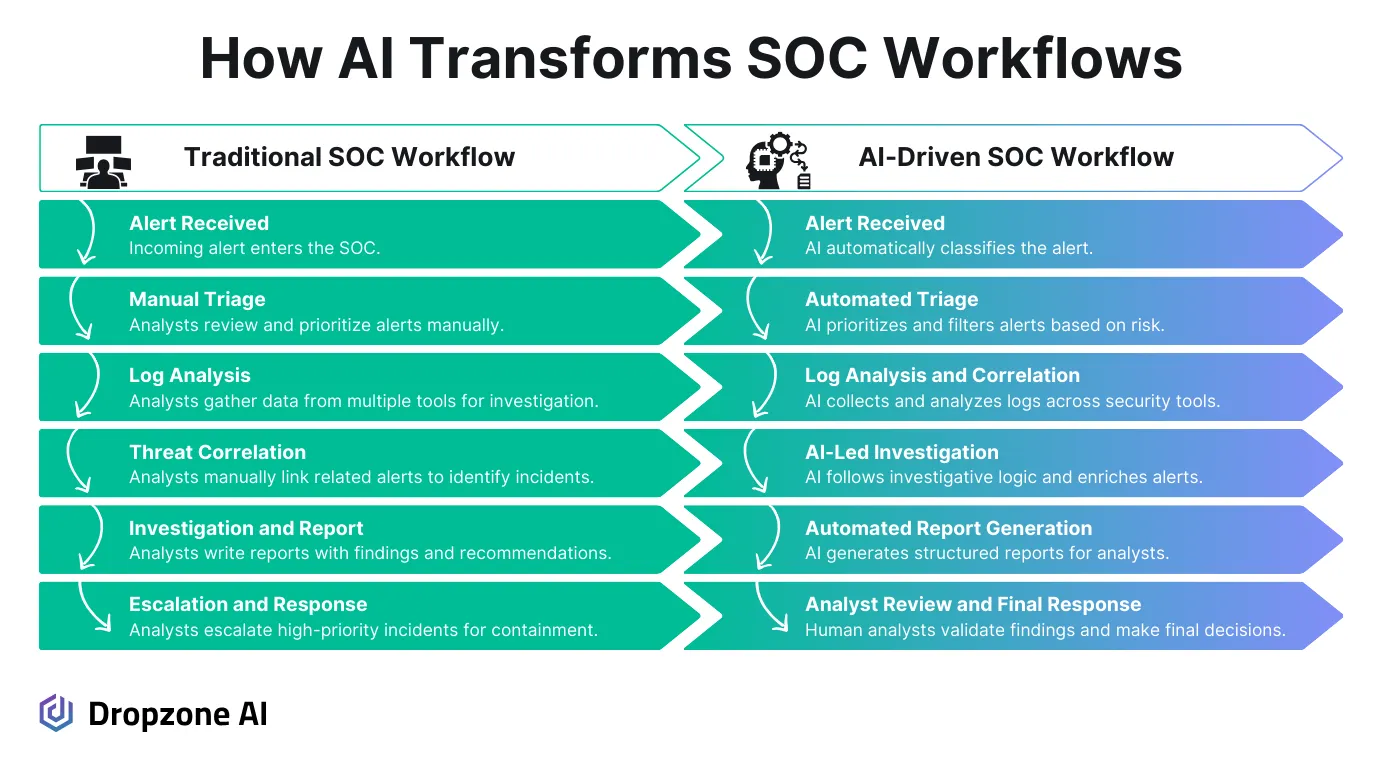
AI-Powered Alert Triage and Prioritization
AI is a game-changer in handling the overwhelming number of alerts generated in your SOC. Replicating security analyst investigation methodology, agentic AI systems can autonomously investigate security alerts and produce full investigation reports for review. This autonomous investigation dramatically reduces false positives and helps your team focus on high-priority incidents.
For example, when AI investigates a suspicious login alert, it checks user authentication patterns for anomalies, investigates access patterns to identify suspicious behavior, and verifies if the activity aligns with normal user behavior. Instead of wasting time on non-issues, your team receives context-rich, actionable alerts, improving efficiency.
