In cybersecurity, we're all too familiar with the defender’s dilemma: breaches seem inevitable because while defenders must be right 100% of the time, attackers only need to succeed once. This profound asymmetry isn't just a technological gap—it's a strategic challenge. As the technological arms race with attackers wages on, it’s no longer sufficient to be right 100 out of 100 times. Defenders need to be right 1 million out of 1 million times. Dropzone AI was conceived to tackle this disparity. We are on a mission to transform how Security Operation Centers (SOCs) handle cyber threats by leveraging the power of large language model (LLM)-based autonomous AI agents.
Turning the table with network data
My journey into cyber defense began with my fascination with networks as a rich source of security data. After quitting my Ph.D. in computer science at the University of Washington, Seattle (where I developed new techniques in program analysis and software defenses), I joined ExtraHop Networks, which has the best network streaming parsing technology on the planet. Networks, I believed, could serve as a veritable minefield of invisible tripwires for cyber attackers. I wanted to leverage AI-powered behavioral analytics to create an environment where attackers would have to tread with the utmost caution, thereby shifting the balance of power in favor of the defenders.
Throughout my eight-year tenure at ExtraHop, I led the development of its advanced AI/ML detection capabilities from scratch and spearheaded the transition from network performance monitoring (NPM) to network detection and response (NDR). Forrester recently named Extrahop the leader in NDR, with the largest market presence of over $140m ARR. However, while we were providing comprehensive detection of subtle but suspicious changes in the networks, it became clear over time that innovations in detection alone wouldn’t solve the asymmetry.
“New detections are not as valuable as you think, Edward”
I remember a call in the early days of my tenure at ExtraHop, with a SOC manager of a prominent financial services provider, one of our early adopters. Being the detection product lead, I was in a feedback session with Michael, the SOC manager, about some of the deep learning-based abnormal data movement alerts we were testing with them and why his team was ignoring them. When I brought up the topic, Michael politely but firmly responded, "Edward, I appreciate the math and engineering you guys have put into these detections, but it's not as valuable as you think. Let me show you why." He proceeded to run through a live demonstration of an investigation, from an alert in the SIEM, confirming network telemetry in NDR, pivoting to the EDR, then the file share, and eventually, cross-referencing with the HR system for insider threat possibilities. "You see, Edward," Michael remarked as the stopwatch hit over fifteen minutes, “Surfacing an alert doesn't change the game. You need to help me understand them."
The process of piecing together context from fragmented data sources is complex and time-consuming. Over time, it became clear that the SOCs, for all their alert-detection capabilities, were being drowned in an ocean of alerts, often managing to investigate fewer than 10% of them due to limited resources and bandwidth. There is a stark automation mismatch: as alert generation became more sophisticated and automated, the alert investigation was still mostly manual, causing a substantial bottleneck in security operations. At the time, significant automation of alert investigation was technically impossible. The combinatorial explosion caused by the large permutation of fragmented cybersecurity tooling/data sources, the variety of different alerts, and the organizational-specific contexts required were too much for traditional if-statement-based robotic automation to handle.
A formidable challenge but also a once-in-a-generation opportunity
Fast forward to 2023, IBM Data Breach Report revealed that 83% of organizations experienced more than one data breach, from local hospitals to government agencies. Even the most well-resourced tech company of our era, Microsoft, with a $2.5T market capitalization, was recently compromised by state-sponsored actors without even realizing it for over a month. Microsoft only discovered the breach when a government agency, a customer of theirs, found some tell-tale signs that pointed to Microsoft being breached when reviewing obscure alerts deep in their systems. With the introduction of LLMs, attackers can now perform attacks (from social engineering to vulnerability discovery) more efficiently at a much larger scale. It’s clear the asymmetry between cyber defenders and attackers is growing faster than ever before. We have reached an inflection point where humans alone can’t keep up anymore, and a step function in the automation of security operations is desperately needed.
Fortunately, the same LLMs that attackers are weaponizing can also be used by defenders as a new and superior way to automate cognitive reasoning. LLMs can now be utilized to build modules that mimic human reasoning for tasks that were previously not automatable with traditional programming. What if we could harness the cognitive reasoning power of LLM to encode cybersecurity know-how and expertise into AI software? Could we create a technology that would handle the operational toils, leaving human analysts free to focus on more critical projects?
Motivated by what feels like a seismic shift in the cybersecurity landscape, I bid ExtraHop a fond farewell and embarked on a new journey: to create Dropzone AI. The vision was clear - reinforcing SOCs with AI so they can better operate and defend as if they had an unlimited number of tier-1 analysts.
