Introduction
Security teams often have the right tools, such as SIEM, EDR, identity platforms, and cloud security, but still feel underperforming. The issue isn’t the tooling itself. It’s that most security teams don’t have the time to put these excellent tools to the best use. Without correlation and analysis, context gets lost between systems, data remains siloed, and alerts sit waiting to be investigated. In this article, we’ll break down why operationalization matter so much to security operations, where teams typically lose ROI, and how tools like Dropzone AI can help you turn existing investments into outcomes you can measure.
The ROI Problem in Security Operations
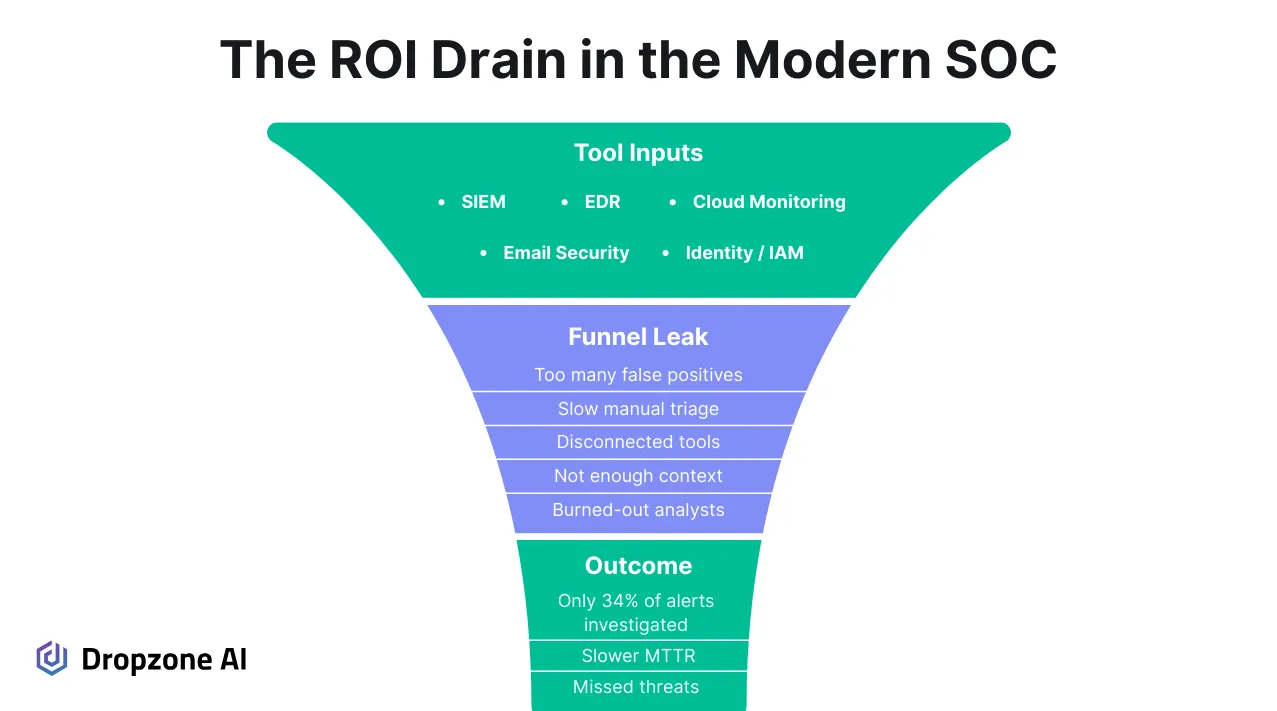
Security teams run a wide array of tools across detection, identity, and cloud monitoring, but most of those tools rely on people having time to use them and they don’t talk to each other in meaningful ways. More importantly, few teams have the time to make use of the full potential of these tools. When alerts hit the queue, analysts must manually chase context across multiple consoles to validate what they see—and they have to do it fast or risk falling behind.
Despite analysts’ frantic work, this manual workflow actually slows everything down and directly impacts how long it takes to detect, triage, and escalate real threats. Context switching burns time, and when platforms operate in silos, it’s easy to miss links between signals that should be connected. As a result, valuable telemetry often gets ignored because it’s too time-consuming to access or correlate on the fly.
These inefficiencies show up in the metrics that matter. Mean Time to Detect (MTTD), Mean Time to Conclusion (MTTC), and overall alert throughput suffer, regardless of how advanced the tools are. According to the latest SANS SOC Survey, 66% of teams say they can’t keep up with alert volume, even with significant investment in tooling. The problem isn’t the tech, it’s the lack of coordination between them.
