Quick Answer
Cybersecurity debt is the accumulated risk from deferred security tasks like patching, configuration management, and access reviews. It forms when teams spend most of their time on reactive alerts instead of preventive controls. AI SOC agents like Dropzone reduce this debt by automating alert triage, freeing 10-20 hours weekly for foundational security work that prevents future incidents.
Introduction
Cybersecurity debt builds through deferred patching, outdated configurations, and missing controls. It adds up when teams are stuck reacting and can’t make time for foundational work. The CIS Critical Security Controls (CIS Controls) prioritize foundational cybersecurity hygiene and are designed to keep that debt manageable, but without space to apply them, exposure grows. AI SOC agents, such as Dropzone AI, don’t replace analysts; they free them from repetitive work, allowing them to focus on reducing risk instead of chasing symptoms. In this article, we’ll examine how cybersecurity debt forms, why it persists, and how AI helps teams allocate time toward work that enhances their security posture.
What Builds Cybersecurity Debt
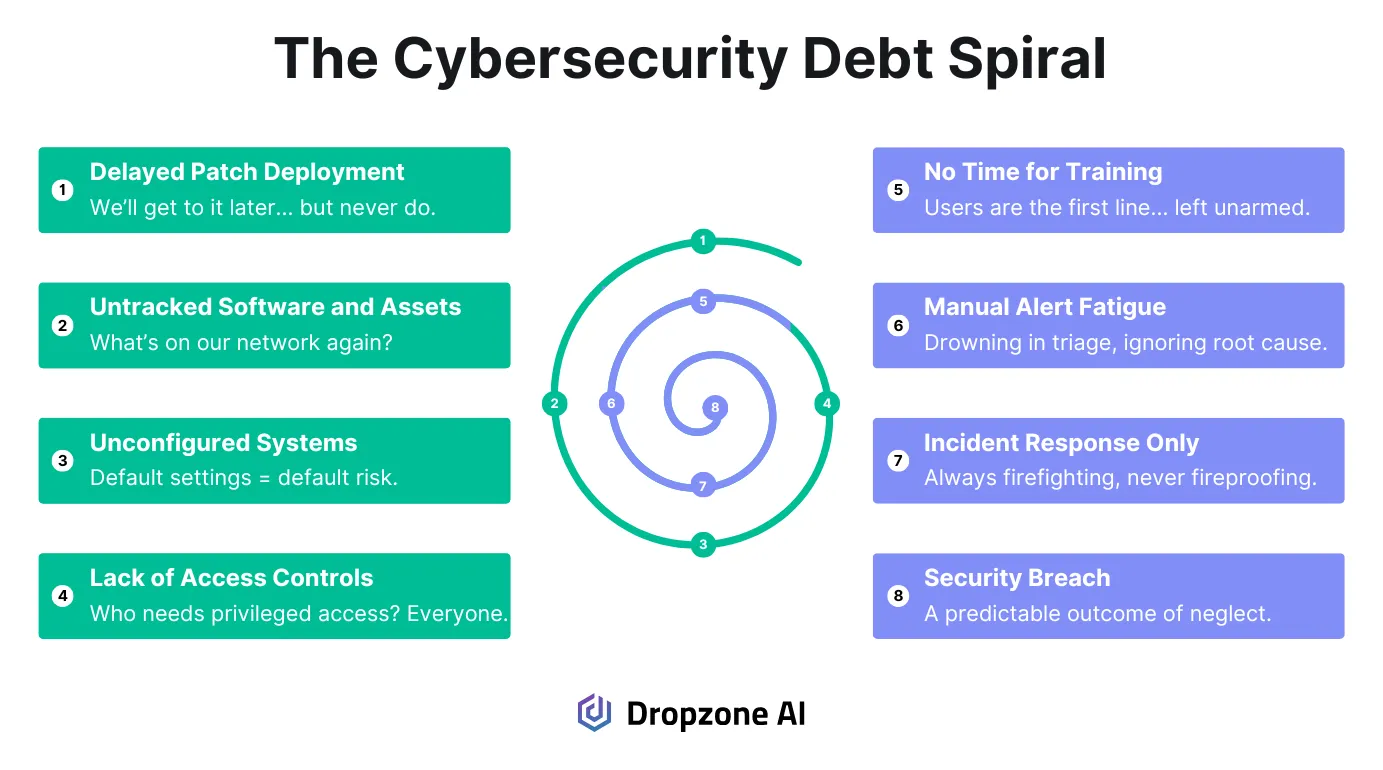
Most teams don’t plan to let foundational work slide. It happens because there’s no breathing room. When incident queues fill up and alerts continue to fire, the time allocated for baseline reviews, patch cycles, or configuration audits gets pushed back, only to be pushed back again. That’s how debt builds. Not all at once, but every time a hardening task is deferred in favor of closing tickets.
