An uninvestigated alert in your queue exists in a kind of quantum state: it's simultaneously benign and malicious until you investigate it, at which point it collapses into one state or the other. The problem is that the process of investigation takes time, and most of these alerts end up being false positives. Dropzone’s AI SOC analyst does this initial triage for you, investigating every alert as soon as it hits the queue. In this blog post, we’ll take a look at a Microsoft Defender for Cloud Apps alert that Dropzone AI recently investigated.
Unusual Login Alert: Benign or Malicious?
When Dropzone AI caught wind of a high-severity alert involving a user logging into Microsoft Exchange Online from an unusual overseas location, alarm bells naturally rang. A high-value user, with activity flagged as suspicious due to geographical anomalies, is exactly the kind of scenario that seems malicious at face value. But digging deeper into alert logic sometimes reveals the story isn't quite what it appears to be. Here's how Dropzone AI conducted a step-by-step analysis of this intriguing case, eventually concluding that a seemingly suspicious event was, in fact, benign.
Alert Investigation Steps

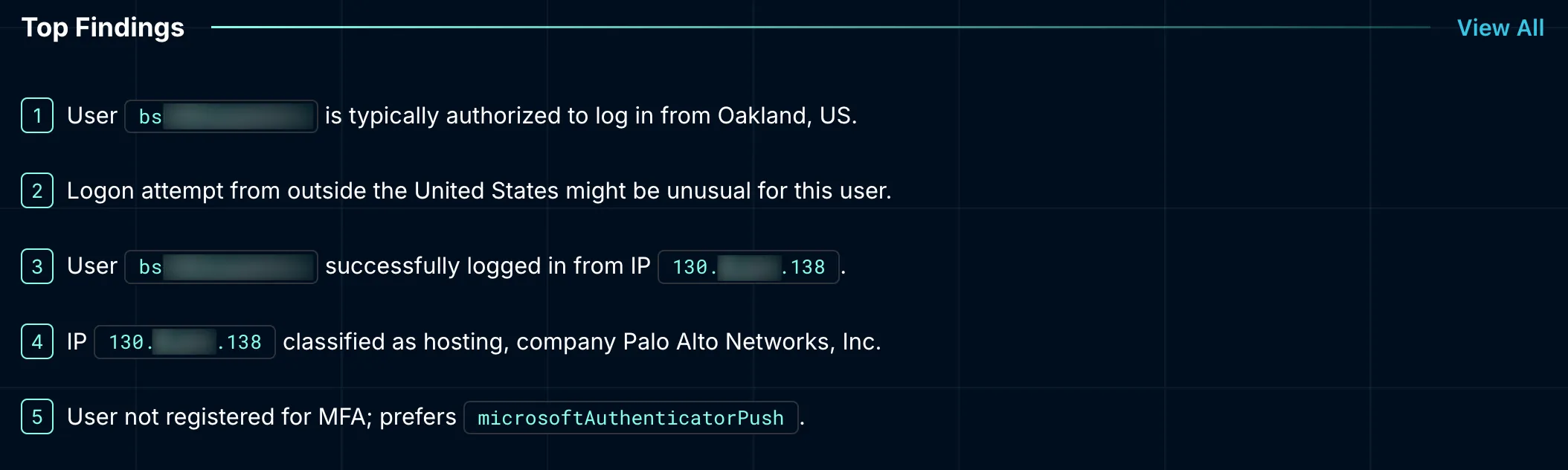
At the start of the investigation, Dropzone AI immediately took note that the user appeared to have logged into Microsoft Exchange Online from an external IP. This prompted the Suspicious Activity policy in Microsoft Defender for Cloud Apps to fire due to login activity from outside the United States. This was unusual given the user’s typical logins originated from Oakland, California.
With this initial context, Dropzone AI began methodically assessing the entities involved, starting with the details of the user account itself.
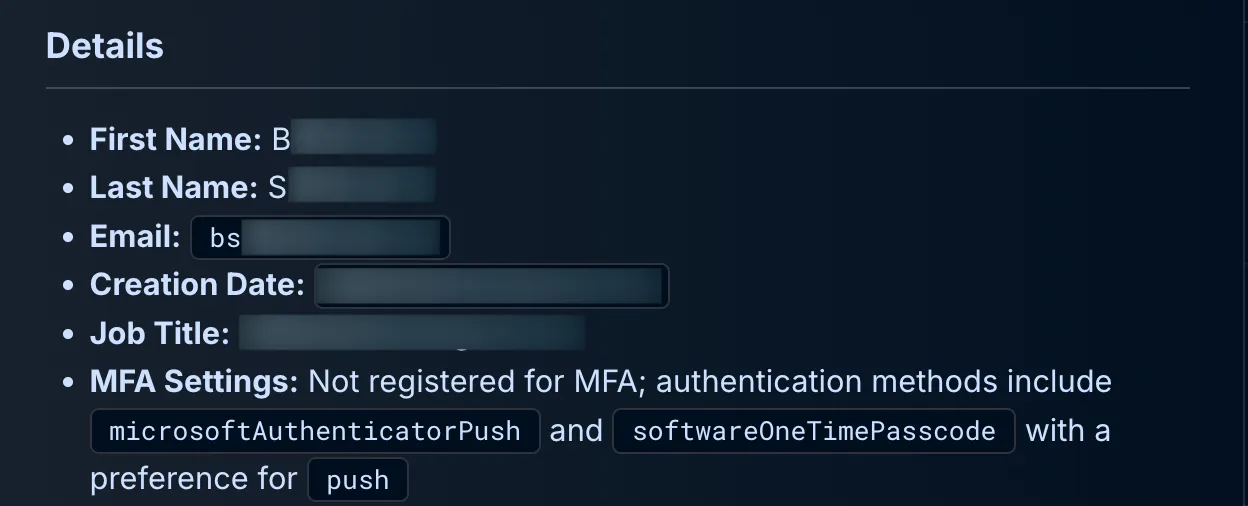
Examining Azure Entra user details showed that the user was created as a user several years prior, with access to numerous internal teams (not displayed). However, an important red flag was present: the user was not currently registered for Multi-Factor Authentication (MFA), a practice strongly recommended to secure such high-level accounts.
Next, Dropzone AI reviewed the user’s login IP addresses over the prior 30 days. This revealed two notable IPs: 130.x.x.138, a Palo Alto Networks address associated with a trusted corporate VPN (GlobalProtect), and another, 205.x.x.37, tied to Panasonic Avionics Corporation, a known inflight internet provider. The historical logs indicated frequent successful access from those IPs, confirming regular, legitimate use over time.
