What is Recursive Reasoning in AI Security Systems?
In traditional computing systems, logic follows a linear path: input goes in, processing happens, and output comes out. However, recursive reasoning in agentic AI systems takes a fundamentally different approach. Rather than using static if-then logic, recursive reasoning creates iterative feedback loops where outputs from one stage of processing become inputs for subsequent stages.
Recursive reasoning enables an agentic AI system to:
- Generate an initial alert hypothesis and investigation path
- Gather evidence and findings needed to test the hypothesis
- Reason to decide if it has enough information for a conclusion
- Form an updated hypothesis, if needed
- Repeat until reaching a high-confidence conclusion
- Extract details to add to context memory
This mirrors how expert human analysts think—they don't follow rigid playbooks but rather adjust their approach as new evidence emerges, revisiting earlier assumptions when necessary, using frameworks such as the OSCAR methodology.
Why is Recursive Reasoning Important for Cybersecurity?
What makes recursive reasoning particularly powerful for cybersecurity is its ability to handle complexity without predefined rules. Instead of requiring security teams to anticipate every possible attack scenario and code appropriate responses, recursive reasoning allows AI systems to adapt dynamically to the types of unpredictable investigations that SOCs see day-in, day-out. An analogy would be self-driving cars: If these cars only needed to drive on test tracks, then their behavior could be programmed more easily. What makes self-driving cars challenging is the variety of situations they face in real-world traffic.
The Limitations of Traditional Security Automation
Before diving deeper into recursive reasoning, it's worth understanding why traditional security automation approaches often fall short in modern SOC environments.
Security Orchestration, Automation, and Response (SOAR) playbooks have served security teams well for certain tasks, particularly for automating routine remediation or policy-based responses. However, they come with significant limitations:
- Complexity spirals: As SOAR playbooks attempt to handle more sophisticated scenarios, they become exponentially more complex to maintain
- Brittle responses: Playbooks can only respond to threats they were explicitly designed to handle
- Resource-intensive: Maintaining comprehensive playbooks requires dedicated automation engineers
- Limited investigation depth: Most enrichment playbooks provide basic context but require humans to perform the actual investigation
Consider a typical firewall alert playbook. It might automatically check an IP against threat intelligence, enrich it with basic metadata, and then hand off the investigation to a human analyst for the remaining 95% of the investigation work. While valuable, this level of automation has not fulfilled the promise of eliminating routine alert triage leading Gartner to write that the SOAR category is obsolete.
How Do AI SOC Analysts Use Recursive Reasoning?
AI SOC analysts built with recursive reasoning capabilities, like Dropzone AI, fundamentally change the security automation equation. Rather than following predefined steps, these systems employ a multi-stage investigation process that mirrors expert human reasoning:
1. Initial Understanding and Context Gathering
When an alert first arrives, the AI assesses the basic alert details and immediately begins forming hypotheses about potential causes—both benign and malicious. This initial hypothesis generation isn't rigid; it's a starting point that will evolve as more evidence emerges.
2. Dynamic Evidence Collection
Based on initial hypotheses, the AI system autonomously determines what additional evidence it needs to confirm or refute each possibility. This might include:
- Querying logs from various security tools
- Checking user activity patterns
- Looking up roles and permissions of accounts
- Referencing IPs, users, or other entities in context memory
- Examining network traffic
- Correlating with other alerts or historical data
The AI doesn't follow a fixed pattern of evidence collection; instead, it adapts its approach based on what it discovers at each step. This is where specialist agents come into play. They are pre-trained agents that are skilled in the particular task at hand, whether understanding how to expertly query a particular security tool, safely analyze a PDF attachment or landing page, or examine a process tree to look for malicious activity. By using pre-trained specialized agents for discrete tasks, AI SOC analysts are able to minimize hallucinations and improve accuracy.
3. Recursive Analysis and Hypothesis Refinement
As evidence accumulates, the AI continuously reassesses its hypotheses through recursive reasoning loops. This is where the real power of the approach becomes apparent:
- If a piece of evidence contradicts an initial hypothesis, the AI takes this information into account and adjusts its thinking
- When new evidence suggests additional investigation paths, the AI pursues them
- The system can return to earlier assumptions and revise them as the investigation unfolds
For example, what starts as a suspicious login investigation might recursively expand to include GitHub access patterns when the AI discovers evidence of potential code exfiltration.
