Key Takeaways
- Slow incident response carries a measurable financial cost. IBM estimates unresolved incidents cost ~$800 per hour on average, making delays in high-severity investigations a significant risk factor. We propose a simple model to measure your organization's risk.
- Even modest improvements in response time can yield large savings. Reducing mean time to respond (MTTR) by just a few hours per critical incident can translate into thousands of dollars in risk reduction annually.
- Security ROI should be framed in business terms, not just technical gains. Clear metrics like MTTR, alert volume, and cost-per-incident help justify AI investments to budget holders.
Introduction
Most SOCs deal with high alert volumes but don't always quantify the cost of slow response times. When an incident remains unresolved, it extends the window for attacker movement, data exposure, and operational disruption.
IBM research estimates that each hour of delay during a breach can cost around $800. If even a small fraction of incidents are high-severity, the financial impact adds up quickly.
This article presents a simple model to calculate that risk. It shows how targeted time savings, especially during triage and containment, can translate into measurable, defensible savings when AI accelerates those phases with autonomous alert triage and investigation, such as provided by Dropzone’s AI SOC agent.
What's the True Cost of Unresolved Incidents?
The Hourly Price Tag of Security Incidents
Slow response times in security operations can quietly generate large financial risk. IBM's data shows that every hour a breach remains unresolved, it costs organizations an average of $800.
This number reflects a range of direct and indirect consequences, from prolonged exposure and operational disruption to post-incident recovery and remediation efforts.
The Impact of High-Severity Incidents
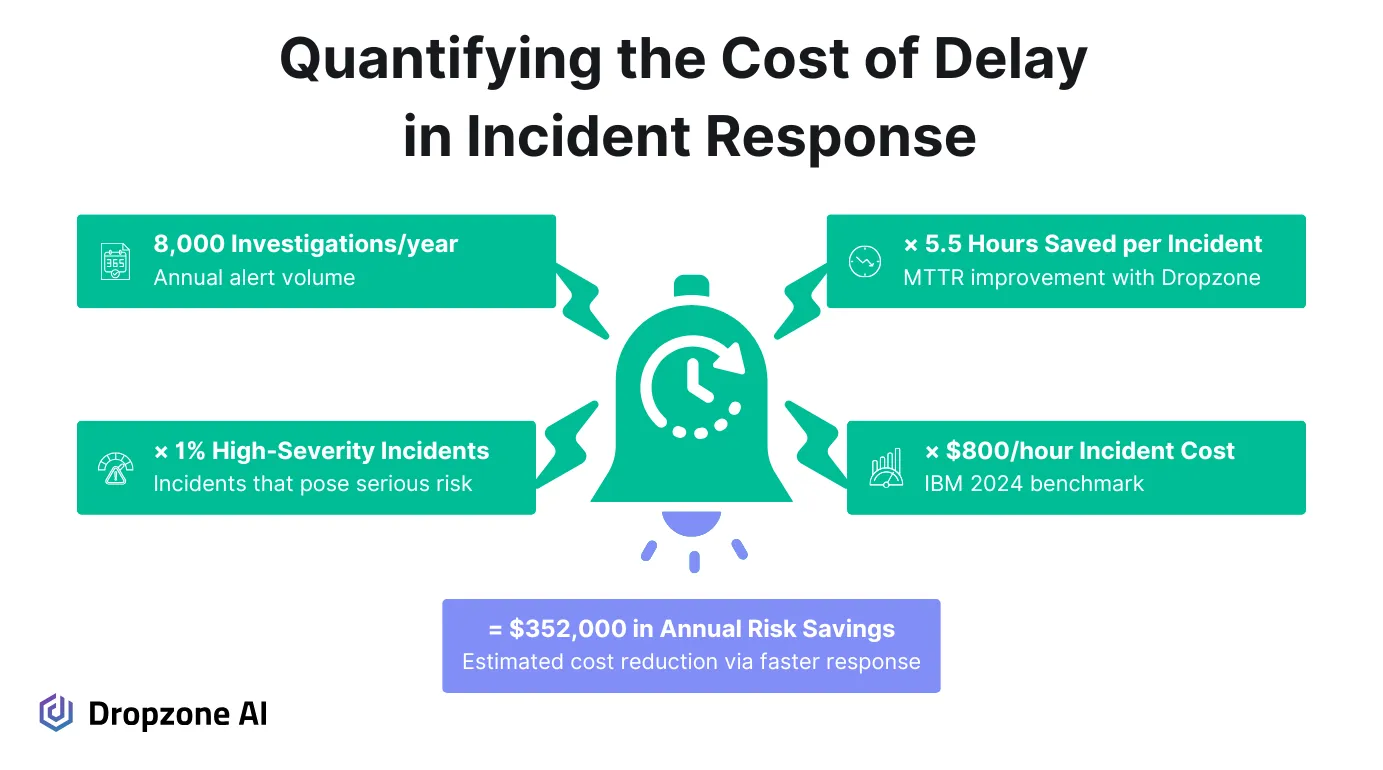
Even if the number of high-severity incidents is small, the cost impact is still material. If only 1% of 8,000 annual investigations are considered high-severity, that's 80 incidents a year where delays matter.
If your team takes hours to move from detection to containment, those hours stack up fast.
Quantifying Time Savings
Some teams have reduced their mean time to respond (MTTR) in purple team exercises from six hours to thirty minutes. That's a 5.5-hour reduction per incident.
