Introduction
Your SIEM generates alerts. Your EDR flags suspicious processes. Your network monitoring identifies anomalies. But what about the threats that slip through all three? The sophisticated attacks that look like normal admin activity, use legitimate credentials, and operate below your detection thresholds? That's where threat hunting comes in:the proactive search for hidden threats that your automated defenses missed.
What Is Threat Hunting in Cybersecurity?
Threat hunting is the proactive process of searching for cyber threats that have evaded your automated security defenses. While traditional security tools wait for known signatures or rule violations to trigger alerts, threat hunters actively search through networks, endpoints, and log data looking for unusual patterns.
Think of threat hunting like a security guard actively patrolling your building versus an alarm system that only sounds after a break-in. The alarm system is reactive (waits for a breach to trigger). The security guard is proactive (looking for threats before anything bad happens).
Threat hunters search for:
- Unusual credential access patterns
- Lateral movement between systems that shouldn't communicate
- Data transfers at odd hours
- PowerShell commands outside normal administrative activity
- Process executions that deviate from established baselines
- Subtle behavioral signals automated tools miss
Real-World Example
An attacker gains initial access through compromised credentials (which look legitimate to automated tools), then slowly moves laterally using standard administrative tools like Remote Desktop.
No malware signature to detect. No rule violation to trigger an alert.
But a threat hunter examining authentication logs and lateral movement patterns spots the anomaly: unusual account activity combined with cross-subnet RDP sessions. The intrusion is uncovered before the attacker reaches critical systems.
In 2026, this proactive approach is essential. Threats operate at machine speed. Advanced adversaries use identity-based attacks and living-off-the-land techniques specifically designed to evade automated detection.
Why Threat Hunting Matters (The Dwell Time Problem)
The Dwell Time Reality
Source: M-Trends 2025, Mandiant
Median dwell time (how long threats remain undetected) reached 11 days in 2024 (M-Trends 2025). But here's the reality: those are median numbers for detected breaches. For sophisticated threats that successfully evade detection, average dwell time still reaches 200+ days.
The Cost of Detection Delays
The global average cost of a data breach is $4.44 million (IBM Cost of Breach 2025). Much of that cost directly correlates with detection delays. The longer threats operate undetected, the more damage they inflict.
What modern threats look like:
- Custom malware that evades signatures
- Legitimate system tools used maliciously
- Patient reconnaissance staying below detection thresholds
- Identity-focused attacks that bypass EDR
- Techniques specifically crafted to avoid SIEM correlation
Why Proactive Hunting Works
Proactive threat hunting reduces dwell time by not waiting for threats to trigger known patterns. When your team actively searches for behavioral anomalies (unusual authentication, suspicious processes, abnormal data movements), they find threats operating in the gaps between automated rules.
Every day of reduced dwell time means:
- Less data exfiltration
- Less lateral movement
- Less damage
- Lower breach costs
Organizations discover 50% of breaches through their internal security teams (IBM 2025). Those internally-discovered breaches (often found through proactive hunting) typically cost less than breaches discovered by external entities or ransomware notifications.
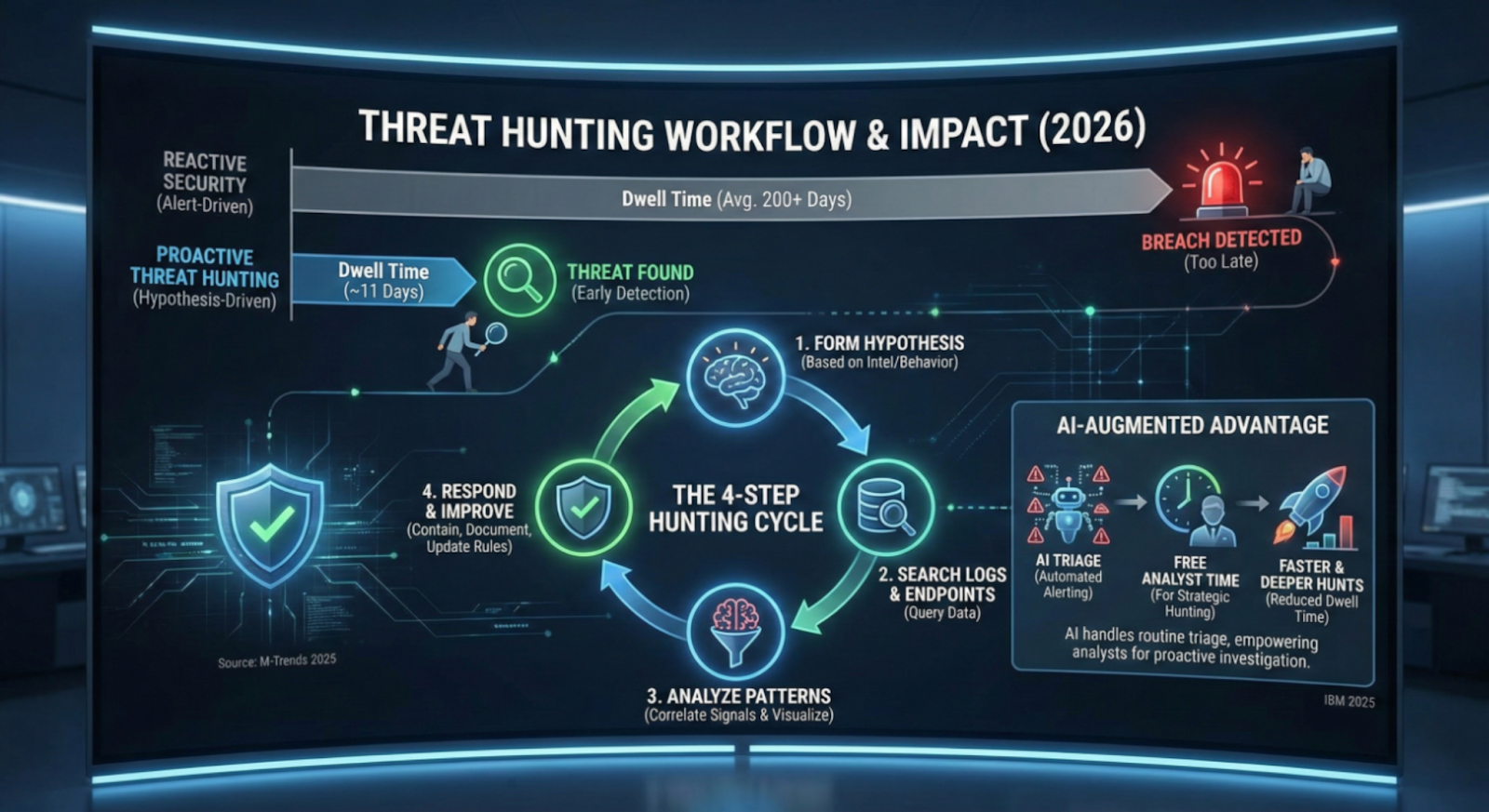
How Threat Hunting Works (4-Step Process)
Effective threat hunting follows a systematic cycle:
1. Form Hypothesis
Start with a testable theory based on threat intelligence, industry reports, or observed behavior.
