Introduction
Teams across financial services are under constant pressure to protect customers, stop fraud quickly, and meet strict regulatory expectations, all while handling nonstop identity alerts, cloud activity, and customer transactions. Most SOCs are skilled but overloaded, making it harder to maintain consistent, well-documented investigations.
Dropzone helps by taking on investigations the way a human analyst would, applying whole reasoning and context at a pace teams can't match on their own. This article examines why financial institutions are turning to AI-driven investigation automation and how it's helping them keep up with growing demands.
Why Are Financial Institutions Under Increasing Security Pressure?
Financial institutions face escalating pressure from two fronts: regulatory frameworks demanding faster, more defensible investigations, and increasingly complex threats that span multiple security tools and require deeper contextual analysis. This dual pressure creates operational strain on fatigued SOC analysts who must maintain audit-ready documentation while responding to sophisticated attacks across identity systems, cloud environments, endpoints, and payment networks.
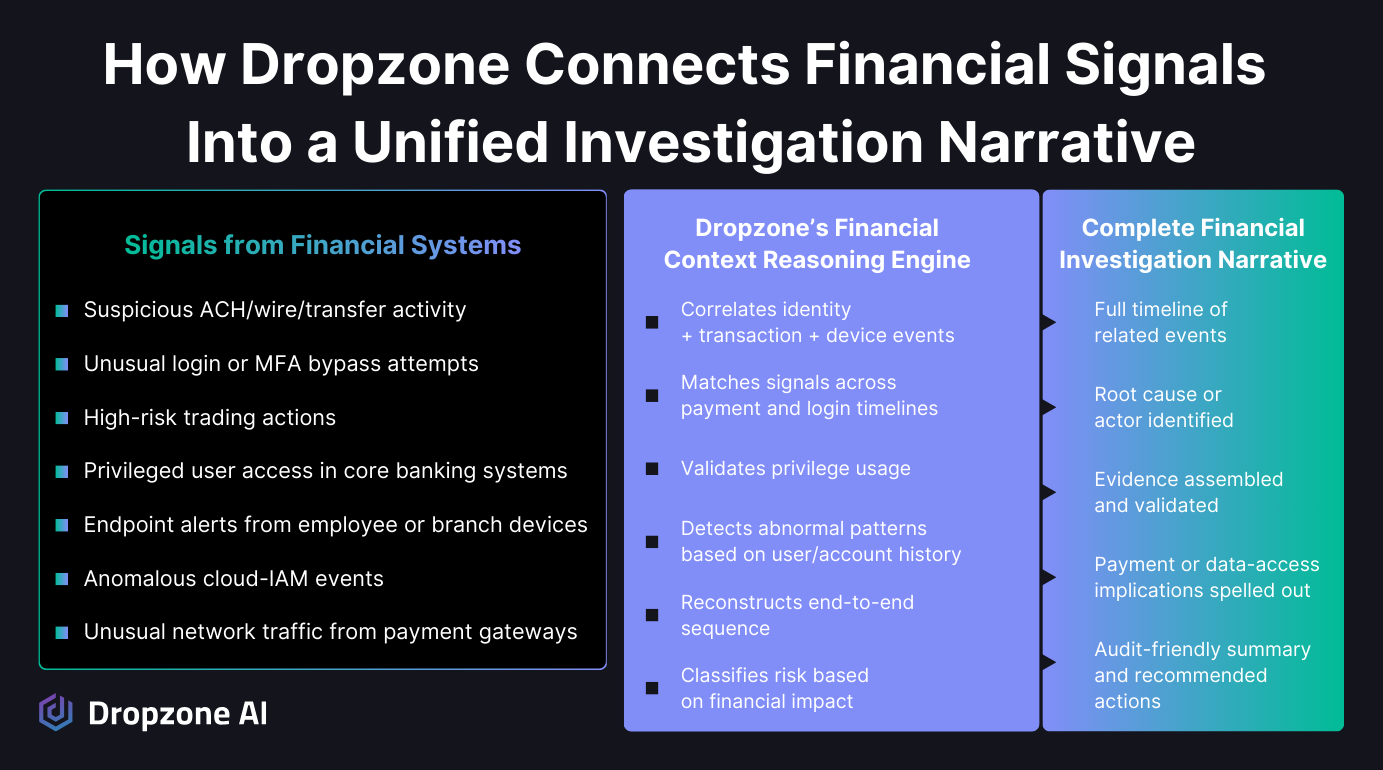
Regulators Expect Faster, More Defensible Investigations
Security teams in financial services face intense regulatory scrutiny. The challenge is not only responding to alerts, but proving to regulators that every investigation followed a consistent, documented, and defensible process.
