Key Takeaways
- MTTA is the largest drag on MTTR in traditional SOCs. Human analysts can only handle alerts sequentially, leading to queues, delays, and inconsistent response times.
- AI SOC analysts virtually eliminate MTTA. They acknowledge alerts instantly, begin investigations without delay, and complete them in 3-10 minutes with consistently deep investigations.
- AI automation compresses MTTR end-to-end. AI SOC analysts conduct investigations in parallel and execute automated containment actions, reducing fatigue for human analysts and enabling SOC teams to operate more effectively.
Introduction
Mean Time to Respond (MTTR) is one of the most closely watched metrics in any SOC because it reflects how quickly a team can detect, investigate, and contain threats before damage spreads. It serves as a direct measure of response efficiency, indicating where delays occur and how effectively the team performs under pressure.
Related metrics, such as MTTC (mean time to containment), provide additional perspective on containment speed, which we've covered in detail in a previous MTTC blog post. The challenge for most SOCs is that MTTR reduction is often limited by human bottlenecks, especially when alerts wait for attention or when investigations depend on limited staffing and skill sets.
AI SOC analysts are changing this picture, reshaping how response time is measured and dramatically reducing the delays that once felt unavoidable.
What Are the Phases of MTTR?
.png)
When people talk about MTTR, it's easy to think of it as a single metric. In practice, it's built from several stages:
- Mean Time to Detect (MTTD) - How well detection tools like SIEM, EDR, and NDR are tuned and optimized. High-fidelity alerts make this fast; noisy or misconfigured systems slow it down. In the worst cases, internal detections fail and organizations only become aware from third parties such as law enforcement, partners, or through public data leaks.
- Mean Time to Acknowledge (MTTA) - The time elapsed between an alert being fired and an analyst starting to work on it. This is usually the biggest contributor to MTTR. Alerts arrive faster than analysts can handle, so they sit in queues.
- Investigation - Where analysts gather context across logs, endpoints, and network data to validate a hypothesis and issue a verdict: either benign (false positive) or malicious (true positive). The vast majority of alert investigations are dismissed as benign.
- Containment - The SOC shifts into containment by isolating systems, disabling accounts, revoking sessions, or blocking traffic.
- Recovery - Often handled by forensic and IT teams, which involves fully evicting attackers, restoring systems, and applying fixes such as patching or password resets.
Together, these stages define the full MTTR.
Why Does MTTA Dominate in Traditional SOCs?
Ask any SOC leader where the most time is lost, and you'll almost always hear the same answer: MTTA, or mean time to acknowledge. Detection is handled by tooling, investigation has defined workflows, containment has known playbooks, but acknowledgment is tied directly to human availability. In other words, human resource constraints determine how quickly a SOC can prioritize and start investigation on incoming alerts.
Analysts need to be present, notice the alert, and decide to take it on. That simple human step consistently proves to be the largest drag on MTTR.
Contributing factors include:
- Staffing levels - A small SOC handling enterprise-level telemetry may not touch alerts for hours.
- Workload distribution - Thin staffing or heavy workloads exacerbate the issue.
- Skill distribution - Less experienced analysts may hesitate before engaging, which further delays the process.
Even in larger SOCs with round-the-clock shifts, the distribution of skill levels adds friction. Senior analysts prioritize the most urgent cases, while junior staff may hesitate on complex ones. And no matter how skilled the team is, they can only handle alerts one at a time. Unlike detection systems, human attention doesn't expand, and it doesn't parallelize. That's why MTTA so often dominates the entire MTTR equation.
How Do AI SOC Analysts Eliminate MTTA?

In most SOCs, MTTA is where time seems to disappear. Alerts stack up, analysts are already stretched thin, and even the most skilled responders can only focus on one thing at a time. AI SOC analysts immediately change that situation.
Every alert is acknowledged the moment it's generated. There's no lag, no backlog, no question of whether someone is available. That entire segment of MTTR, often the largest portion, simply disappears.
But acknowledgement is only the first step. AI SOC analysts don't just flag an alert as "seen." They immediately start a thorough investigation, formulating hypotheses about why the alert might be benign or malicious, and then gathering data and context to prove one of those hypotheses out:
- Logs from SIEM platforms
- Endpoint telemetry from EDR solutions
- Identity information from directory services
- Threat intelligence from external feeds
All of this is consolidated and analyzed without waiting for an analyst to initiate the process.
From the second the alert fires, investigation is already in motion. For SOC leaders, this means the response clock starts ticking on analysis, not on waiting.
Can AI SOC Analysts Handle Multiple Investigations Simultaneously?
The other major shift is that a human SOC analyst has to make tough decisions about which alerts to prioritize. AI SOC analysts don't. They can launch multiple investigations in parallel, applying the same level of rigor to each one whether it’s a high- or low-severity alert.
Benefits of parallel investigations:
- No alert sits idle while the team works through a queue
- No important signal is missed because of capacity limits
- Consistent quality across all investigations
The impact is measurable. Typical AI SOC analyst investigations take only three to ten minutes, and the outputs are consistently thorough, structured, and provide evidence, correlated activity, and clear findings.
That level of speed and quality not only compresses MTTR but also gives human analysts confidence that nothing is slipping through the cracks. Strategically, it moves the SOC away from reactive triage and into a mode where every alert gets the attention it deserves, without sacrificing depth or coverage.
How Do AI SOC Analysts Automate Investigations and Containment?
Investigations are where SOC teams often lose valuable time. The minutes spent on investigation represent limited cognitive capacity, the most valuable resource in a SOC. You don’t want to waste this precious resource investigating false positives.
