Introduction
Running security operations today, you’re probably juggling too many tools, such as SIEM, EDR, cloud, identity—you name it. Each one serves a purpose, but they don’t always work together, creating real friction. That won’t necessarily get better even as each platform adds its own AI automation. While those AI agents will automate things within those platforms, that’s not how your human staff accomplishes tasks.
Almost always, your staff need to work across platforms and tools—so to get the full benefit of AI in the SOC, you’ll need the AI agents to do so as well. In this article, you’ll see why adding a vendor-agnostic AI layer can make a difference. You’ll learn how it brings your tools together, helps your analysts move faster, and unlocks more value from the stack you’ve already built.
Why Most Cybersecurity Stacks Are Siloed by Design
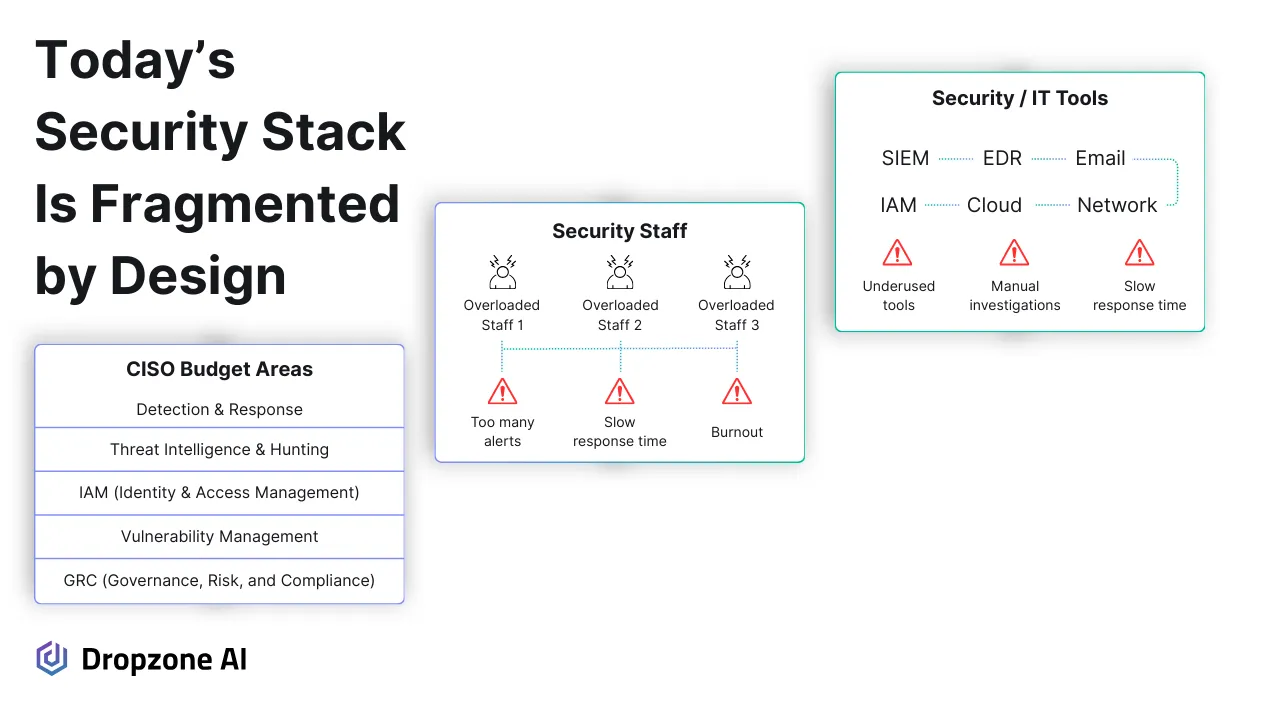
Enterprise security operations teams have fragmented stacks because budgets are divided by function. One team owns governance, another handles threat detection, and others manage identity, cloud, or vulnerability programs. The result is a collection of tools selected for specific domains or parts of the attack surface, but not necessarily designed to work together. Each system excels in its category but operates on its terms, with its data formats, alert logic, and context.
Even with integrations in place, these tools don’t analyze threats collaboratively. SOC analysts are left bridging the gaps themselves, jumping between consoles to piece together timelines and validate what happened.
That work adds up fast, especially when investigating complex incidents that span endpoints, cloud infrastructure, and identity systems. Valuable time is spent stitching together information that should already be connected.