Compliance Framework Requirements
How Dropzone Supports Compliance: Investigations function as complete case files with every step, piece of evidence, and decision recorded in a clear timeline. SOC teams no longer need to reconstruct investigations for audits. They can rely on ready-to-use, defensible reports that align with examiner expectations.
Threats Are More Complex and Require Deeper Context
Threats to financial institutions rarely reside in a single system. Analysts often have to jump between multiple data sources to understand what is really happening:
Data Sources Analysts Must Correlate
- Identity tools and authentication logs
- Cloud activity and configuration events
- Endpoint (EDR) behavior and process execution
- Network traffic patterns and lateral movement indicators
- Payment system transaction logs
Each source operates independently, requiring manual correlation to understand the full attack chain. That back-and-forth slows investigations, especially during high-volume periods.
Internal access risks make this even more complicated, since a single compromised employee account can quickly impact regulated systems and customer data. In those cases, teams must clearly show what happened, why it mattered, and what evidence supports the conclusion.
Dropzone AI's Solution: Automatically brings this context together by stitching identity events, endpoint activity, cloud behavior, and network patterns into a single investigation. Instead of piecing together fragments from multiple tools, analysts get a clear reasoning trail that helps them confirm or dismiss threats more quickly and work with confidence, even under pressure.
Why Are Skilled SOC Analysts at Risk of Attrition?
Despite having talented security professionals, SOC teams can't scale fast enough to handle exponential alert growth across identity, payment, cloud, and endpoint systems. Hiring and training is slow and expensive, industry turnover remains high, and even when roles are filled, the workload quickly overwhelms the expanded team. This creates an endless cycle where manual investigation becomes the bottleneck, not analyst skill or dedication.
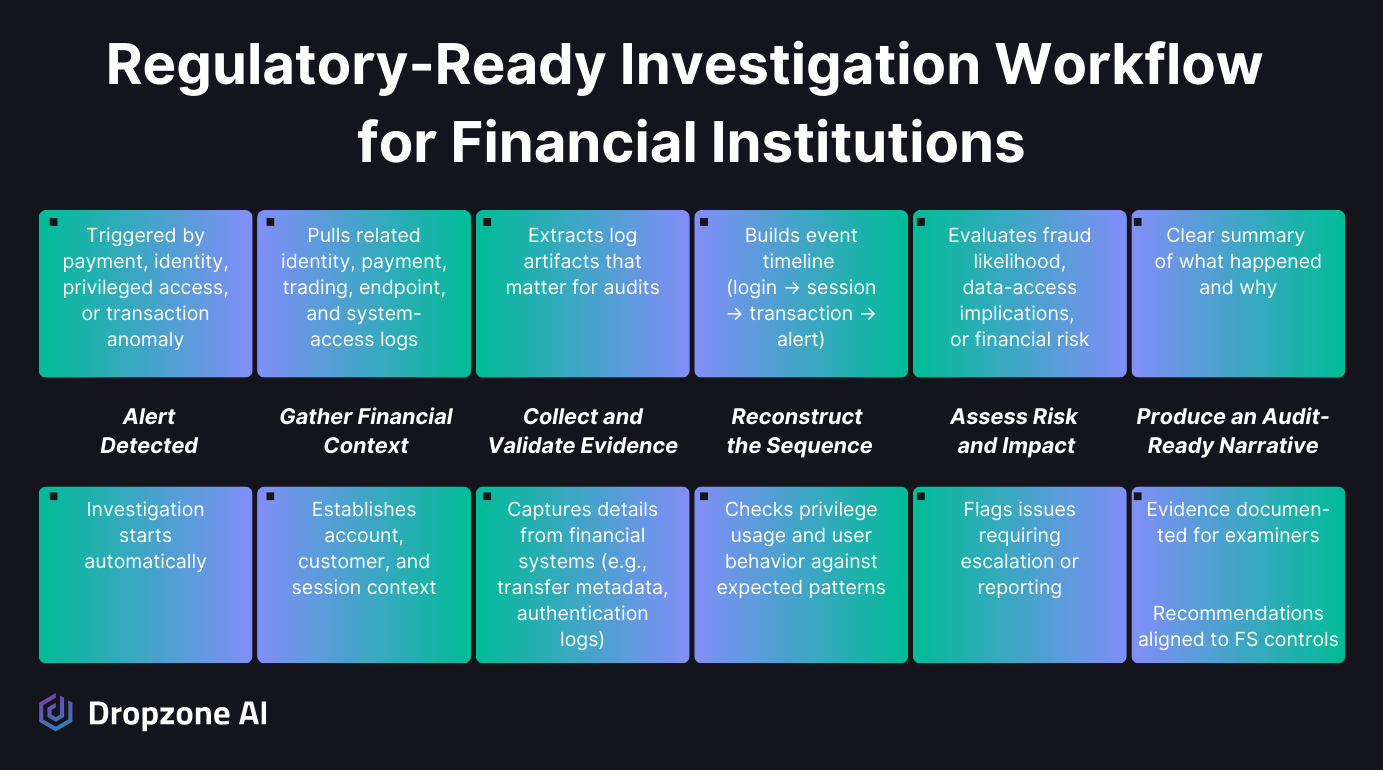
