Introduction
SOAR has been widely adopted to automate security workflows, streamline response actions, and improve operational efficiency. However, Gartner and other industry leaders have pointed out that SOAR alone struggles with complex investigations that require contextual analysis and decision-making. While SOAR is effective at enrichment and predefined actions, it cannot adapt to evolving threats in real-time. AI SOC analysts bridge this gap by performing deep investigations, reasoning through complex attack patterns, and reducing the manual burden on security teams. This article will break down the roles of SOAR and AI SOC analysts, explain how they complement each other, and outline a workflow that leverages both for a smarter, faster security operation.
The Reality of SOAR: What It Does Well and Where It Falls Short
SOAR’s Strengths
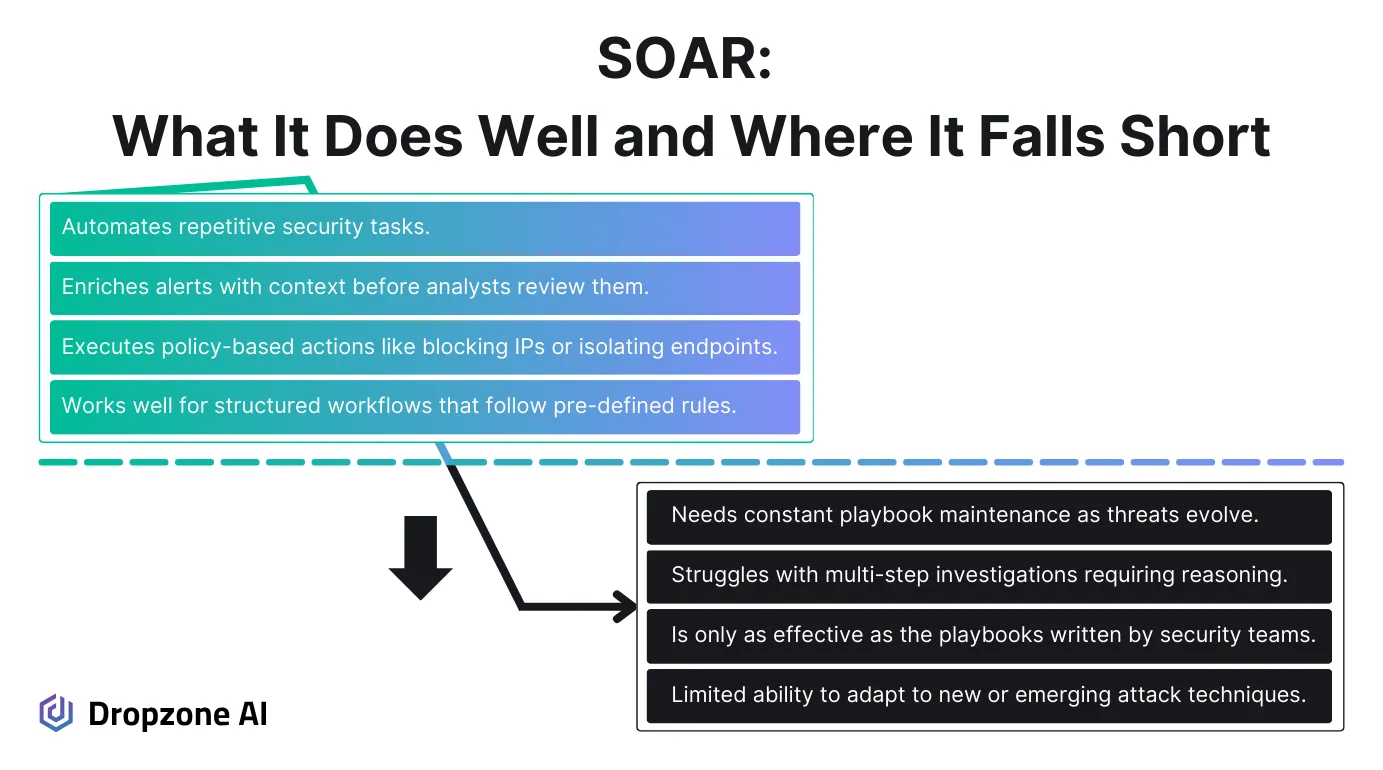
SOAR helps security teams automate repetitive tasks, making workflows more efficient by integrating security tools and executing predefined actions. It speeds up alert triage by automatically enriching security events with context, such as checking an IP address against threat intelligence feeds or correlating an alert with previous incidents. This reduces manual workload and allows analysts to focus on actual threats rather than spending time collecting data across different platforms.
SOAR also speeds up standard security responses by executing policy-based actions like isolating an endpoint, disabling a compromised account, or blocking a malicious domain. These predefined workflows improve response consistency but are only as effective as the rules written into them.