Considering this, it became clear the “unusual” IP address had actually been frequently utilized by the user previously without incident, strongly indicating benign activity.
To more thoroughly verify this suspicion, Dropzone AI examined the IP enrichment information. The IP in question from Palo Alto Networks is classified as legitimate business-hosted infrastructure, matching known corporate VPN solutions frequently utilized by authorized personnel. Likewise, Panasonic Avionics Corp’s IP suggested the user might be traveling and connecting via airplane Wi-Fi—another entirely legitimate context for seemingly suspicious overseas logins.
Further, Dropzone AI referred to historical operational context logs, which clearly stated the user typically logs in from Oakland, but also showed previous cases of legitimate, international usage due to travel and secure VPN connection, documented under a separate internal investigation. This additional context from earlier investigations helped Dropzone AI decisively reinforce its conclusions.
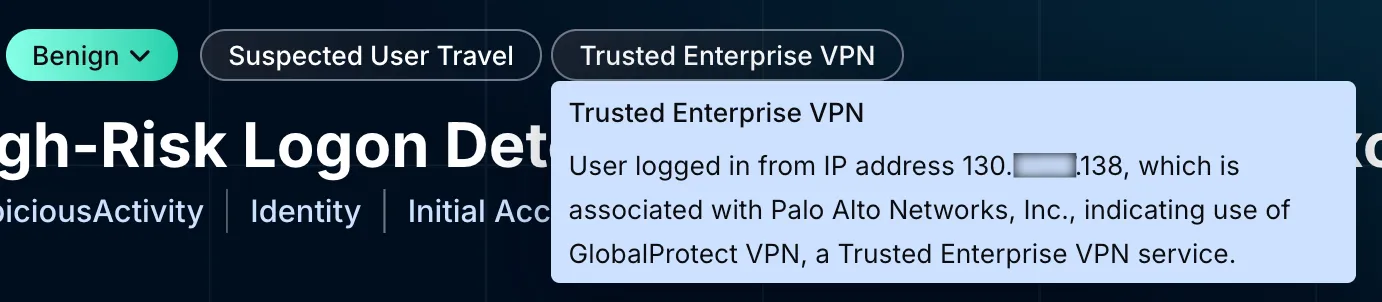

At this point, the analysis pivoted to categorizing insights. Two Dropzone AI insight tags directly aligned with the current findings—“Trusted Enterprise VPN” for Palo Alto’s GlobalProtect and “Suspected User Travel” due to Panasonic Avionics inflight Wi-Fi usage. These quickly explained to the human analyst reviewing the investigation why the activity occurred—the user was traveling internationally and securely logged in via legitimate, known IP addresses and VPN access, negating the initial concerns about malicious behavior.
With all these findings, Dropzone AI confidently determined that the alert could clearly be considered benign, and the activity matched the established pattern of behavior historically observed for this user.

Takeaways for the SOC
From suspicious alert to firm benign classification, Dropzone AI's investigative process shows how security analysis transcends simple geographic checks or IP reputation lookups. It highlights how crucial deeper historical context, IP enrichment understanding, and thoughtful behavioral analysis are when determining outcomes for high-severity alerts. The combination of detailed context memory, consistent user behavior patterns, and legitimate VPN use can turn an initially concerning incident into just another case of a traveling executive securely accessing critical resources.
Want to experience the power of context-rich investigations across other kinds of alerts and scenarios? Check out Dropzone AI's interactive demos for different alert types and experience firsthand how smarter investigations yield better, faster decisions.