The Case for an AI-Driven Security Reasoning Layer in Security Operations
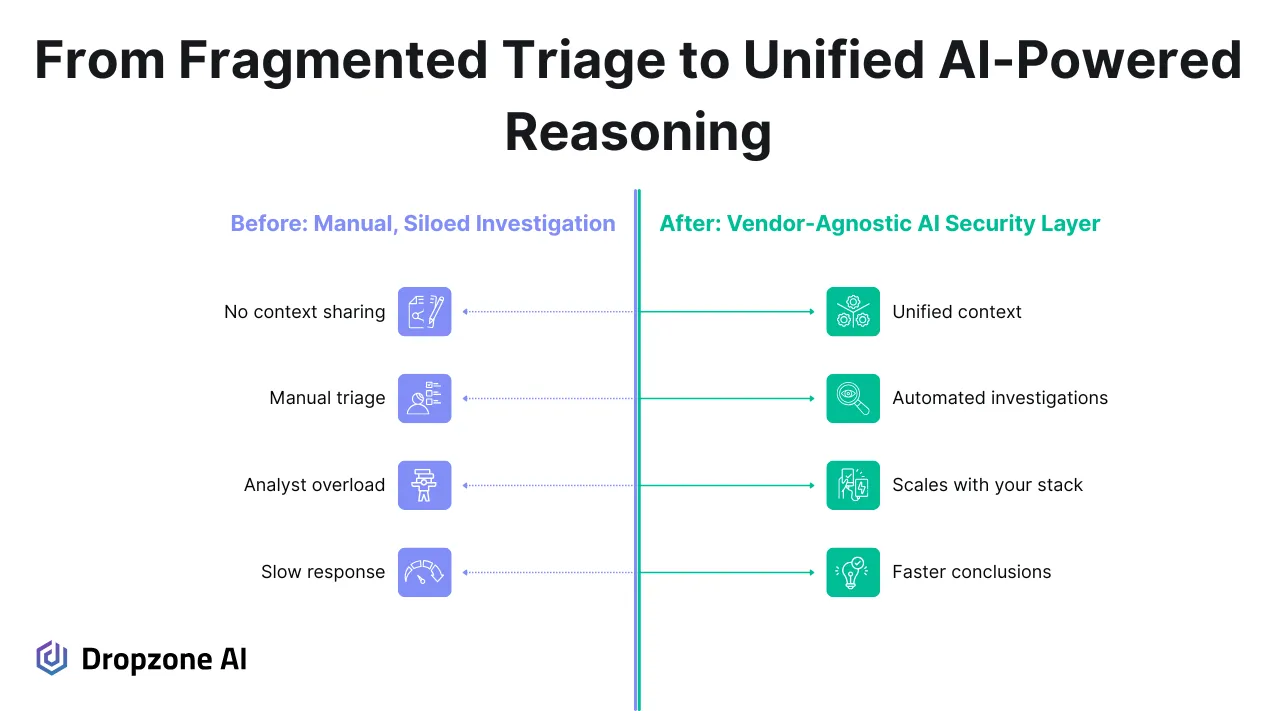
Security operations teams are used to working with data scattered across multiple tools. Each one is good at what it does, but they all operate in their lanes. What’s missing is something that can bring context together and understand the relationships between data points to help analysts see the full picture. This is especially true for alert investigations when security staff need to get context from different sources.
That’s where a vendor-agnostic AI layer impacts you, as it can pull from your SIEM, EDR, identity systems, cloud tools, and threat intel sources and use that combined context to investigate an alert the way that a human would (which is to say, the right way).
The AI system doesn’t just follow a checklist or run through pre-set rules. It recursively reasons through each alert like a seasoned analyst would, looping back to reevaluate based on new signals, comparing behaviors, checking historical data, and weighing evidence across different layers of the environment. This recursive analysis helps the system achieve more accurate outcomes, especially when filtering noise or prioritizing what matters most in real time.
It also gives SOC teams a way to unify all the areas the organization is already spending money on, such as threat detection, identity and access management, and vulnerability management, without stretching their analysts even thinner. Instead of juggling multiple platforms and trying to make sense of disconnected alerts, teams can rely on the AI layer to do the correlation work up front. It doesn't take away control; it gives analysts a smarter starting point, with more clarity and less guesswork.
