By the Numbers
- 75% of SOC time consumed by reactive tasks (Osterman Research, 2024)
- Only 25% of time available for proactive security work
- 90% reduction in manual triage time with AI SOC agents
- 20+ hours per analyst reclaimed weekly
- 10X increase in alert handling capacity
*Sources: Osterman Research Survey 2024, Dropzone AI Customer Data
The Reality: Reactive Work Dominates SOC Operations
Resource-constrained security teams don’t need convincing that proactive work matters. Most already have a long list of improvements they want to make: better detections, more and better log sources, prioritized vulnerabilities, least-privilege access … the list goes on. The problem is they rarely get to it. Day after day, time is swallowed by reactive work: alert triage, investigation, and ticketing. That tension between what matters and what gets done is consistent across teams.
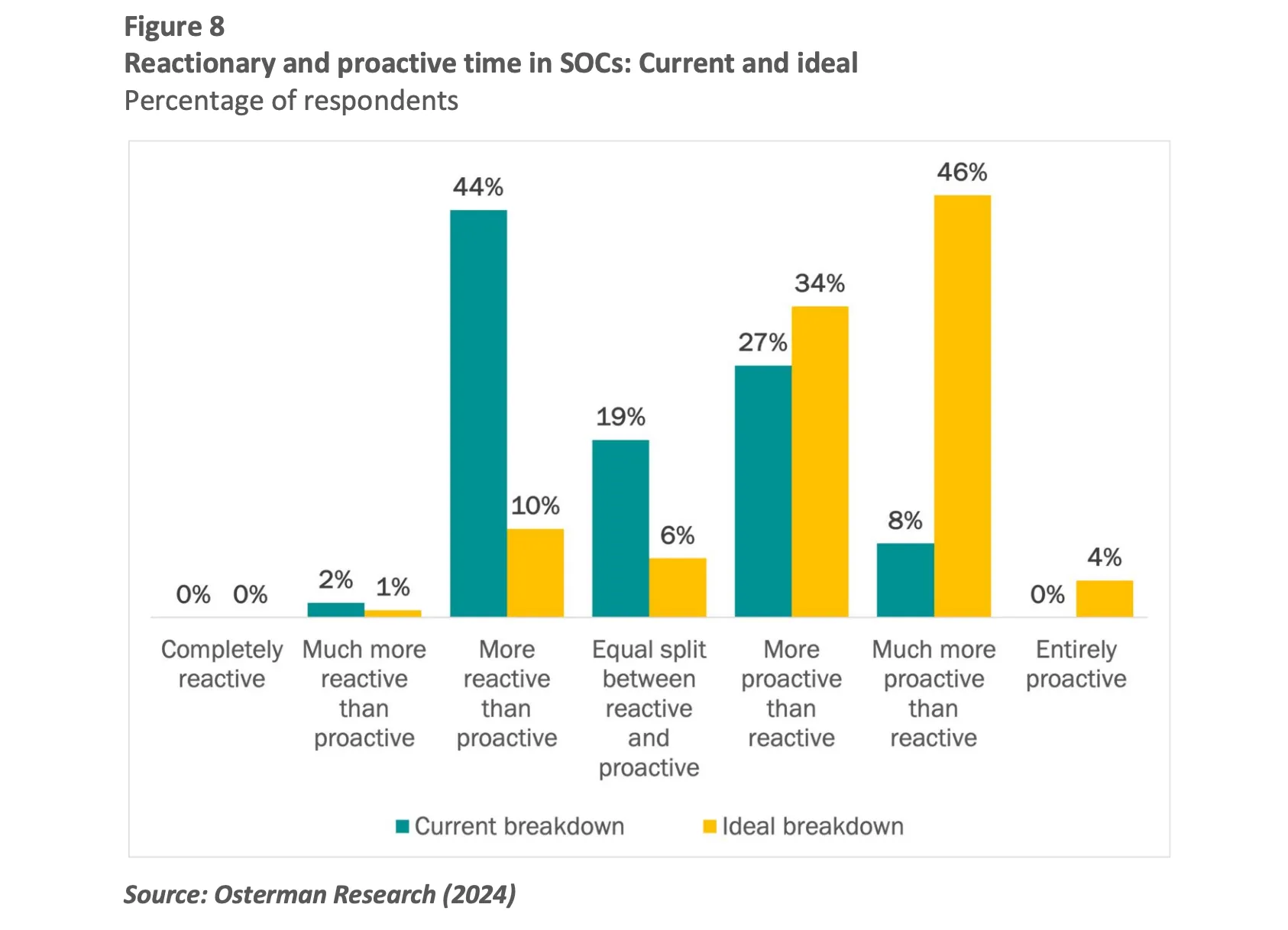
A 2024 Osterman Research survey revealed that the majority of security professionals want to prioritize proactive tasks, but only a small fraction of their time is dedicated to them. According to the survey report, “Many SOCs are stuck in a reactive firefighting mode of operation where half of available time is spent reacting to the latest crisis. In this research, 46% of organizations spend more time in reactionary mode than proactive mode, and an additional 19% say there is an equal split between the two modes. In combination, that’s more than two out of three SOCs.”