Unlocking Value Through Integration and Context
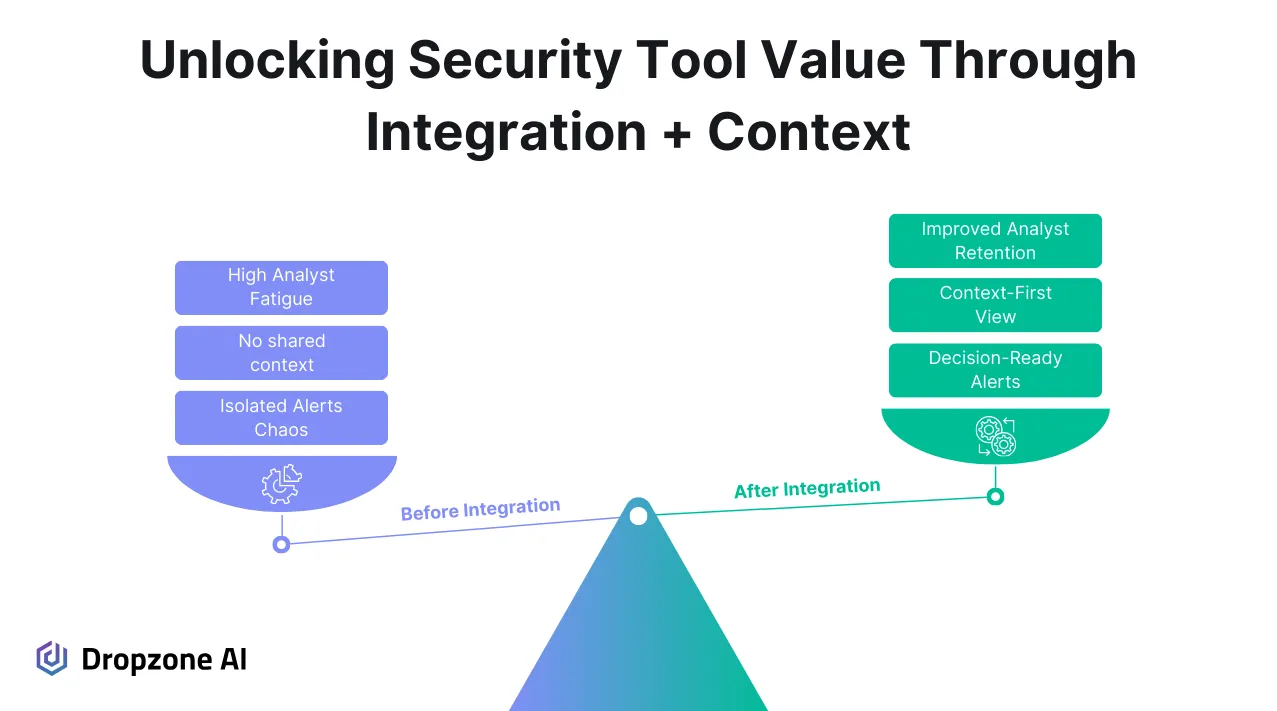
It’s easy to feel like your tools should be doing more. Most teams already have what they need: SIEM, EDR, identity, cloud logging, and vulnerability scanners, but those systems rarely communicate in a way that makes investigations easier.
The burden often falls on analysts to correlate all these data manually during an investigation. That creates delays, especially when they chase alerts across different consoles with inconsistent data formats and no shared timeline.
SIEMs are built to centralize events, but they aren’t built to interpret them and can’t access business systems to gather necessary context. For example, an unusual login alert from your identity provider might come through. Unless you can correlate that with recent file access logs, EDR telemetry, changes to group membership, MFA behavior, or even an employee’s calendar it’s hard to know if the activity is suspicious or expected. The context exists, but it’s scattered across tools and systems that don’t reason together. Without integration, you're left piecing it together by hand.
This is where AI SOC analysts make a measurable impact. Alert triage becomes more reliable when you have an autonomous AI SOC agent that is pre-trained to use the tools that you have in place and gather data from business systems like Google Workspace, Office 365, and Jira.
AI SOC analysts can track a suspicious login, pull in the associated process tree, check against threat intel, and review file access patterns all in one flow. That kind of AI-powered automation directly reduces Mean Time to Triage (MTTC), improves incident accuracy, and gives security leads cleaner metrics to report upstream. Most teams don’t need to add more tools; they need AI agents to use the ones that they already have in place.