Start with asset and software inventories, focusing on CIS Controls 1 and 2. If you're not actively maintaining visibility into what’s deployed, you’re leaving gaps that attackers can walk through.
Shadow IT, orphaned cloud instances, and outdated software versions won’t show up in alert logic if they're missing from your inventory. This is a foundational issue, and the longer it remains unaddressed, the more difficult it becomes to rectify without rework.
Configuration baselines (CIS Control 4) often drift in silence. You might start with hardened images or scripts, but enforcement is a different problem.
If you don’t have time to validate or continuously monitor those configurations, exceptions accumulate. Without a feedback loop, you won’t know where systems have deviated until it impacts incident response or leads to a failed audit.
Access control (CIS Control 6) is another high-risk area where debt adds up quickly. In many orgs, identity lifecycle management is still tied to manual reviews or delayed syncs across systems.
Old accounts stay active, privileges don't get right-sized. Service accounts with broad access often go untouched because no one is assigned to review them. These aren’t theoretical risks; they’re patterns that have been exploited in real breaches.
The impact is evident in all the ways that make a team feel overwhelmed: more noise, more near misses, and more time spent firefighting. If the backlog of preventive work grows faster than your team can work through it, you're caught in a cycle. Breaking out of that means reclaiming time and allocating it toward tasks that reduce risk at its source, rather than just reacting to its symptoms.
Time Budget Breakdown: AI Augmented SOC
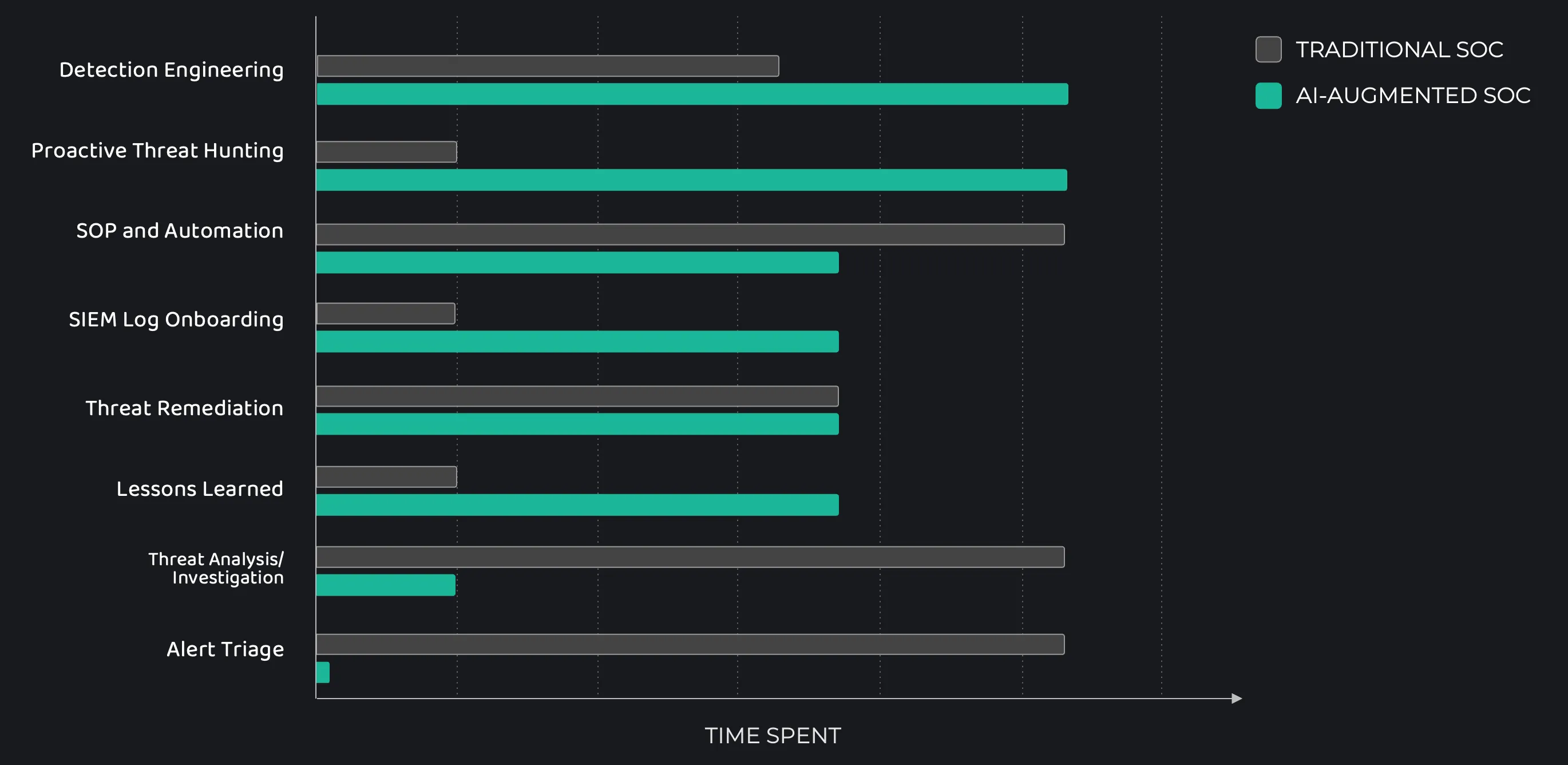
SOC teams already know where the time goes; it’s just that fixing it feels out of reach. When the majority of the week is spent sorting alerts, investigating false positives, and tracking down missing context, there’s little energy left for anything strategic.