AI also continually refines its accuracy through feedback, learning from human analysts, and adapting its logic over time. This adaptive process results in faster, more accurate triage that helps prevent alert fatigue.
.webp)
Automated Log Analysis and Data Correlation
Analyzing log data across multiple systems can be daunting, especially when dealing with different data formats and volumes that can reach terabytes daily. AI automates this process by pulling data from SIEMs and other security and business systems, analyzing process trees to trace malicious execution, and investigating access patterns to identify suspicious behavior.
Rather than treating data sources in isolation, AI looks at historical investigations to identify attack patterns and correlates events to build a complete attack timeline. For instance, if a suspicious login is detected in identity logs and simultaneous lateral movement is observed in endpoint telemetry, AI can cross-reference these events and surface them as part of a multi-stage attack. This correlation level reduces investigation time and improves accuracy by connecting related activities that might be missed in manual reviews.
With automated log analysis, your team can quickly visualize attack paths, prioritize remediation efforts, and shift from reactive responses to proactive security measures. AI saves your analysts hours of manual data collection and provides deeper insights into potential attack vectors.
What AI Still Needs Human Analysts For
Investigating Complex Attack Campaigns
AI can be a great assistant when identifying potential threats, but some investigations require human judgment and deeper analysis. Multi-step attack campaigns including lateral movement, privilege escalation, or social engineering, aren’t always obvious especially if some activity does not generate alerts or occur over a long period of time, and that’s where your expertise and intuition matters.
AI provides detailed data points by checking user authentication patterns, analyzing permissions and recent user account and group changes, and deobfuscating scripts or payloads to determine intent. However, without human oversight, it sometimes can’t assess the broader implications. You need to evaluate how that activity fits into the bigger picture and decide if it’s an actual threat.
Human reasoning is essential to connect different clues, especially when attacks span multiple stages or involve subtle tactics. Your understanding of your organization’s threat model and risk impact is something AI can’t easily replicate now, although it should be able to do this in the future. While AI sets the foundation, your insight and critical thinking determine the best action.
Incident Response and Threat Hunting
When it’s time to respond to incidents, AI can offer recommendations, but the final decision-making is always yours. Whether it’s containment, remediation, or developing a strategy to prevent future incidents, these choices require experience and judgment.
Proactive threat hunting is another useful area for your creative thinking and intuition. Unlike AI, which follows predefined patterns and logic, you can simulate adversary behavior, look for emerging tactics, and analyze unusual activity in ways AI might not predict.
AI supports you by pulling data from SIEMs, checking file hashes against threat intelligence feeds, and investigating access patterns to provide actionable context. However, discovering unknown threats still requires human judgment and expertise. Your ability to think creatively and adapt to new challenges can make a big difference in staying ahead of attackers.
How SOCs Can Optimize Workflows With AI
Using AI to Free Analysts for Higher-Value Work
When you let AI handle repetitive tasks like alert triage and log correlation, your team can focus on proactive security work. This means spending more time on threat hunting, improving detection strategies, and working on long-term security improvements.
AI-generated reports, created after analyzing process trees, verifying file sensitivity, and checking user access patterns, reduce the documentation workload. This allows analysts to focus on higher-priority tasks, resulting in faster responses to real threats and a team that can dedicate more energy to higher-impact projects.