Multiply that 5.5 hours across even a small number of high-severity alerts, and the operational value becomes easy to quantify.
The Financial Calculation
Here's the math: 8,000 investigations per year × 1% high-severity rate × 5.5 hours saved per incident × $800/hour = $352,000 in potential annual risk reduction. This is a conservative model based on industry standard assumptions. Feel free to adjust according to your organization’s risk model.
The point is that even small improvements in triage or containment can make a noticeable financial difference at scale.
This shows that time isn't just a technical variable; it's a risk vector. When you reduce the time an attacker has inside your environment, you reduce the window for damage. When that time is decreased consistently, the economics of breach response shift in your favor.
Where the Time and Cost Savings Come From
Immediate Mean Time to Acknowledge (MTTA)
One of the biggest areas of time savings will come from the fact that AI SOC analysts can get started on investigations immediately.
Typically, alerts will sit in a queue until a human analyst picks it up to start the investigation. This is measured as mean time to acknowledge (MTTA) and is usually one of the largest components of MTTR, especially in understaffed SOCs.
Download this ebook to learn about MTTA, MTTD, MTTR, and how a new metric called mean time to conclusion (MTTC) can help you measure real SOC efficacy.
Internal vs. External Detection
Another point to consider is that many incidents are detected by outside third-parties such as law enforcement or industry partners, and then brought to the attention of the SOC.
Verizon’s 2025 DBIR found that 34% of security incidents were discovered by "External" means. According to Mandiant's 2024 M-Trends Report (covering 2023 data), 54% of compromised organizations first learned of the compromise from an external source.
Autonomous AI-driven alert investigation can identify true positives in low-priority alerts that are often ignored, thus dramatically speeding up detection.
Automated Context Gathering
Investigation speed improves when teams don't have to hunt for basic context. When an alert is received, Dropzone AI SOC agent automatically gathers and presents relevant information, like recent system activity, user behavior, and threat intelligence.
The Dropzone AI system can even automate user interviews via Slack and Microsoft Teams to gather contextual details needed to close an investigation.
This context gathering reduces the need for analysts to manually pivot between tools or initiate redundant queries to get a complete picture.
Reduced Alert Fatigue
It also helps reduce repetitive work. Analysts spend less time triaging alerts that are false positives or noise.
The system reduces decision fatigue by filtering out what doesn't matter and flagging patterns worth attention. That means analysts stay sharper longer and can respond more consistently throughout the day.
Advanced Correlation Capabilities
The AI doesn't just enrich alerts—it connects related signals across logs, endpoints, and identity systems. That correlation shortens the time between detection and containment.
In purple team tests conducted by Dropzone AI customers, incident response time improved by a factor of five. That gain came without increasing headcount or adding new tools to the stack.
Broader Operational Benefits
The operational benefits extend beyond just speed. Faster investigations mean less risk exposure, but they also improve internal reporting, reduce stress during audits, and support team retention.
Security teams that run lean need this kind of efficiency to maintain performance over time without burning out.
Validating ROI and Framing the Budget Conversation
Use Conservative, Defensible Assumptions
To get AI investments approved or renewed, security teams need to present results in a way that resonates outside of technical circles. That starts with using conservative, defensible assumptions.
If you estimate 5.5 hours saved per incident and use IBM's $800/hour breach cost multiplier, you're working from widely accepted data points that are hard to dispute.
Time savings will come from improved chances of detecting an incident internally (as opposed to hearing about it from a third party) and in reduction in mean time to acknowledge, or the time an alert spends uninvestigated in a queue.
Calculate Based on Your Actual Volume
It helps to run the numbers on your actual investigation volume. Even if just 1% of alerts are high-severity, the math adds up quickly.
Showing how a small time reduction scales into a six-figure savings model gives stakeholders a clearer view of what they're funding.
Translate Technical Metrics to Financial Impact
Translate operational improvements into financial impact. Instead of saying "we reduced MTTR," say "we reduced high-risk exposure time by 5.5 hours per incident, which aligns to $X in avoided breach costs annually."
Most budget holders want a clear connection between funding and risk reduction. The more direct that link is, the better the conversation goes.
Develop Internal Tracking Metrics
You can go one step further by developing internal metrics that track how security outcomes shift over time. Examples like:
- "Cost per high-severity delay"
- "Mean analyst time per alert"
- "MTTR delta" before and after deployment
These give you hard numbers to present during budget planning. They also make it easier to compare tools in a repeatable way.
If you have the resources, you can conduct regular purple team exercises to measure SOC efficacy and MTTR.
Maintain a Focused Narrative
Finally, keep the narrative tight. Decision-makers want to know what changed, what it saved, and how it supports overall risk posture.
Show them measurable progress. Skip the vague promises and go straight to outcomes. That's what drives funding decisions.
Conclusion
AI that reduces response time can directly influence how much risk remains active in your environment. Shaving a few hours off high-severity incidents, even if they make up only 1% of total alerts, can prevent thousands of dollars in potential loss each year.
Security leaders are asked to quantify the impact and justify the budget with data. Time-to-response, investigation depth, and alert coverage are measurable areas where AI can make a difference.
Start with your current numbers, apply industry benchmarks, and use the deltas to frame an operational ROI story. Try our self-guided demo to see how this Dropzone AI plays out in real scenarios.