Even high-value work, such as tuning detections or reviewing vulnerabilities, gets delayed because daily demands continue to accumulate.
Dropzone’s AI SOC analyst changes this by eliminating the repetitive, low-signal work from your team’s queue. It automatically triages alerts, links related artifacts, and builds a timeline with context that would normally take an analyst 25+ minutes to gather.
Instead of starting from zero, analysts begin with relevant insight and focus only on cases that require judgment. The result is fewer bottlenecks, faster response, and less cognitive drain.
Once the volume is under control, the real shift happens. Time opens up for tasks that have been consistently pushed back, such as targeting high-risk vulnerabilities under CIS Control 7, not just tracking CVEs but also tying them to actual exposure in your environment.
It becomes possible to spend cycles reviewing log sources under Control 8 and improving configuration enforcement under Control 4. You can run real root cause reviews after incidents and close the loop with updated controls under Control 17.
Teams benefit from categorizing their workload by task type: routine operational work, responsive incident activity, and longer-term improvement initiatives. Without automation, the operational and reactive work dominate.
With AI support, the distribution changes. The time that would have been spent digging through tickets can now be used to support backlog reduction, architecture improvements, and enhanced coverage control.
This shift isn’t limited to Dropzone. Other AI-driven tools, such as SOAR and detection-as-code pipelines, support this transition. But reclaiming time isn’t enough.
That time needs to be directed toward hardening systems, reducing noise, and preventing the same issues from recurring. That’s where the value compounds and where your team starts building momentum instead of just holding the line.