This gap is where AI SOC agents like Dropzone AI come in. They’re not just accelerators; they’re multipliers, freeing teams from reactive work so that they can focus on work that actually improves the security posture of the organization.
The Goal: High-Value Proactive Security Work
Proactive work is what pushes security forward. It’s the time spent building detections that map to real-world TTPs, not just dropping in vendor-provided rules, but writing your own based on observed behaviors in your environment.
Shrinking the Attack Surface
It’s reviewing the gaps exposed in recent incidents and updating your runbooks so that the next time, the path from detection to containment is shorter. It’s getting ahead of known vulnerabilities by correlating scan data with asset criticality and pushing fixes before they’re exploited. It’s cross-functional reviews with IT, engineering, and compliance to tighten controls and eliminate blind spots.
These types of activities directly reduce risk exposure. When detections are tuned and the right log sources are brought in, false positives drop, and actual threats are caught sooner. When patching isn’t just reactive, the attack surface gets progressively smaller. When the team revisits detection logic and response processes after every major incident response (IR), the process becomes faster because there is less guesswork and fewer escalations.
Less Noise, More Signal
You also start seeing better fidelity in the investigation process. Instead of jumping between SIEM dashboards, EDR consoles, and ticketing systems, context is already layered in. Analysts are moving decisions forward because telemetry and enrichment have been aligned to how they work cases. Audit outcomes improve, not because someone cleaned up the documentation at the last minute, but because workflows are already built with traceability in mind.
Teams want to get here; they know what good looks like. The barrier is time. Proactive work pays off fast, but only if there’s room to do it. Without it, teams are stuck replaying the same incidents, with the same inefficiencies, over and over.
The Time Trap: Why It Rarely Happens
.webp)
Every day in the SOC starts with a queue of alerts from the SIEM, tickets from the help desk, and a few flagged emails from executives—if you’re lucky. On especially bad days, there’s active exploitation of a widespread zero-day vulnerability or worse. Before you can even think about tuning a detection or reviewing yesterday’s gaps, you’re pulled into triage and incident response. Did that login anomaly warrant a deeper look? Is that EDR alert another noisy behavior-based flag? You dig, document, escalate, and close. Then repeat.
Most teams aren’t short on motivation; they’re short on bandwidth. The 2024 Osterman Research survey indicates that security teams would like to spend the majority of their time on proactive work, such as detection engineering; however, in practice, only about a quarter of their time is dedicated to this effort. The rest gets swallowed up by alert handling and incident response that rarely leads to deeper investigation or root cause analysis.
When You’re Too Busy to Save Time
The volume of inbound alerts doesn’t just demand attention, it dictates pace. It’s not enough to spot suspicious activity; you must quickly contextualize it, often stitching together logs from disparate sources, manually checking enrichment, and validating assumptions.
Even with a well-maintained SIEM and threat intelligence feed, you often end up second-guessing correlations or retracing steps when the tooling doesn’t provide clear answers.
The Anxiety of Cybersecurity Debt
This kind of operational grind adds up when you’re on call or rotating through primary responder duties; there’s a persistent sense that something important is slipping through the cracks.
You log off knowing you didn’t get to the detection logic that needs review. You didn’t map the internally gathered threat activity you’ve seen to MITRE ATT&CK. You didn’t update the IR documentation with the learnings from yesterday. And that weighs on you.
So you get stuck in the loop: responding instead of building. Improving the stack, testing hypotheses, or hardening coverage becomes a luxury. The backlog of projects aimed at reducing future toil continues to grow. The work that should make your team more resilient and less reactive often fails to receive the attention it deserves.
