SIEMs excel at collecting data, correlating events, and raising alerts, but their capabilities end at detection. Once an alert fires, analysts must still dig through email logs, endpoint data, and identity systems to determine what really happened. Dropzone AI fills that gap by automatically pulling in the missing context, investigating across systems, and explaining what's actually going on, all without requiring scripts, playbooks, or full data ingestion. In this article, we'll look at how Dropzone transforms a traditional SIEM into a system that can think, reason, and respond on its own.
Why Can't SIEMs Investigate Alerts on Their Own?
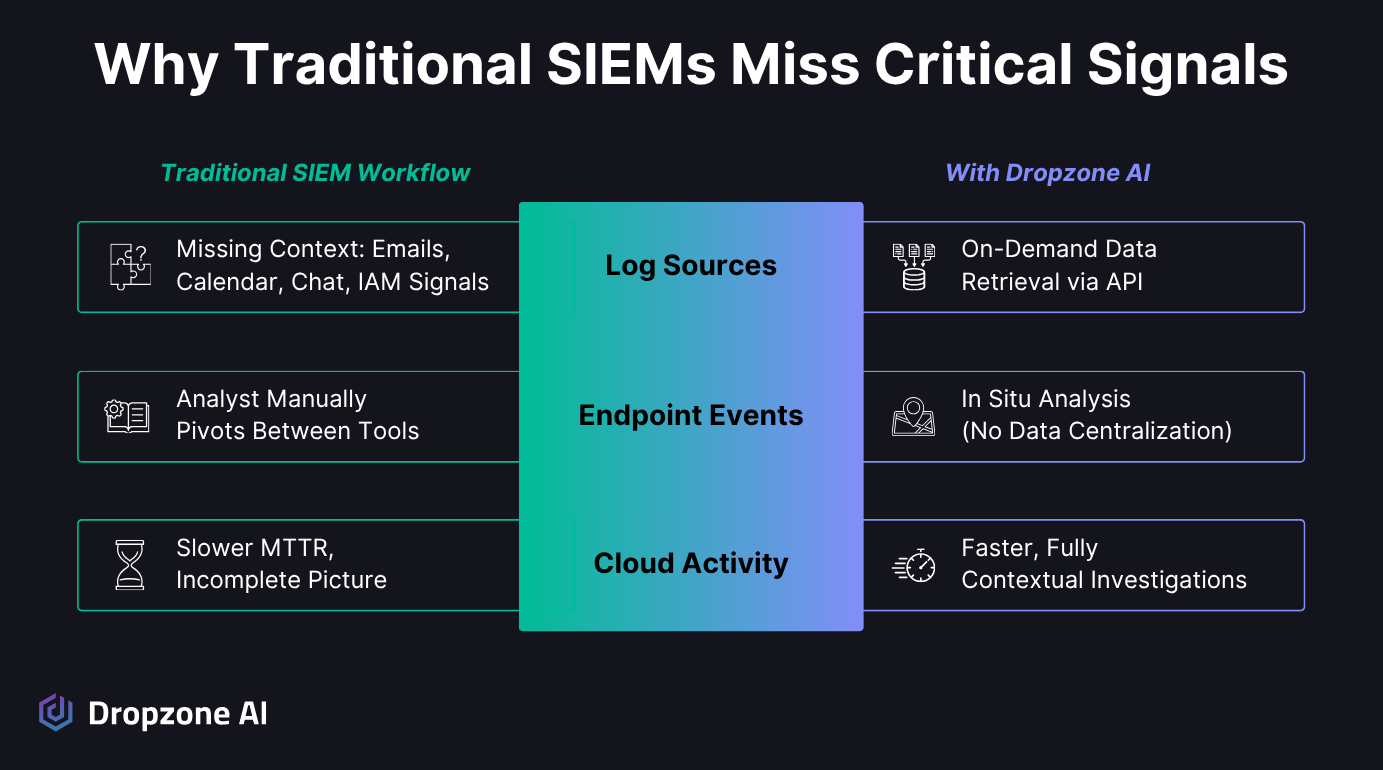
What Context Do SIEMs Typically Miss?
SIEMs excel at capturing system data, such as firewalls, endpoints, and authentication events, but often overlook significant human context. High-volume sources, such as SaaS logs, often remain outside the SIEM due to their high cost and complexity in ingestion. In addition, there’s some data crucial to investigations that the SIEM doesn’t have access to, such as email and calendar events. That means analysts see the alert but not the situation around it. They know something happened, but need to understand why.
Context sources typically outside SIEM:
- Email contents and communications patterns
- Contents of shared files
- Collaboration tool usage
- Calendar schedules
- SaaS application activity
- Cloud service logs
When that happens, analysts do a lot of investigative legwork, using multiple tools to piece things together. They jump between consoles, export logs, and manually cross-check timestamps. It's slow, repetitive work that eats into response time and increases the chance of missing key details. Most of the time, the data they need is already available; it's just locked in systems that the SIEM doesn't access.