Alert Volume Keeps Growing, but Staffing Can't
Financial services SOC teams are full of talented people, but the workload keeps growing faster than anyone can realistically handle. Analysts face constant alerts across:
- Identity anomalies - Unusual login patterns, privilege escalations, access violations
- Payment system alerts - Transaction monitoring, fraud detection signals
- Cloud configuration drift - Policy violations, unauthorized changes, compliance gaps
- EDR noise - Endpoint behavior alerts requiring investigation and context
Each alert requires real attention: checking identities, reviewing endpoint activity, confirming cloud events, and tracing network behavior. It's a lot to work through, and the number of systems involved means even simple investigations take longer than they should.
As volume rises, many analysts feel like they're stuck in an endless triage loop. They're spending so much time validating alerts that there's barely any space left for deeper investigative work or the improvements they know the environment needs. High-volume days turn into high-volume weeks, and the pressure quietly builds.
Even in the relatively well-resourced financial services sector, attrition in the SOC is a serious problem because of fatigue and strain. Hiring is slow and expensive, and 62% of SOC professionals say their organization isn't doing enough to retain top talent (SANS 2025). Teams often lose analysts within a few years, which means they're constantly training new people while trying to keep up with a nonstop queue of alerts. It puts everyone in a tough spot. The SOC wants to maintain high standards, but the workload keeps pushing them right up against the edge.
Automation That Enhances SOC Output and Reduces Fatigue
Many financial institutions are looking for a way to support their teams without trying to hire their way out of the problem. Senior analysts are hard to find, and even when roles are filled, the workload soon overwhelms the team again. Automation that can carry out full investigations (not just summarize data) gives analysts the breathing room they've been missing. AI SOC agents allow human analysts to focus on real security investigations instead of weeding out false positives.
