To better understand the evolving challenges and efficiencies within Security Operations Centers (SOCs), Dropzone AI partnered with Osterman Research. This collaboration gathered detailed insights from those at the forefront of cybersecurity defense—125 SOC professionals across various industries.
The survey captured a wide array of perspectives. Osterman Research surveyed professionals directly responsible for SOC operations, encompassing a range of roles from analysts to chief information security officers (CISOs). Participants were drawn from a representative sample of organizations varying in size from small enterprises to large multinational corporations across different sectors, including finance, healthcare, technology, and government. This breadth ensured that the findings would provide a holistic view of the current state of SOC operations worldwide.
The survey’s primary objective was to identify and analyze trends affecting SOC efficiency and the day-to-day experiences of SOC analysts, from understanding the dynamics of alert management to exploring the impacts of new technologies. It also gauged the professional satisfaction and challenges related to burnout.
First Off, the Good News: SOC Efficiency Is on the Rise
Cybersecurity is so frequently filled with negative news that it’s refreshing to report a positive trend: SOC efficiency is markedly improving. Our latest findings, illustrated in Figure 1, demonstrate that teams are faster to start work on new alerts and come to conclusions, actions respectively tracked with the metrics Mean Time to Acknowledge (MTTA) and Mean Time to Conclusion (MTTC).
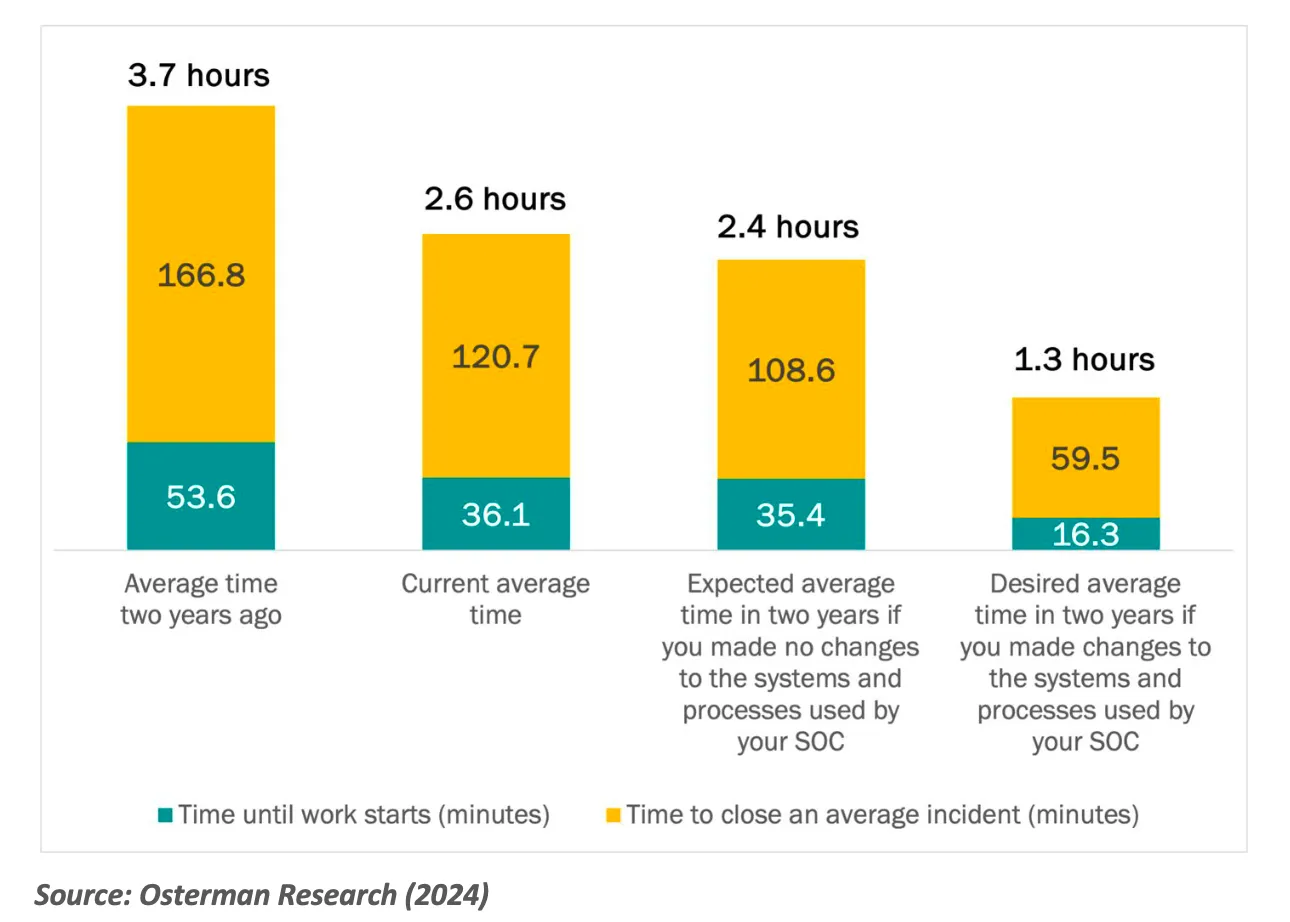
MTTA measures the time elapsed from detecting suspicious activity to when an analyst begins the triage process. A swift MTTA indicates a highly responsive and alert SOC team and enhances the overall security posture by accelerating the initial assessment phase of possible security threats.