SOAR’s Challenges
SOAR playbooks require ongoing maintenance to stay relevant. Threat actors continuously evolve their techniques, and when a playbook doesn’t account for a new attack pattern, it either fails to trigger the right response or generates unnecessary escalations.
Security teams often struggle to keep up with these changes, leading to outdated automation workflows that increase the risk of missing threats or creating alert fatigue. Another challenge is that SOAR follows static instructions and doesn’t adapt dynamically when an investigation requires deeper analysis.
For example, suppose a security event involves a series of unusual authentication attempts across multiple regions. In that case, SOAR may flag it but won’t be able to determine whether the behavior is a real attack or just an employee traveling for work. That decision still falls on a human analyst, adding friction to the investigative process.
Gartner’s Take on SOAR
Gartner has noted a shift in how security teams are using SOAR. Instead of relying on standalone SOAR platforms, many organizations now prefer security tools like SIEM and XDR with built-in automation capabilities. This shift reflects a growing demand for more flexible and adaptive automation rather than solely relying on rigid playbooks.
AI-driven security automation is emerging as an alternative to handle deeper investigations without requiring manual intervention at every step. Unlike SOAR, AI SOC analysts can adjust their investigative paths based on real-time data, identify new attack patterns without needing pre-written rules, and make contextual decisions that static playbooks cannot. This allows security teams to automate more of their response processes without worrying about the constant maintenance overhead that traditional SOAR systems require.
AI SOC Analysts: The Missing Piece in Security Automation
What AI SOC Analysts Do That SOAR Cannot
SOAR automates predefined tasks, but AI SOC analysts handle investigations dynamically, adapting to security events in real-time. They provide deeper analysis and decision-making without relying on static workflows.
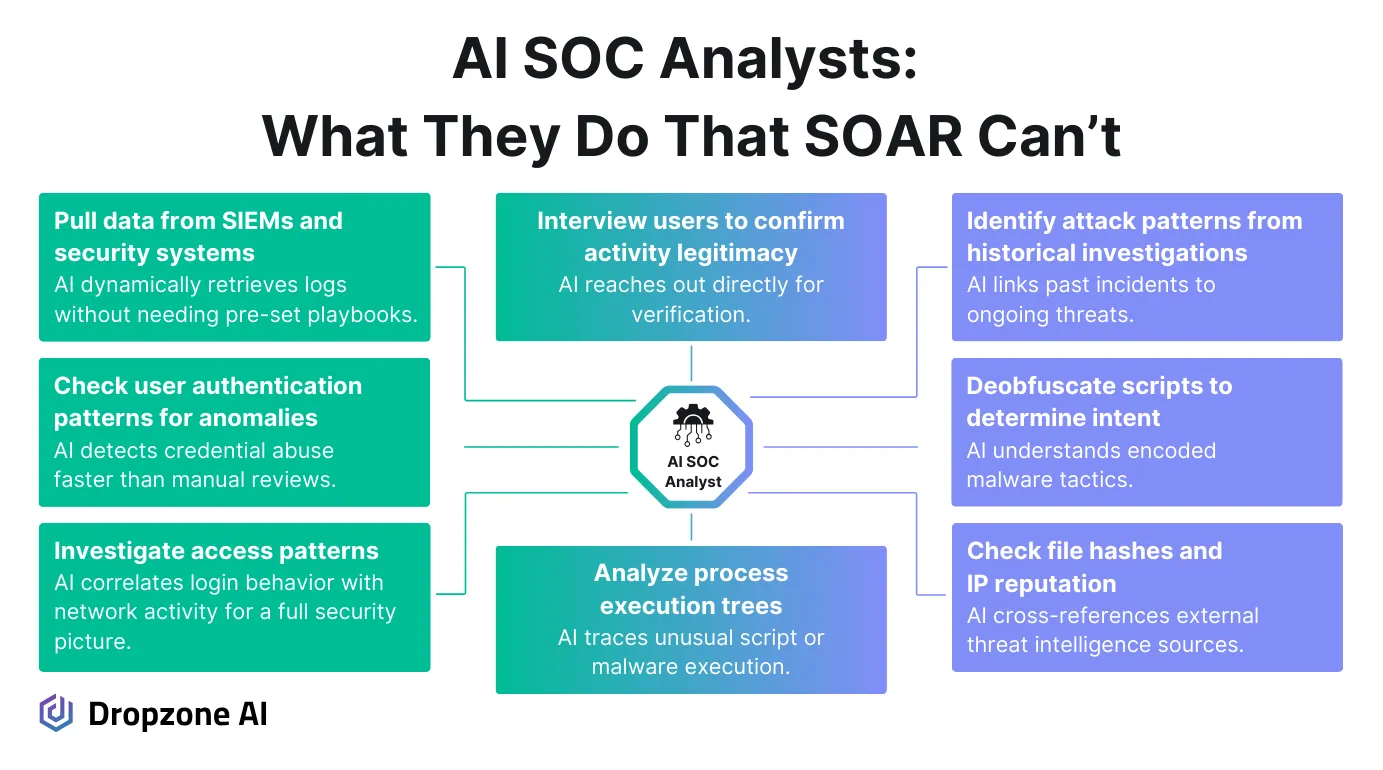
- Retrieve, correlate, and analyze security data from SIEMs, EDRs, identity platforms, and business systems to detect anomalies in authentication, access behaviors, and privilege escalation attempts.