4. Confidence-Based Conclusion
After multiple recursive investigation loops, the AI reaches a conclusion. This final determination includes not just a "benign" or "malicious" verdict, but a comprehensive explanation of the reasoning process, evidence collected, and recommended next steps.
How Does Context Memory Improve Security Alert Analysis?
Dropzone AI's Context Memory system works hand-in-hand with recursive reasoning to dramatically improve alert investigation accuracy. While recursive reasoning provides the investigative methodology, Context Memory supplies the organizational knowledge that makes investigations contextually relevant to your specific environment.
Context Memory serves as an organizational knowledge repository that:
- Stores environment-specific details: Approved VPN services, IP ranges used for test and development, scheduled maintenance windows, expected user behaviors, and other contextual information
- Builds relationships between entities: Users, accounts, devices, IP addresses, and expected connections between them
- Develops over time: The system continuously learns from past investigations and feedback
When combined with recursive reasoning, Context Memory enables Dropzone AI to make increasingly sophisticated decisions about what's normal versus suspicious in your environment. For example:
- A recursive reasoning loop might identify an unusual login from an unfamiliar IP address
- Context Memory could recognize this as a known contractor's VPN endpoint
- This context allows the investigation to shift toward validating expected activity patterns
- The reasoning loop adapts based on this new contextual understanding
According to Dropzone AI's documentation, organizations implementing AI SOC Analysts see MTTC (Mean Time to Conclusion) decrease by 75-95%, with typical investigations reduced from 20-40 minutes to just 3-11 minutes. The synergy between recursive reasoning and Context Memory also significantly reduces false positives, allowing SOC teams to process more alerts with greater speed. This means that security teams can spend more time on preventative security tasks that harden the environment, such as reviewing security controls, prioritizing vulnerability remediation, detection engineering, improving telemetry collection, and incident response planning.
Real-World Examples: AI Reasoning in Action
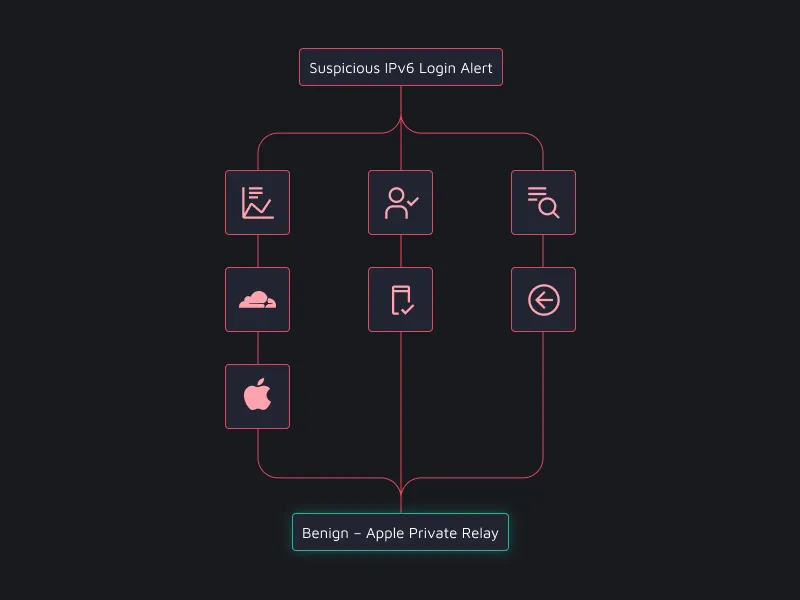
Example 1: Anonymized IP Alert Investigation
In a real-world case described in blog "Unmasking the Relay: Navigating Alerts Triggered by Anonymized IP Services," the Dropzone AI system investigated an alert triggered by a login from an unusual IPv6 address that initially appeared suspicious. Through recursive reasoning, the AI:
- First identified the IP was managed by Cloudflare, a hosting provider often associated with anonymization services
- Through deeper analysis, determined the IP belonged to Apple Private Relay
- Examined historical login patterns to see if similar IPs had been used previously
- Analyzed the user agent string to confirm an iPhone device consistent with Apple Private Relay, a privacy-focused proxy service
- Verified that the user account in question interacted with other IPv6 addresses associated with Apple Private Relay in the past
This recursive investigation process saved approximately 15 minutes of analyst time and correctly identified the alert as benign despite its initially suspicious characteristics. The AI's ability to continuously refine its investigation approach based on emerging evidence was key to reaching the accurate conclusion.