MTTC, on the other hand, is a comprehensive metric developed by Dropzone AI that encompasses the entire time taken to analyze and designate an alert as benign or malicious. This metric offers a holistic view of the SOC’s efficiency, providing insights into how quickly a SOC can process incoming alerts.
Dropzone introduced MTTC as a crucial performance metric for SOCs. Faster resolution times mean reduced windows of opportunity for attackers, minimizing potential damage and enhancing organizational resilience.
Yikes, Bad News: Alert Volumes Outpacing Gains
While there are promising developments in SOC efficiency, not all news is good. According to our latest findings shown in Figure 2, the volume of security alerts continues to climb yearly. This rise can be attributed to many factors, including new attack surfaces and an uptick in attack activity. With such a growth in alerts, SOCs face a troubling trajectory: Alert volumes are likely to outpace the efficiency gains they have made.
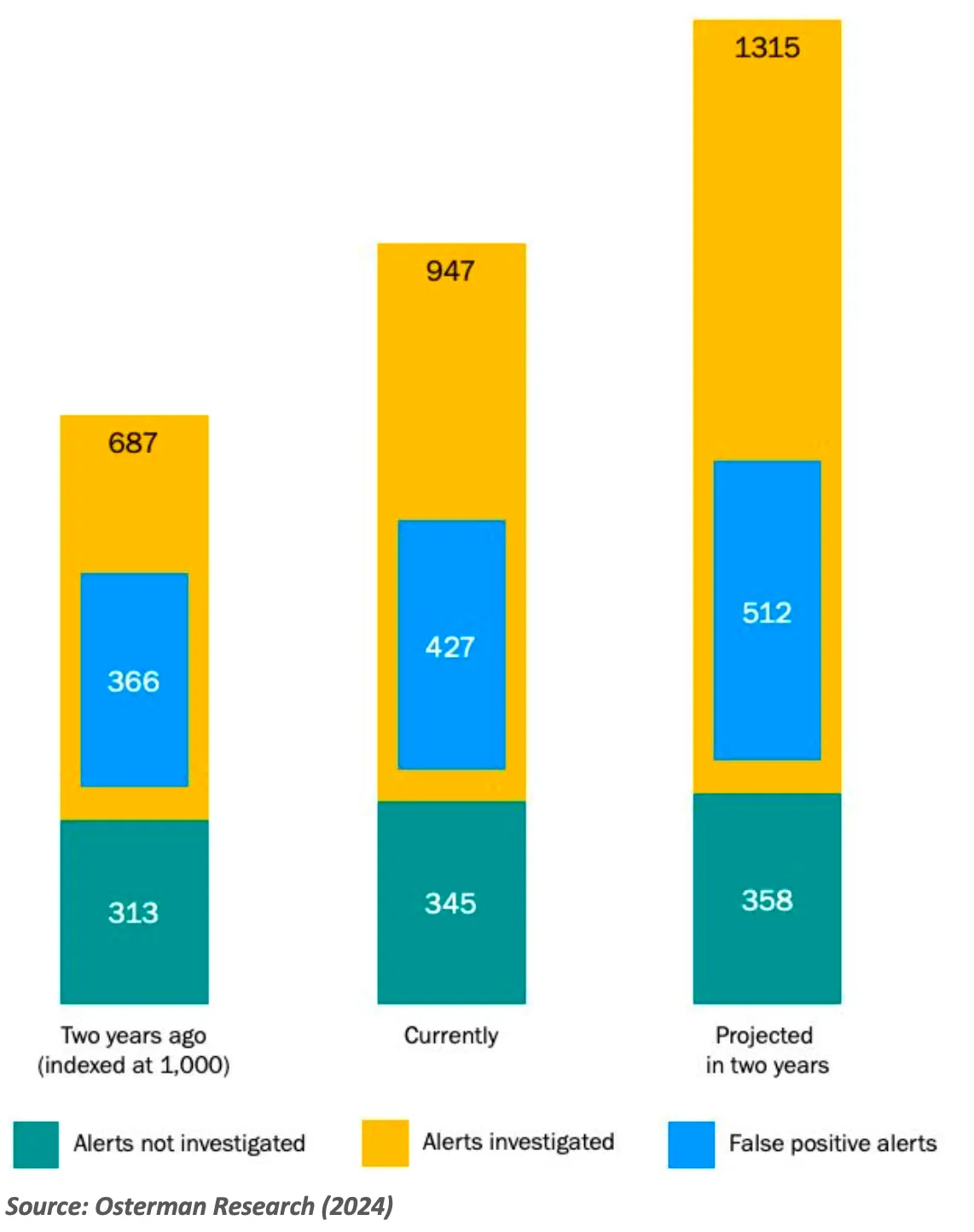
Despite improvements in detection accuracy, the sheer volume of alerts translates into an inevitable increase in false positives—alerts that, after investigation, do not represent actual threats. This not only strains resources but also risks diverting attention from genuine threats.