Reinforce your SOC with Autonomous AI Agents
At Dropzone AI, we are building AI agents capable of performing the first level of analytical work in SOCs autonomously. The AI agents mimic expert human analysts’ decision-making process, understand the intricacies of cybersecurity, and adapt to an ever-changing threat landscape to thoroughly and autonomously investigate all alerts. SOCs send their alerts to our system, and for every single alert, Dropzone will autonomously perform an end-to-end investigation (swivel chairing across their existing security stack) and generate an investigation report that details the related context and whether the alert should be treated as a true positive or false positive. These agents work 24/7 and never tire, ensuring no threat goes unnoticed and leaving the human analysts free to focus on the top priorities.
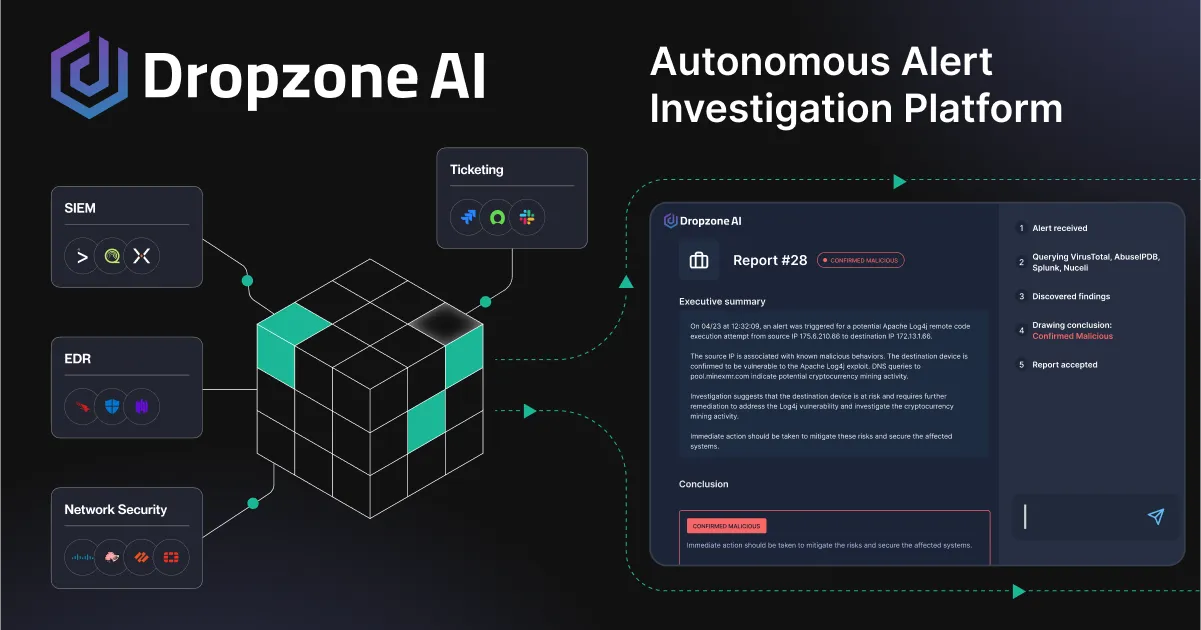
We believe our technology has the capacity to, for the first time, materially level the playing field in cyber defense. Today we are publicly launching the company and announcing our $3.5m seed funding, led by Decibel Partners and joined by Pioneer Square Ventures. Notable angel investors such as Oliver Friedrichs, CEO of Pangea Security and founder and former CEO of Phantom Cyber, Jon Oberheide co-founder and former CTO of Duo Security, and Jesse Rothstein, co-founder and CTO of ExtraHop, also participated in the round. We plan to grow our engineering team and accelerate the development of our technology to support the most common alert types and security stacks.
As deep technologists, we are very proud of what we have already built, and today we would like to invite you to experience the power of AI SOC analysts yourself. We have hooked up our technology to scan@try-dropzone.ai to have it analyze and generate analysis reports of any suspicious email forwarded to it. Please give it a spin by challenging it with phishing emails or ask for a sample and see how it comprehensively investigates suspicious emails by tapping into a dozen different data sources and tools. And check out our website to learn more, stay in touch, or join our waitlist. Thank you for joining us on this journey, and stay tuned for more exciting updates from the frontline of AI-enhanced cyber defense.