Example 2: Suspicious Command Execution in Kubernetes
In another case study from the blog "Dropzone AI for Datadog: Investigate Every Alert Automatically," the Dropzone AI system investigated a potential security incident involving command execution inside an AWS EKS pod. The recursive reasoning-powered investigation process included:
- Identifying container and pod details to establish environment context
- Querying logs to extract all commands executed during the alert window
- Analyzing behavioral patterns to determine if the source IP had executed similar commands before
- Linking the IP to an internal engineer based on historical activity
- Concluding the activity was benign based on the combined evidence
This investigation demonstrated how recursive reasoning enables the AI to adapt its approach dynamically, following evidence trails across multiple systems and timeframes to reach a well-supported conclusion.
How AI SOC Analysts Balance False Positives and Detection Coverage
One of the most significant impacts of recursive reasoning in SOC operations is its ability to dramatically reduce false positives without increasing the risk of missing real threats. As such, AI SOC analysts augment other efforts to reduce false positives, such as detection engineering. However, there can be a hidden cost to detection tuning that AI SOC analysts can help with:
- Traditional detection tuning forces SOCs to make trade-offs between precision (reducing false positives) and recall (avoiding false negatives)
- This creates a hidden cost: well-tuned detections that reduce alerts also create detection gaps that attackers can exploit
- By using AI-powered recursive reasoning to investigate every alert, SOCs can run more sensitive detection rules without overwhelming analysts
This approach allows security teams to:
- Add experimental or test detections previously considered too noisy
- Increase sensitivity on existing detection rules
- Eliminate exclusions that create security blindspots
By automating thorough investigations of every alert through recursive reasoning, Dropzone AI enables SOCs to identify genuine threats more consistently while reducing the burden on human analysts—effectively solving the precision-recall trade-off that has long plagued security operations.
Business Impact: Why AI SOC Analysts Matter
For SOC teams and security leaders, the shift to AI SOC analysts that use recursive reasoning delivers tangible benefits:
- 90% reduction in investigation time: By automating the entire investigation process, not just initial enrichment, Dropzone AI reduces Mean Time to Conclusion (MTTC) by up to 90%
- Complete alert coverage: Every alert receives a thorough investigation, eliminating the common problem of alert backlog
- Reduced false positives: Contextual understanding and recursive analysis significantly reduce false positive rates
- Consistent investigation quality: Each alert receives the same thorough investigation approach, regardless of analyst availability
- No playbook maintenance: Security teams can focus on strategic initiatives and proactive security tasks rather than maintaining complex automation rules

For MSSP providers, Dropzone AI's autonomous SOC analyst—which leverages recursive reasoning as one of its key capabilities—enables scaling service delivery without proportionally increasing analyst headcount. This AI solution allows MSSPs to handle more client alerts, provide consistent investigation quality across accounts, and maintain competitive service levels even during peak demand periods—critical advantages in today's challenging talent market.
Conclusion: The Future of SOC Operations
Recursive AI reasoning represents a paradigm shift in how security operations centers handle alert investigation. By moving beyond rigid playbooks to embrace dynamic, self-refining investigation processes, AI SOC analysts like Dropzone AI unlock unprecedented efficiency and thoroughness to threat detection and response. As security teams continue to face growing alert volumes and increasingly sophisticated attacks, recursive reasoning will become an essential capability in the modern SOC toolkit.
Ready to see how recursive reasoning can transform your security operations? Try our self-guided demo of Dropzone AI's autonomous SOC analyst in a real environment. This interactive experience lets you review end-to-end autonomous alert investigations, see how our AI analyzes threats and collects evidence without manual effort, and evaluate the reasoning process firsthand.