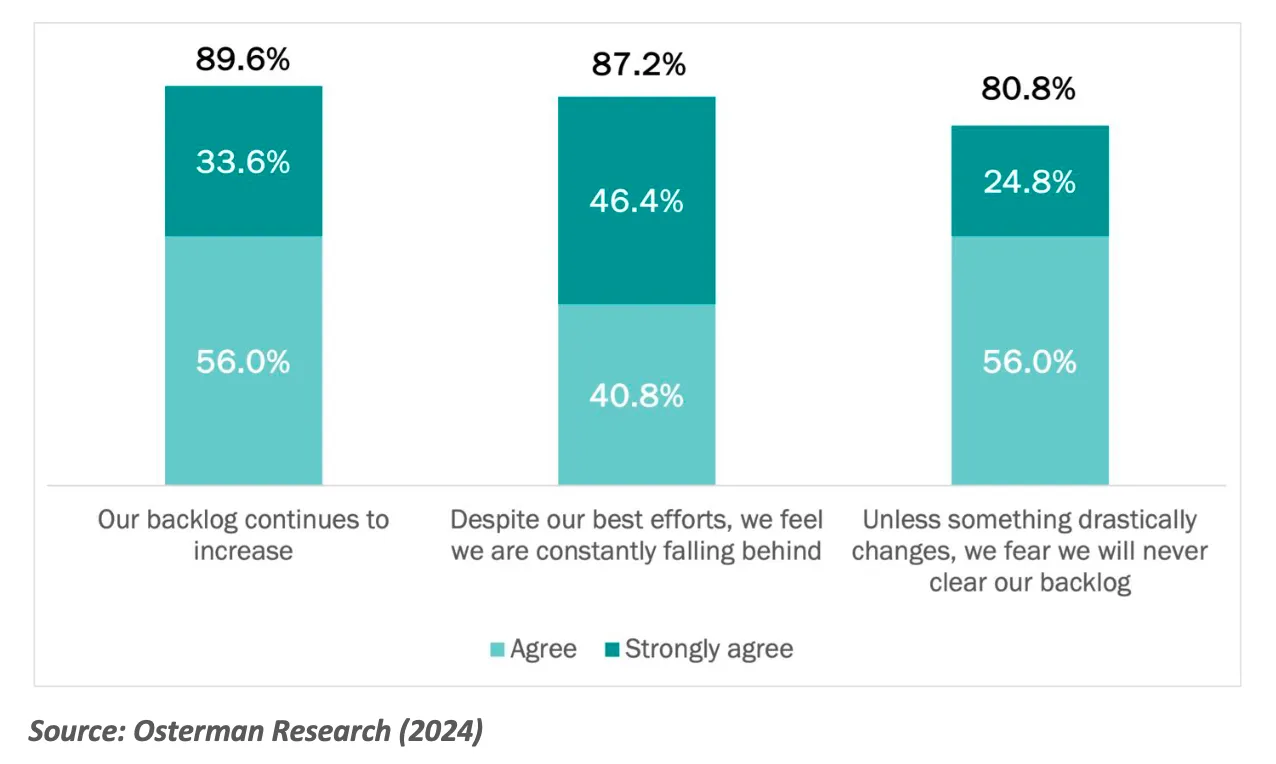
Compounding the issue is the increasing number of alerts that remain uninvestigated. According to our report, “97.6% of the organizations surveyed in this research say that the number of security alerts they must address each day is increasing yearly.” With resources stretched thin, some alerts inevitably fall through the cracks. The ramifications of this growing backlog are significant, as highlighted by a stark observation from the report: “In allowing their backlog to grow, organizations take the gamble that alerts that aren’t addressed do not represent a security risk.”