How Dropzone AI Brings the Missing Context Back
Dropzone AI fills in those gaps without changing how the SIEM works by connecting through secure, read-only APIs and pulling missing context, like meeting activity or recent login details, or reading through email contents and shared files. Dropzone can also use tools for things like PDF analysis and sandbox execution.
You don’t need to send more data to the SIEM for analysis; Dropzone goes out and finds the needed context itself. Every Dropzone request to a data source is logged under strict access controls. Under the hood, Dropzone uses pre-trained AI agents that each specialize in a specific type of tool or skill.
The video below explains how Dropzone reasons through an investigation:
When an SIEM alert appears, Dropzone determines what's missing, queries the appropriate sources, and reasons through the evidence to reach a verdict—an alert is either a true or false positive, malicious or benign. Analysts get a full picture of what happened in minutes, eliminating the need for manual digging.
What's the Difference Between SOAR Automation and AI Investigation?
How SOAR Works with AI SOC Analysts
Many security leaders and architects have questions about where SOAR fits with AI SOC analysts. In fact, the two technologies are complementary.
SOAR platforms excel at handling repetitive tasks, enriching alerts, isolating hosts, or closing tickets, but their capabilities are limited to what's already been scripted. Every action follows a predefined rule or decision tree.
SOAR capabilities:
- Executes predefined workflows
- Automates repetitive tasks
- Requires playbook maintenance
AI investigation capabilities:
- Reasons through ambiguous evidence
- Adapts to unknown threats
- Explains findings with context
When a new or ambiguous SIEM alert appears, SOAR can't adapt; it either stalls or routes it back to a human analyst. That means complex, unfamiliar attacks often slip through the automation layer and land in the manual queue.
Analysts often spend time on investigation steps that could be automated if the system were capable of reasoning. They still need to identify intent, compare behavior across systems, and create timelines to explain what actually happened. SOAR handles execution, not interpretation. It doesn't learn from previous investigations or adjust based on uncertainty. That's where AI-driven analysis changes what's possible in a SOC.
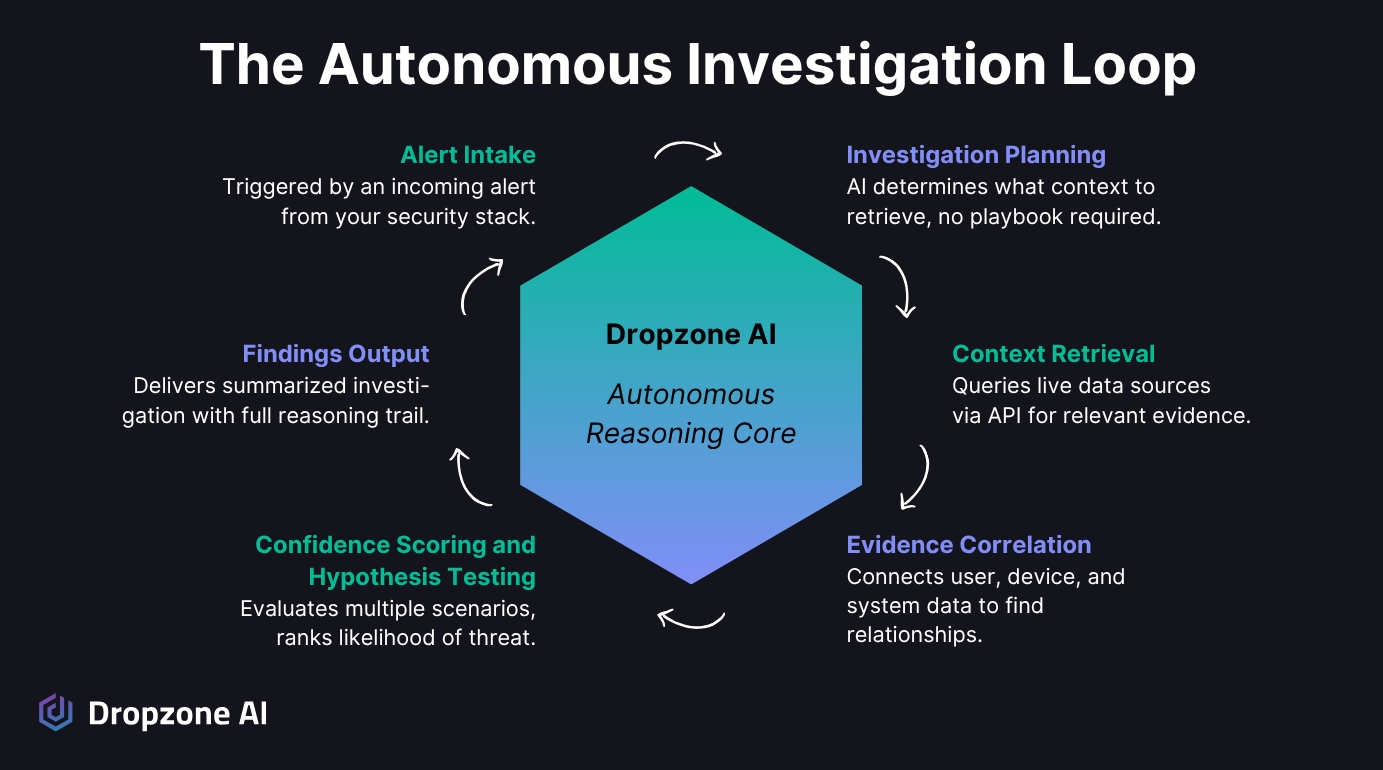
How Dropzone Thinks Like an Expert Analyst
Dropzone AI is an agentic system that uses large language models and context memory to go beyond rule-based automation. Instead of following a static playbook, it learns how to reason through evidence.