Example: "Attackers targeting our industry are using credential dumping techniques. Are we seeing signs of this in our environment?"
2. Search Logs and Endpoints
Query security data sources:
- SIEM logs
- EDR telemetry
- Network traffic
- Authentication records
Look for evidence supporting or refuting your hypothesis.
3. Analyze Patterns
Correlate signals from multiple sources to distinguish threats from false positives:
- Does unusual PowerShell execution correlate with credential access?
- Does lateral movement follow suspicious authentication?
- Pattern analysis separates true threats from benign anomalies
4. Respond and Improve
When you confirm a threat:
- Escalate to incident response for containment
- Document findings for institutional knowledge
- Update detection rules to catch similar threats automatically
- Share intelligence with security team
This cycle is continuous. Each hunt generates intelligence for future hypotheses. Each discovered threat updates baseline understanding of normal vs. suspicious.
Threat Hunting vs Incident Response: Key Differences
How they work together: Threat hunting discovers threats that become incidents requiring IR. Incident response provides intelligence (attack techniques, IOCs, adversary behaviors) that inform future hunting hypotheses.
Mature security programs integrate both approaches. Hunting finds what detection misses. IR handles confirmed threats at scale.
Modern AI-augmented SOCs blur these lines productively. When AI handles routine alert triage autonomously, it frees analyst time for proactive hunting. The complementary approaches (automated alert investigation plus human-driven proactive hunting) create comprehensive security coverage that purely reactive or purely manual approaches cannot achieve.
The Role of AI in Modern Threat Hunting
The Capacity Problem
79% of SOCs operate 24/7 (SANS SOC Survey 2025)
Alert volumes overwhelm even the largest teams. Skill gaps persist. Time that should go toward proactive hunting gets consumed by reactive alert triage.
How AI Creates Hunting Capacity
AI augments threat hunting by automating routine investigative work:
What AI Handles:
- Tier-1 alert triage and correlation
- Log enrichment with threat intelligence
- Initial threat/non-threat determination
- Cross-domain signal correlation (endpoint, network, identity)
- Behavioral anomaly detection at scale
- Continuous monitoring during off-hours
What Analysts Gain:
- Time for hypothesis formation
- Capacity for complex investigations
- Focus on strategic hunting activities
- Consistent investigation quality regardless of workload
AI and automation shorten breach lifecycle by 80 days (IBM 2025). But here's what matters for hunting: when AI handles repetitive Tier-1 work, experienced analysts gain 6-8 hours daily for strategic hunting activities.
This enhances your analysts' capabilities rather than replacing their expertise. AI augments SOC capabilities by automating tasks that don't require human creativity (routine correlation, baseline comparison, IOC matching). Analysts maintain control over hypothesis formation, threat prioritization, and response decisions.
Getting Started with Threat Hunting
Step 1: Start with existing tools
You don't need specialized platforms. Your current SIEM, EDR, and network monitoring provide the data foundation. Learn their query capabilities and visibility.
Step 2: Begin with IOC-based hunting
IOC-based hunting using known threat intelligence (malicious IPs, file hashes, domains from threat feeds) provides an accessible starting point. You're looking for known bad, not forming complex hypotheses.
Step 3: Build documentation habits
Document every hunt:
- Your hypothesis
- Data sources queried
- Findings (even negative results)
- Lessons learned
These become institutional knowledge and training material.
Step 4: Consider AI platforms for scale
As your program matures, evaluate AI-augmented SOC platforms that automate routine investigation work. This creates capacity for consistent hunting when your team operates under constant alert pressure.
Progressive Maturity Path
Start: Alert-based hunting (reactive) → Move to: Scheduled IOC hunts → Advance to: Hypothesis-driven hunting
The journey takes time, but each hunt builds capability.
Key Takeaways
- Threat hunting is proactive search for threats that evaded automated defenses, addressing dwell time by not waiting for alerts
- Essential in 2026 as sophisticated adversaries use identity-based attacks and living-off-the-land techniques designed to bypass automated detection
- AI-augmented SOC platforms automate routine alert triage, freeing experienced analysts from repetitive Tier-1 work for strategic threat hunting
- Success metrics: reduced dwell time, threats discovered beyond automated detection, analyst time freed for proactive activities