Why Vendor-Agnostic Is Key
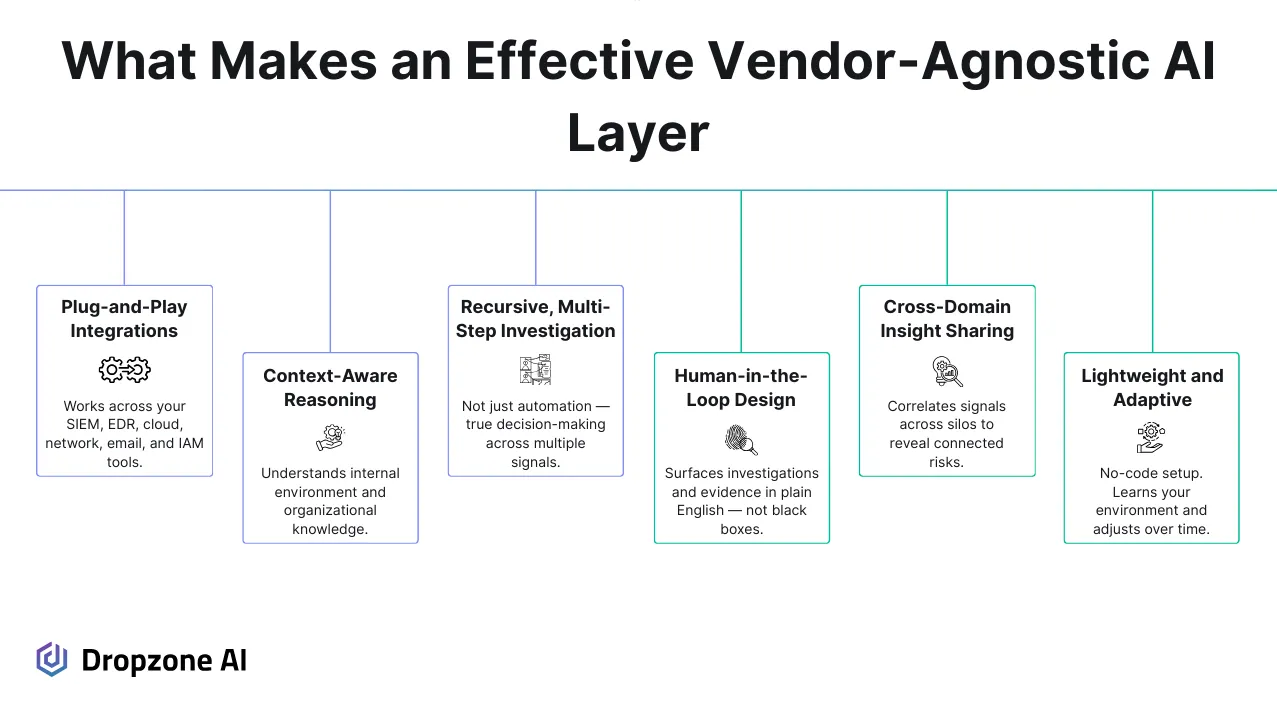
AI tools that only operate within a single vendor’s ecosystem will have a narrow field of view. They’re limited to the data and context available within that specific platform, so if an alert ties into something happening in another tool, that connection will go unnoticed unless a human is there to tie to contextual details together.
Most environments have multiple security tools and do not rely on a single vendor for everything. You likely have a SIEM from one vendor, EDR from another, identity tooling from a third, and a mix of cloud providers. If your AI can’t access and reason across all of that telemetry, it will miss things or, at best, require a human to stitch together the contextual information.
A vendor-agnostic AI layer can use the tools across your stack the same way that a human would and apply reasoning that spans use cases, such as phishing, lateral movement, privilege abuse, and data exfiltration. It doesn’t matter where the telemetry comes from: SSO logs, DNS records, EDR alerts, email metadata.
When the AI has access to everything, it can use the tools at hand the same way a human would to build a clearer picture of what’s happening. It’s not just aggregating data, it’s reasoning over it with awareness of sequence, user roles, and system behaviors. That depth is hard to achieve when AI is boxed into a single tool.
Importantly, being vendor-agnostic will enable AI automation to fulfill its promise in the SOC—eliminating toil. If vendor-specific AI implementations only have access to a narrow set of data, then it will be up to human SOC analysts to cross-check the results with other tools. That just sounds like more of the same problem that AI was supposed to solve.
Designed to Work With All Your Tools, Regardless of the Vendor
Dropzone AI was designed to operate independently of your vendor stack. It connects directly to your SIEM, EDR, cloud, identity, and ticketing systems via APIs and immediately pulls context without custom scripts or middleware. It applies recursive reasoning across those inputs to produce clean, scoped investigations.
Importantly, Dropzone AI also stores details it learns during investigations in context memory, which allows it to store environmental details and get better with time. This capability is making Dropzone AI an indispensable addition to the SOCs at organizations like Pipe, UiPath, and Zapier. “The more we use Dropzone AI, the smarter it gets. Each piece of context we add makes its investigations more accurate as it learns our environment,” says Alana Kim, Sr. Security Incident Response Engineer at Zapier.
You don’t need to rip anything out or migrate platforms. Dropzone sits on top, gives you full-stack visibility, and enhances the tools you’ve already invested in. This keeps your architecture flexible and helps your team stay fast without being locked into a closed ecosystem.
Key Takeaways
- Most security stacks are fragmented, leading to manual investigation work and context gaps across tools.
- AI features built into individual tools can’t reason across systems, leaving analysts to connect the dots themselves.
- A vendor-agnostic AI layer unifies context across your SIEM, EDR, IAM, cloud, and more—without requiring tool replacement.
- Dropzone AI integrates seamlessly with your existing stack, applying intelligence across platforms to scale security operations without additional headcount.
Conclusion
Adding more tools won’t fix coordination gaps. Security teams need a way to reason across their existing stack, connecting context, reducing noise, and speeding up investigations without adding stress. A vendor-agnostic AI layer like Dropzone AI does exactly that. It integrates with your current tools, applies deep reasoning, and delivers structured investigations your analysts can act on. This is how you scale security without slowing down. Ready to unify your stack and move faster? Book a demo today.