When a SIEM alert arrives in the queue, Dropzone automatically gathers data from endpoints, IAM logs, mailboxes, shared files, historical login activity, calendar events, VPN activity—the list of investigative context it gathers goes on. Dropzone can even interview users when needed. It compares these signals, looks for patterns of intent, and builds a contextual timeline of the event, all within minutes.
The system forms hypotheses about why an alert might be malicious or benign, weighs them against the context gathered, and then presents a conclusion with supporting evidence. That report includes the logic behind its conclusion, why it decided something was benign, suspicious, or worth escalation.
From there, Dropzone can send its findings directly into a SOAR for response automation or ticketing system for review. Analysts don't just get an alert; they get a full, reasoned investigation ready to dismiss or escalate.
How Does Dropzone AI Work With Your Existing Security Stack?
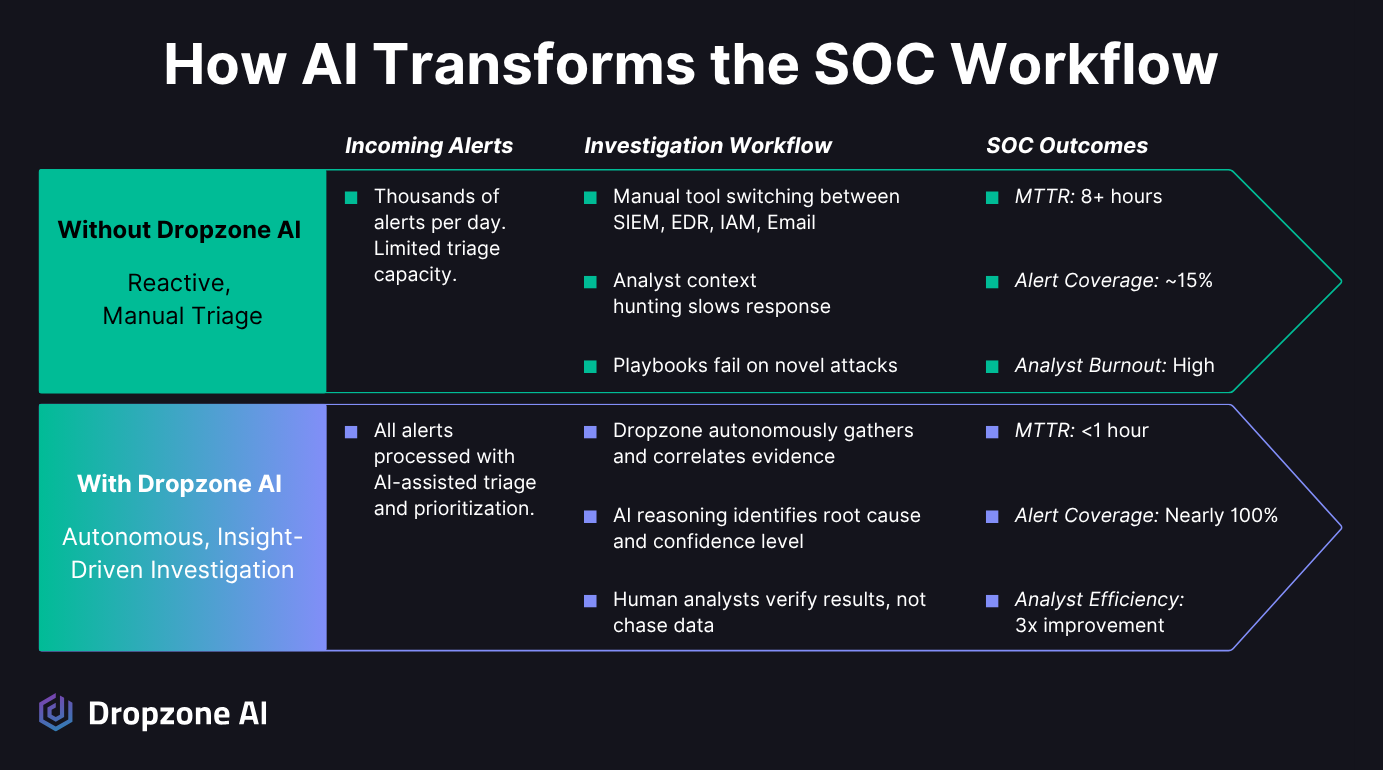
From Alert Overload to Interesting Security Work
Working in a SOC, you know how reactive things can feel. The SIEM lights up with alerts and analysts scramble to piece together what's real and what's noise.