A human analyst faced with a new alert must collect information from multiple systems in order to make a verdict on an investigation:
- Endpoint and cloud logs
- Identity directories
- Access management systems
- Firewalls
- Threat intelligence platforms
Switching back and forth is slow, and when alerts pile up, it quickly becomes a bottleneck.
AI SOC analysts change the flow entirely. As soon as an alert is selected for investigation, they begin collecting and correlating relevant data across systems. Log entries, correlated events, and external intelligence are consolidated without human intervention.
What comes back is not just raw output but an organized record that highlights suspicious links, patterns, and likely root causes. They reason through the findings to see which of their original hypotheses seems most likely.
The advantage of an AI SOC analyst is consistency and speed. Every investigation receives the same structured treatment, regardless of the team's workload or the time of day. The reports AI SOC analysts generate are formatted for action, giving human analysts immediate insight into what matters most when a malicious alert is escalated.
Investigations that previously consumed hours are now often resolved in minutes. At the same time, repetitive manual work is eliminated, reducing the load on human teams and allowing them to devote more energy to judgment and strategy.
What Happens After a Threat Is Confirmed?
Once a threat has been confirmed, speed becomes the top priority. Every minute of attacker access increases the risk of privilege escalation, lateral movement, or data theft. In many SOCs, containment depends on an analyst stepping in to disable an account, block a domain, or isolate a host. That step is rarely instantaneous because it requires awareness and sometimes coordination with other teams.
AI SOC analysts collapse that delay. The moment a threat is verified, they can carry out containment directly:
- Disable compromised accounts
- Block malicious traffic
- Quarantine endpoints
This automation stops the attacker quickly and reduces the chance of further spread.
It is essential to distinguish between containment and remediation:
- Containment halts attacker activity, stabilizing the situation
- Remediation is the follow-up work (reimaging machines, rotating credentials, closing vulnerabilities)
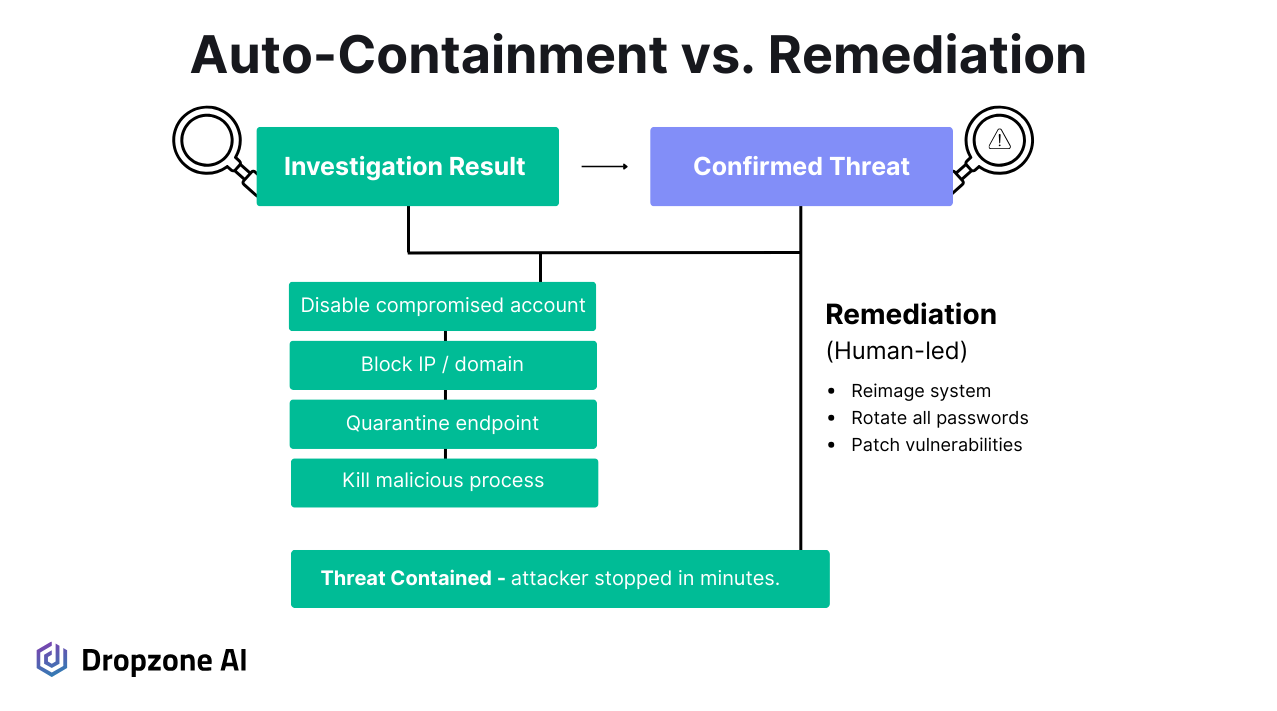
By automating containment, AI SOC analysts provide the human team with the breathing space to manage remediation in a controlled and less stressful manner.
The strategic outcome is significant. Automated containment compresses MTTR by reducing hours of manual work to minutes. It also reduces the pressure on analysts to constantly monitor and intervene, which lowers fatigue and strengthens consistency.
Over time, this shift not only improves response metrics but also enables SOC teams to adopt a more resilient and proactive operating model.
Conclusion
MTTR remains one of the most important performance signals for SOC leaders, but it no longer has to be limited by slow acknowledgment times and stretched investigations. AI SOC analysts reduce MTTR by eliminating the waiting period of MTTA, conducting parallel investigations, and automating containment actions. The result is a faster, more consistent response across every alert.
Looking forward, this shift enables SOC teams to transition from reactive firefighting to a more resilient security posture. To see how this works in practice, visit our self-guided demo.