- Investigate and verify suspicious activity by mapping user and process behaviors, engaging users for validation, and identifying deviations from normal patterns across cloud and on-prem environments.
- Trace and analyze execution flows by reviewing command-line activity, parent-child process relationships, and historical attack patterns to uncover tactics used in broader campaigns.
- Assess and decode potential threats by analyzing obfuscated scripts, payloads, and malware execution techniques to determine intent and detect attempts to evade security controls.
- Validate external risks and file integrity by checking IP addresses, domains, and file hashes against threat intelligence databases to identify malicious infrastructure and unauthorized file modifications.
How AI SOC Analysts Work Alongside SOAR
SOAR excels at handling structured workflows, such as enriching alerts with threat intelligence, automatically assigning tickets, or triggering predefined response actions like blocking an IP. These functions streamline security operations by reducing manual steps in well-documented scenarios. However, SOAR does not analyze the relationships between alerts or adjusts its workflow based on new findings. It operates within the boundaries of its preconfigured playbooks, escalating cases requiring more reasoning and investigation.
AI SOC analysts take over when an alert needs deeper investigation. Instead of escalating every ambiguous case to a human analyst, they correlate activity across multiple tools, gather additional data, and analyze patterns to determine if a threat is real.
They adapt their investigation path dynamically based on their findings, allowing them to confidently confirm or rule out threats. They escalate only fully contextualized incidents when necessary, providing security teams with a clear summary of findings and recommended actions. This combination of SOAR for structured automation and AI SOC analysts for reasoning-driven investigation creates an efficient and adaptive workflow.
Designing a Smarter Security Workflow: AI SOC Analysts + SOAR

Suggested Workflow: Where SOAR and AI SOC Analysts Fit Together
SOAR plays an important role in security automation, but it has limitations when dealing with complex investigations. AI SOC analysts work alongside SOAR by handling the investigative steps that require reasoning, correlation, and contextual understanding. Together, they create a more efficient and adaptable workflow.
- Step 1: SOAR enriches alerts by checking IP addresses, domains, and file hashes against threat intelligence databases. If no SOAR is present, the AI SOC analyst can complete this enrichment step.
- Step 2: AI SOC analyst investigates patterns and anomalies by analyzing authentication logs, access behaviors, and process execution details. The AI will recursively reason until it has all the findings and evidence that it needs.
- Step 3: AI SOC analyst generates a high-confidence decision, determining whether an alert is a real threat or a false positive before escalating to a human analyst.
- Step 4: AI SOC analysts can integrate with SOAR where present and initiate response actions. SOAR executes final response actions, such as isolating compromised systems, blocking malicious connections, or sending detailed reports to incident response teams.
Why This Approach Works
Security teams deal with high alert volumes, and many of those alerts are false positives or low-priority events that still require manual review. AI SOC analysts take on the initial investigative workload, allowing human analysts to focus on real threats instead of sorting through irrelevant alerts. This reduces burnout and increases productivity by automating tasks that don’t require human judgment.
Threat actors are adapting their techniques, making investigations more complex. AI SOC analysts use historical data, behavioral analytics, and real-time threat intelligence to connect the dots between multiple alerts. By applying reasoning, AI detects patterns that traditional automation would miss, increasing accuracy and reducing response times—and more importantly, the workload on human teams.
Still Using SOAR? AI SOC Analysts Still Provide Value
SOAR remains useful for automating response actions, but maintaining playbooks for every alert type is time-consuming. AI SOC analysts reduce the need for constant updates by dynamically adjusting to new threats and handling investigations that don’t fit into static workflows. Organizations that have invested in SOAR can improve its effectiveness by adding AI-driven investigations, making their security operations faster and more scalable.
Conclusion
SOAR remains an important part of security automation, but it reaches its limits when dealing with complex, multi-step investigations. AI SOC analysts fill this gap by applying reasoning, analyzing real-time security data, and reducing reliance on static playbooks. By combining SOAR’s response automation with AI-driven investigations, organizations gain a more adaptive, efficient, and scalable security operation. Teams looking to improve their detection and response capabilities should consider how AI SOC analysts can work within their existing workflows to automate investigations, reduce false positives, and accelerate threat resolution. See how Dropzone AI SOC analysts can enhance your security operations. Book a demo today.