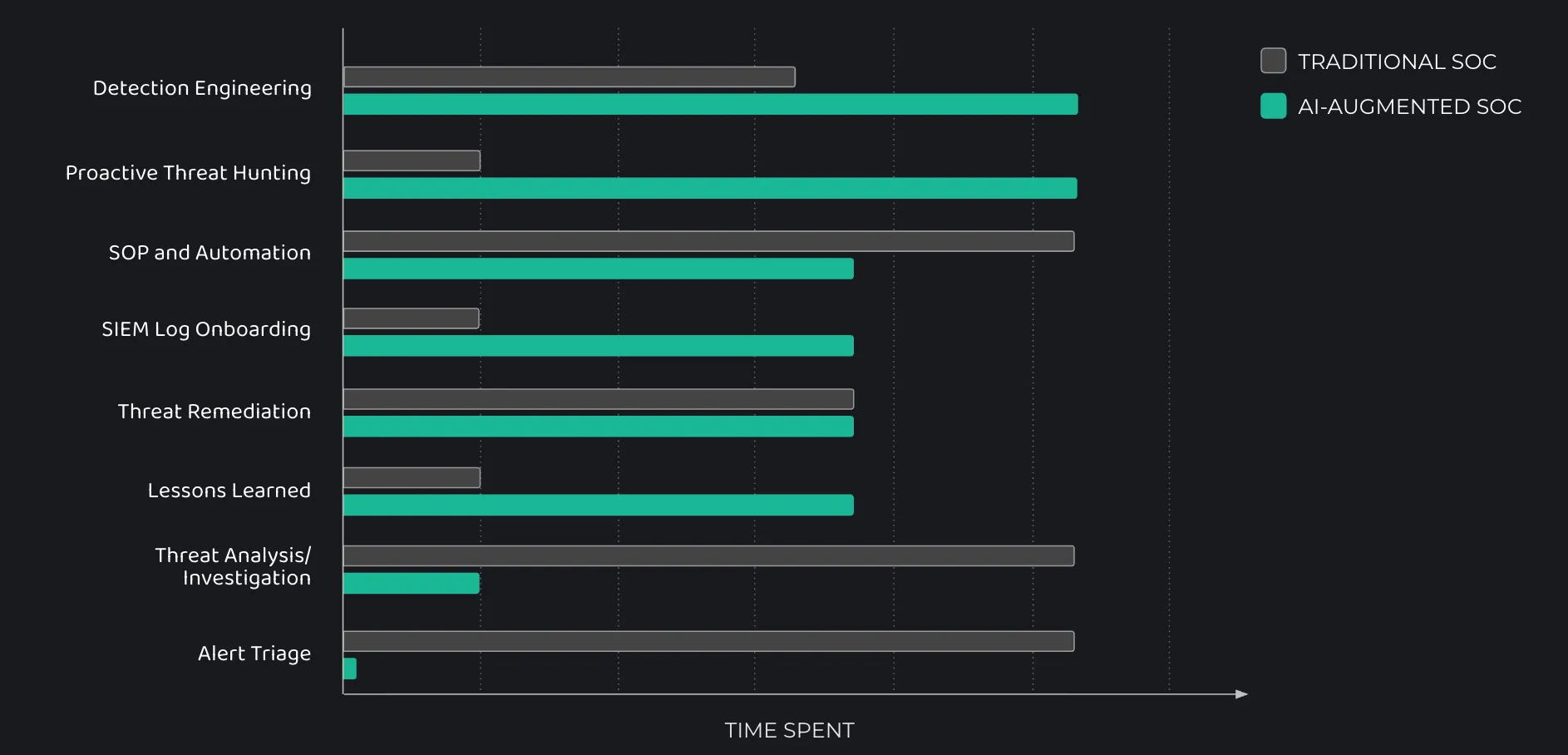
Combining AI and Human Expertise for Maximum Efficiency
AI isn’t here to replace your analysts; it works best as a smart assistant that boosts their capabilities. The more feedback you provide, the better AI can identify relevant patterns by examining historical investigations, checking file hashes against threat intelligence feeds, and analyzing user authentication anomalies.
Consider it an ongoing collaboration; combining AI’s ability to scale and process data with your human judgment and experience will build a stronger, more efficient SOC. Balance is key; let AI do repetitive work while you and your team focus on decision-making and strategic security efforts.
Conclusion
AI transforms SOC operations by taking over repetitive tasks like triaging alerts, analyzing logs, and correlating events across tools. This frees you to focus on high-value activities like threat hunting, strategic planning, and complex investigations. But AI works best when paired with your expertise. It provides data, but you bring the context and decision-making power. The smartest SOCs use AI SOC analysts like Dropzone AI to handle the repetitive load so analysts can focus on what matters most: keeping your organization secure. Ready to lighten the load? Check out our self-guided tour (a live environment with test data) to see how AI-driven security automation can help your team.