How Dropzone AI Helps You Maximize Toolset ROI
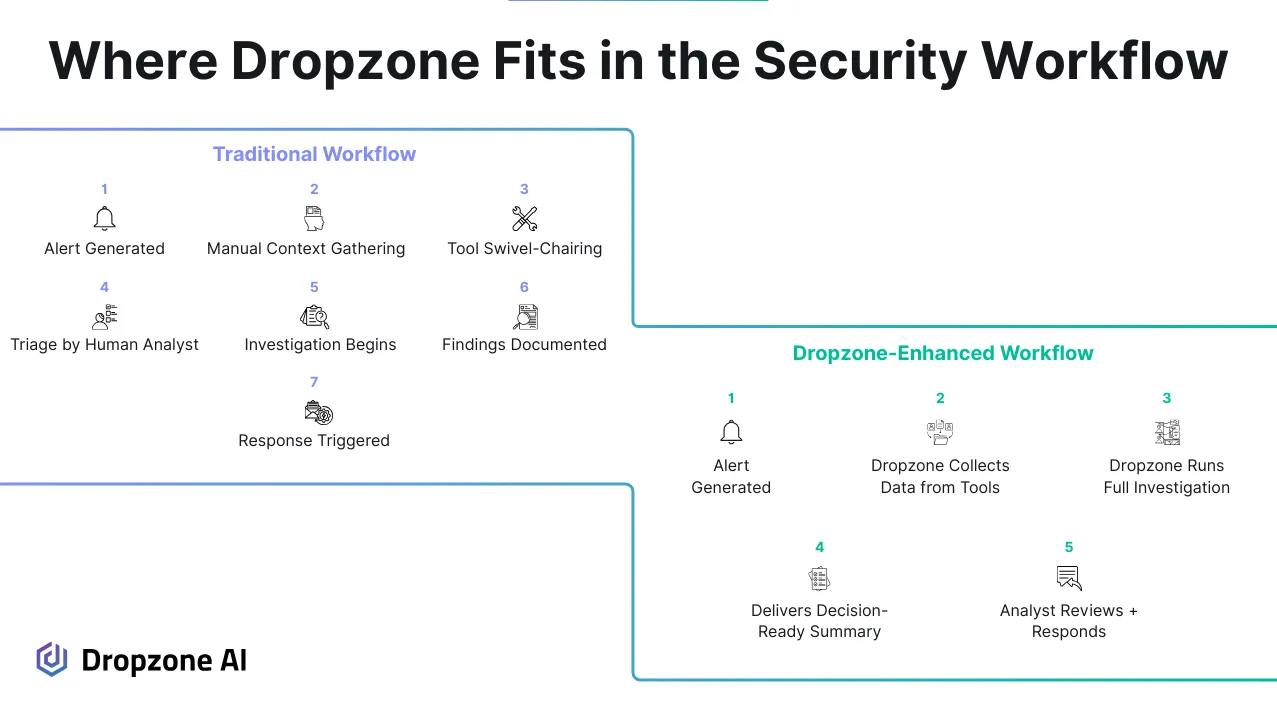
Dropzone AI is pre-trained to expertly use the platforms you're already running, no rip-and-replace, no re-architecting. It supports over 70 tools and business systems, including Microsoft Sentinel, Splunk, CrowdStrike, Okta, Google Workspace, and AWS.
Once connected, Dropzone pulls data from SIEM, EDR, identity, and cloud tools, and launches full investigations using recursive reasoning. It checks authentication patterns for anomalies, verifies account roles and permissions, analyzes recent group changes, and reviews access patterns for suspicious behavior. It also references past investigations to identify recurring attack patterns and looks at cloud API calls to flag unauthorized access or abuse.
Instead of passing alerts through for manual triage, Dropzone expertly uses the same security tools and business systems that your human analysts do to deliver decision-ready investigations. Each report includes a clear conclusion, timeline of observed activity, and technical details such as process trees, privilege escalation attempts, file hash lookups, and suspicious API calls. It can safely visit websites linked in suspected phishing emails to determine if they are malicious. The AI even interviews users to confirm activity legitimacy, checks file sensitivity when external sharing is detected, and deobfuscates suspicious payloads to assess intent. It verifies roles and permissions, checks authentication patterns, traces process execution, and flags defensive evasion through policy change reviews, without requiring analysts to pivot between consoles or run manual queries.
Dropzone also reviews email headers and metadata to confirm whether external file shares were legitimate, hunts for persistence mechanisms, and looks up IP and domain reputation in real-time. This level of context eliminates the guesswork from triage and makes your existing toolset far more efficient. Analysts can focus on evaluating conclusions, not gathering evidence. Teams report measurable gains across MTTC, alert fidelity, and time-to-response, while dramatically reducing the number of alerts requiring human review. If you’re working to reduce fatigue, improve your KPIs, or get more out of your current tech stack, Dropzone AI ensures that all your security toolset investments are put to good use.
Conclusion
You don’t need to expand your stack; you need to make it work smarter. When you have AI SOC analysts expertly using your security tools, you reduce manual overhead, accelerate investigation timelines, and avoid duplicate work. Dropzone AI plugs into the tools you trust and turns them into a coordinated system that delivers consistent, decision-ready output. It’s how teams are shrinking MTTC, cutting false positives, and giving their analysts more time to focus on higher-impact work. If you’re ready to see how well your current tools can perform with better coordination, check out the Dropzone AI self-guided demo and see how it works.