Dropzone’s AI SOC analyst takes over the investigative work that analysts usually have to do by hand. It collects context, connects evidence across systems, validates what's happening, and writes out a detailed narrative that shows how it reached every conclusion. Analysts get a complete investigation to review, not a pile of logs. That shift lets them focus on work that actually moves security forward, such as fraud-detection improvements, threat hunting, or tuning the signals that matter for their business.
Most financial institutions run a mix of security tools that don't communicate:
Each product has its own AI features, but none of them talk to each other. Analysts still have to jump between them to understand what's going on.
Dropzone AI's Vendor-Agnostic Advantage: Connects across all security tools and produces a single, clear investigation, giving teams the consistency they've been trying to build on their own.
How Do Financial Services Maintain 24/7 Security Coverage?
Financial services maintain continuous security coverage through AI-driven investigations that run around the clock with the same depth and quality as human analysts. Dropzone automatically verifies user context, closes false-positive alerts pre-escalation, and produces audit-ready documentation. This reduces overnight analyst escalations while maintaining SLA consistency across all time zones.
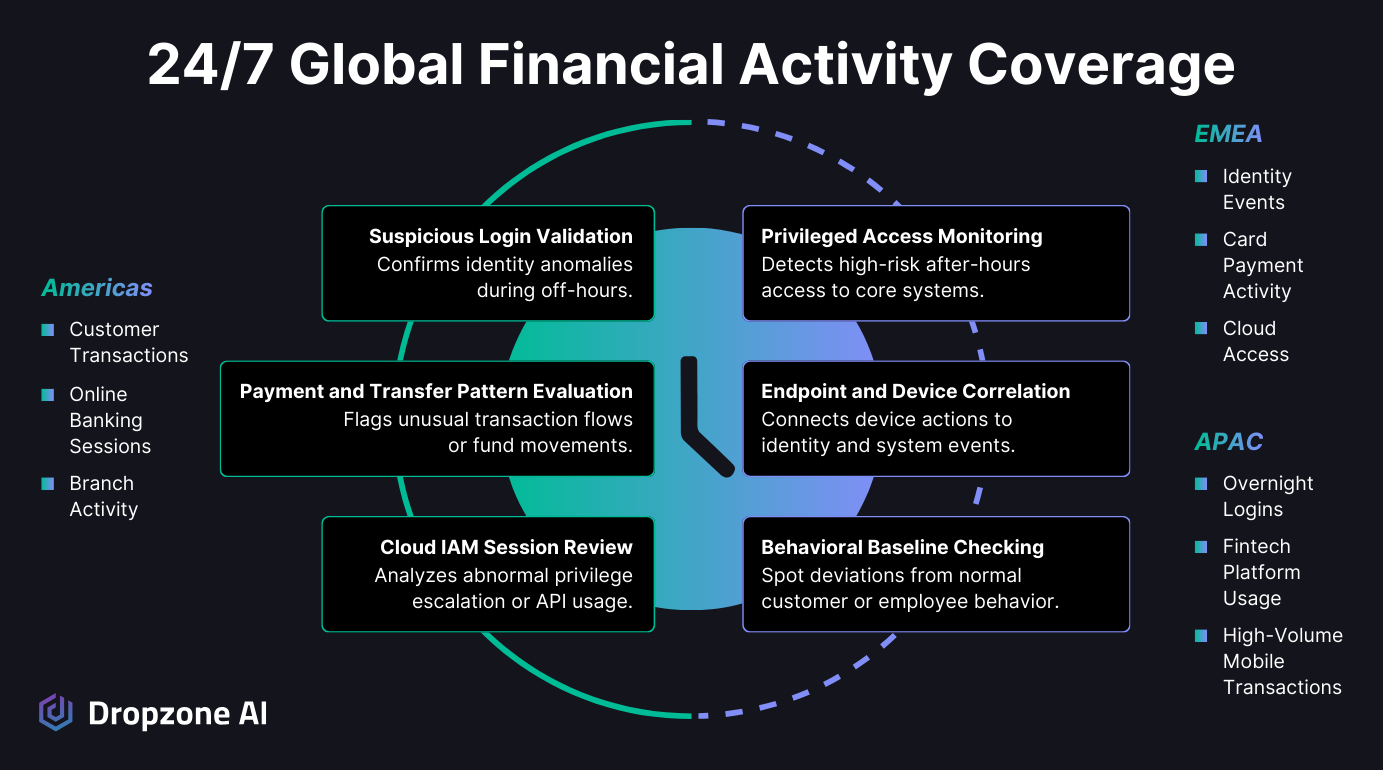
Investigations That Don't Pause When the Business Doesn't
People in financial services know better than anyone that the work never really stops. Customers move money, log in, make changes, and trigger identity checks at any time of day. This reality drives 79% of SOCs to operate 24/7 (SANS 2025). When an unusual login, a strange cloud session, or an unexpected authentication event happens at midnight, the SOC can't just wait until morning. Someone has to look at it, and teams feel that pressure constantly.