Paying Down the Debt: What to Do With Freed Time
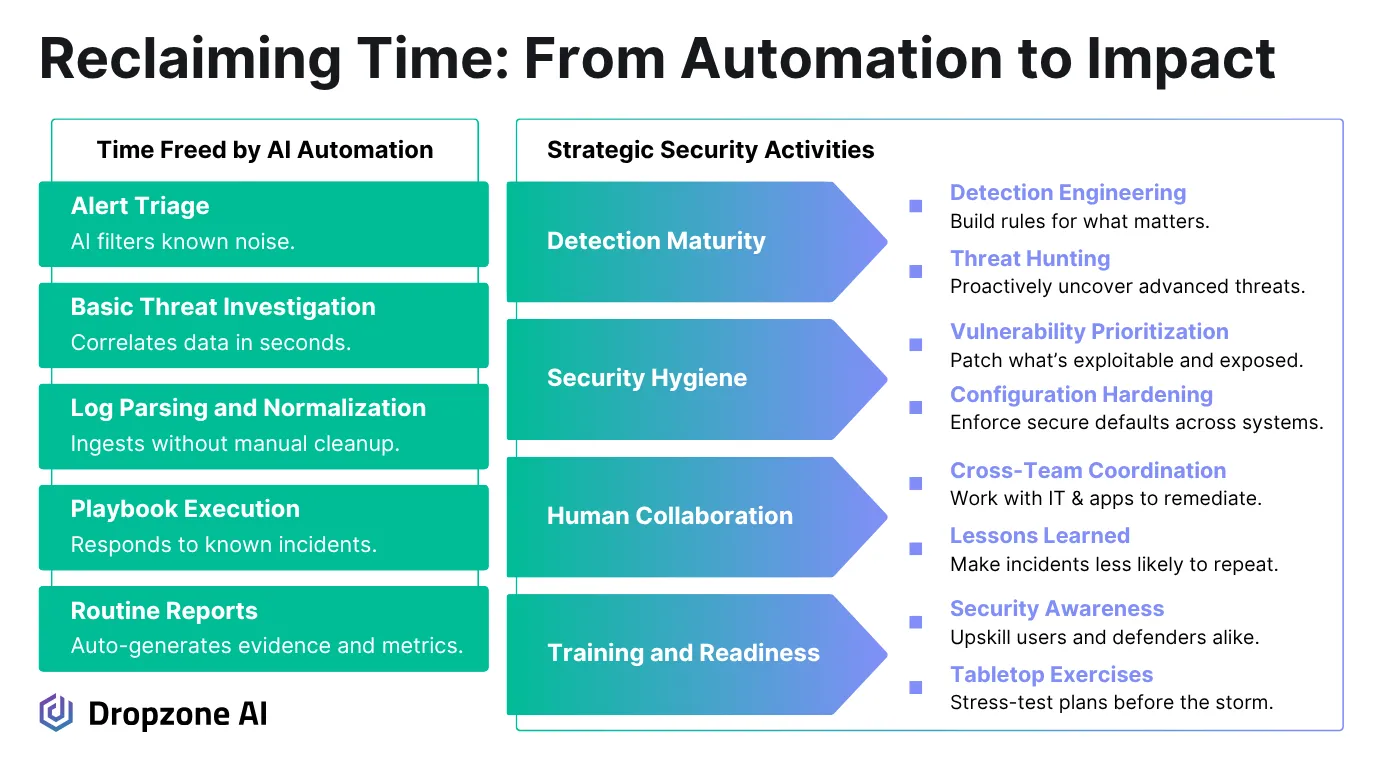
Once you’ve reclaimed time from routine alert handling, the next step is deciding where to apply it. One of the highest-impact areas is vulnerability management, specifically, using contextual risk to prioritize what needs to be fixed first. CIS Control 7 pushes beyond just identifying vulnerabilities.
The focus needs to shift toward understanding which exposures map to high-value assets or common attack paths. This requires correlation between scanner output, asset inventories, and threat intelligence, not just patching based on CVSS scores.
With time available, collaboration across teams becomes more practical. Enforcing secure configurations according to CIS Control 4 typically requires coordination with IT and application owners.
Security teams can work alongside those groups to define enforcement boundaries, validate configs, and deploy changes without creating friction. Drift can be monitored in real time, and variances can be logged and reviewed before they introduce new gaps.
Structured exercises also become feasible. Tabletop drills, simulated breaches, and internal red team scenarios tied to Controls 17 and 18 help identify weaknesses that may not be apparent in alert data.
When combined with regular training under Control 14, these efforts improve readiness and surface gaps in both process and tooling. Without breathing room in the schedule, such strategic exercises rarely occur. Over time, they can be scheduled and refined.
There’s also room for longer-term improvements. Data classification projects aligned with CIS Control 3 establish the foundation for more effective protection policies. Auditing identity stores under Control 5 can help reduce unnecessary access and privilege sprawl.
These are the types of tasks that don’t scale well through automation alone, as there’s a sharp line between what machines can handle and where human review still drives impact. The real benefit isn’t just reducing the number of incidents; it’s building a system where the same incidents don’t recur.
Conclusion
Cybersecurity debt increases risk and keeps teams stuck in reactive mode. It leads to preventable incidents, audit friction, and time spent on repeat issues. The turning point occurs when teams recover time to address the root causes. Dropzone helps by automating low-value tasks, allowing analysts to focus on improving systems instead of just responding to them. In Part 2, we’ll cover how to measure this shift through ROI and maturity modeling. For now, review your team’s time budget and, if you'd like to see how Dropzone fits, book a self-guided demo to try it out for yourself.