The Solution: AI SOC Agents as Force Multipliers
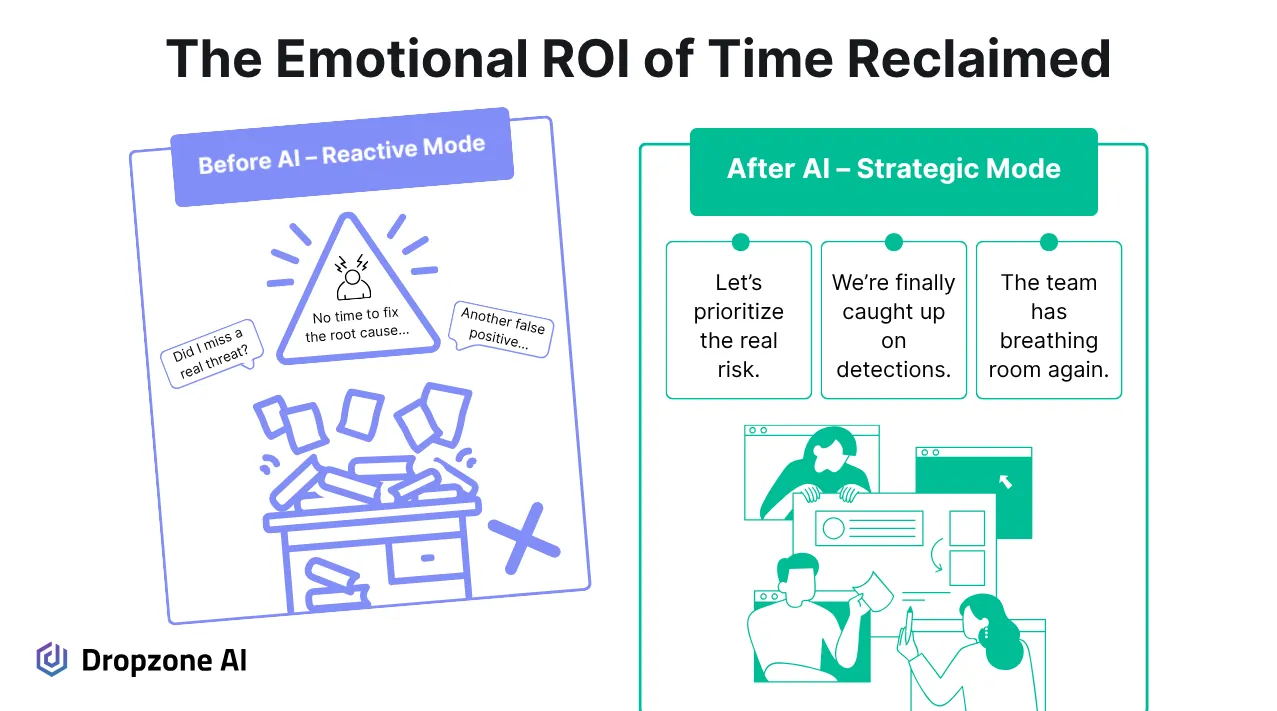
When you’re stuck in reactive mode, the first thing to go is focus. AI SOC agents, such as Dropzone, shift usual SOC dynamics by taking high-volume, low-value tasks off your plate. Triage becomes automated as alerts get sorted, scored, and de-duplicated before they even hit your queue. You’re no longer starting from scratch when triaging alerts. Instead, you have full investigation reports complete with conclusions, findings, and evidence.
One of the biggest time gains comes from how investigations are handled. Dropzone enriches alerts with relevant data sources in real-time, such as asset inventory, user activity, threat intelligence, and past incident context. You’re not stitching this together from five tools or waiting on other teams to pull logs. The timeline is already built. The pivots are already there. It’s a faster and cleaner process.
The result isn’t just time saved, it’s a better use of the time you have. Analysts can step back and examine coverage gaps, revisit detection logic, and explore emerging techniques.
Conclusion
You don’t improve security posture by doing more of the same. You improve it by carving out space to think, build, and fix the things that keep causing noise. That only happens when teams get time back, and AI can make that possible. Look at where your time goes. If most of it’s tied up in repetitive investigation, triage, or alert routing, that’s an opportunity.
AI SOC Agents like Dropzone can handle those layers, giving your team room to operate strategically. If you're evaluating options, it may help to model that shift. Our ROI calculator can help you visualize what reclaiming even 20% of your time looks like in terms of measurable outcomes. Check it out here and start quantifying the difference.