Each investigation means jumping between console endpoint logs, email evidence, and identity records, hoping the full story eventually comes together. It's exhausting, and honestly, it's not the best use of human time.
Dropzone changes that dynamic; when an alert hits, it immediately starts collecting context from across your connected systems. It checks user sessions, endpoint activity, and communication patterns, then stitches it all together into a clear, readable summary.
What used to take hours of manual digging now happens automatically. Analysts can focus on confirming and making decisions, rather than chasing data.
Fits Right Into the Tools You Already Use
Dropzone doesn't replace your stack; it works alongside it; it connects through simple REST APIs or webhooks, allowing alerts from your SIEM to flow directly into Dropzone's investigation engine. Dropzone also queries your SIEM like an expert user to gather data needed for an investigation.
Integration approach:
- Connects via REST APIs, webhooks, or MCP
- Read-only access with audit logging
- No data storage or ingestion required
- Works alongside existing tools
There's no big deployment project or architecture change required. Everything runs as a separate service that uses the same security boundaries you already have in place.
Every query Dropzone makes is permission-bound, logged, and traceable. It operates with role-based access and strict rate limits, so nothing slips outside of policy.
All the heavy lifting happens in memory, with no extra storage or ingestion required. You get richer insights without adding new infrastructure or data pipelines. It just helps your existing tools work smarter together.
Results Your Team Can Actually Feel
The difference is easy to notice. Instead of triaging a small subset of cut-and-dry alerts, Dropzone helps your team cover much more, including endpoint, cloud, identity, network, and insider threat alerts. It handles the repetitive, low-level work, then delivers organized, evidence-based findings for analysts to review. Investigations move faster, fatigue decreases, and confidence in decisions increases.
You'll see it in the numbers: shorter mean time to resolution, fewer missed alerts, and cleaner escalations. But you'll also feel it in the workflow. Your analysts regain their time, your SOC becomes calmer, and the team can finally focus on strategic security thinking instead of just keeping up with alerts.
What Systems Does Dropzone AI Connect To?
Data sources accessed during investigation:
- Email systems (Microsoft 365, Google Workspace)
- Identity providers (Okta, Active Directory)
- Endpoint platforms (CrowdStrike, SentinelOne)
- Cloud infrastructure (AWS, Azure, GCP)
- VPN and network access logs
- SaaS applications and collaboration tools
Security approach: All connections use read-only API access with full audit logging and role-based permissions.
Key Takeaways
- SIEMs Don't See the Full Picture. Traditional SIEMs collect valuable logs but miss critical human-layer context, such as email, calendar, and SaaS activity, creating investigation blind spots that slow down response.
- Dropzone AI Investigates, Not Just Automates. Unlike SOAR tools that follow rigid playbooks, Dropzone uses AI reasoning to gather context, form hypotheses, and explain findings, turning alerts into clear, evidence-backed insights.
- Smarter Workflows, Not More Tools. Dropzone runs alongside your existing SIEM, automating triage and investigation without changing your infrastructure. Analysts gain speed, coverage, and clarity without extra complexity.
Conclusion
SIEMs are incredible at detection, but detection is only half of the equation. Without automated investigation that can pull context from across your entire environment and reason to a conclusion, alerts pile up, analysts burn out, and threats slip through.
Dropzone AI changes that. It turns your SIEM into a thinking system—one that doesn't just flag suspicious activity, but autonomously investigates it with the skill and reasoning of a senior analyst. Your team gets complete, evidence-backed answers instead of ambiguous alerts, freeing them to focus on high-impact work that requires human judgment.
See Dropzone AI in Action
Ready to see how AI investigation transforms your SIEM workflow? Our self-guided demo lets you experience Dropzone AI autonomously investigating real security alerts in a live environment.
What you'll see in the demo:
- Complete alert investigations in 3-10 minutes
- Automatic context gathering from email, identity, and cloud systems
- AI reasoning that explains findings with supporting evidence
- Integration with your existing SIEM and security stack
No sales call required. Explore the platform at your own pace and see exactly how Dropzone AI turns your SIEM alerts into actionable insights.