The off-hours alert problem creates multiple cascading issues:
- Sleep disruption - Interrupts analyst recovery time
- Next-day productivity loss - Context-switching exhaustion compounds
- Always-on pressure - Creates unsustainable on-call burden
- False alarm fatigue - Many overnight escalations turn out to be legitimate activity
When most alerts turn out to be false, the real cost goes beyond lost sleep: it erodes team resilience.
Dropzone AI's 24/7 Solution: Runs full investigations around the clock with the same careful reasoning and context checking you expect during business hours, but without calling on an analyst to get out of bed or log in after hours. It brings steadiness to the parts of SOC work that used to rely on someone sacrificing their night just to confirm whether something mattered.
Reducing Escalations While Strengthening Operational Resilience
Overnight escalations aren't just disruptive; they add real strain to already busy teams. Many SOCs report that most of the alerts that wake analysts up turn out to be legitimate employee activity, such as employees working late or traveling.
Dropzone automatically verifies user context and closes false alerts before they reach the SOC:
Benefits:
- Closes false-positive alerts pre-escalation
- Improves analyst recovery time and focus
- Maintains SLA consistency across all time zones
- Reduces operational strain on senior team members
- Produces defensible documentation for overnight events
Teams get stronger operational resilience without adding headcount to night shifts. Instead of coming in tired or facing a backlog of half-finished overnight investigations, analysts start their morning with clean, well-documented cases ready for review. Response quality stays consistent whether it's 2 p.m. or 2 a.m., and leadership gets more confidence that nothing slipped through the cracks overnight.
For financial institutions that operate across multiple time zones or have strict internal SLAs, consistency matters. Dropzone gives teams the ability to maintain the same level of investigative depth no matter when the alert fires, helping them stay aligned with resilience targets without stretching people thin or expanding on-call rotations.
Key Takeaways
- Financial services SOC teams are overloaded, and manual investigations can't keep pace with the rising volume of identity alerts, cloud events, and regulatory expectations.
- AI-driven investigations give analysts time back by handling the full reasoning and context gathering needed to validate alerts across complex environments.
Financial services organizations gain faster response times and true 24/7 coverage without adding headcount, while keeping documentation consistent for audits and regulators.
Conclusion
Financial institutions face constant pressure to move quickly, stay secure, and meet strict regulatory expectations, and that weight shows up most clearly in the SOC. Dropzone helps teams handle that load by delivering investigations that feel like a seasoned analyst wrote them, but with the consistency and speed needed to keep pace with modern threats. Faster MTTR, smoother day-to-day operations, and true 24/7 coverage give FS teams a way to stay ahead of fraud, risk, and compliance demands without stretching staff beyond their limits. If you want to see how this works in practice, you can walk through it yourself in our self-guided demo.