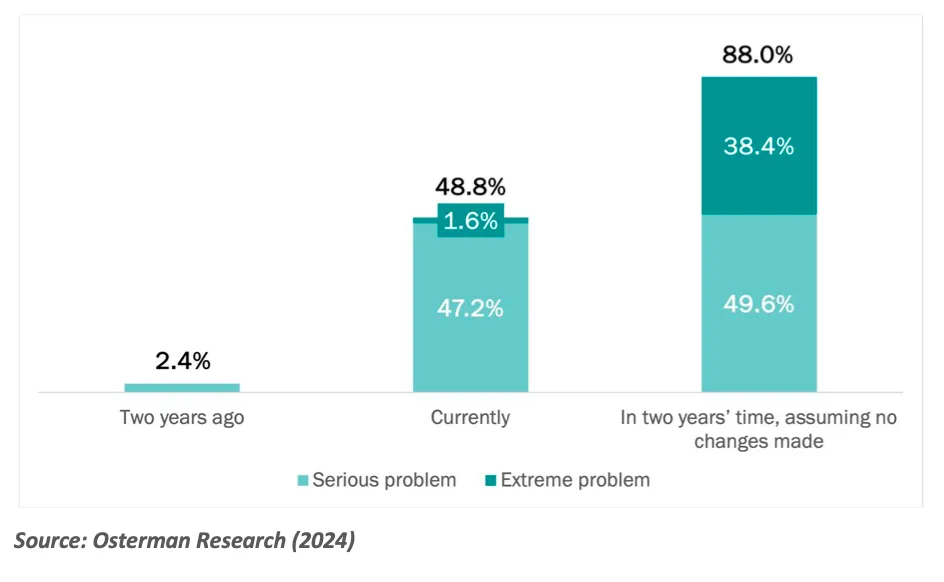
The sentiment among survey participants reflects a sense of gloom, as depicted in Figure 3, “Concerns about the backlog of alerts and incidents that need to be investigated.” The data paints a picture of SOC teams increasingly concerned about their ability to manage the flood of alerts without compromising the quality of their investigations.
Switching Costs: A Silent Killer of SOC Efficiency
A particularly intriguing finding from our recent survey with Osterman Research highlights the complexity and collaborative nature of investigations. The results depicted in Figure 4 show that, on average, 4.6 employees are involved in investigating each security incident.

Investigations frequently involve various specialists, each bringing a crucial skill set to the table. For example, one analyst might possess deep knowledge of the operational or business context, which helps assess the impact of the incident. At the same time, another might specialize in forensic packet or memory analysis, which can be crucial for ascertaining root cause.
The Cost of Collaboration
While this collaborative approach is essential for thorough investigations, it comes with its own downsides:
- Time Cost: Every additional person involved in the incident response process uses up valuable capacity on the security team and delays other work.
- Switching Costs: “Switching costs” refers to the cognitive and operational overhead incurred when employees shift their focus from one task to another, reducing overall productivity.
- Security Risks: Perhaps the most critical implication of extended investigation times is the security risk it poses. The longer an attacker remains undetected or unresolved within the environment, the greater the potential for damage and data theft. Quick and efficient incident resolution is imperative to minimize attackers’ “dwell time.”
The findings suggest that SOCs need to optimize their collaborative processes. Implementing more integrated communication tools, enhancing automated workflows to free up analyst time, and better training in interdisciplinary understanding could potentially reduce the number of personnel needed for each incident.
.webp)
Enter Dropzone AI: Revolutionizing SOC Efficiency
At Dropzone AI, many of us previously worked at vendors that focused on threat detection. But we realize that SOCs have reached a point where adding more detection technology has diminishing returns because the alert triage and investigation process is so onerous.
In a blog describing Dropzone AI’s mission, Dropzone AI CEO and Founder Edward Wu recounts a conversation with a SOC manager: “Being the detection product lead, I was in a feedback session with Michael, the SOC manager, about some of the deep learning-based abnormal data movement alerts we were testing with them and why his team was ignoring them. When I brought up the topic, Michael politely but firmly responded, ‘Edward, I appreciate the math and engineering you guys have put into these detections, but it’s not as valuable as you think. Let me show you why.’ He proceeded to run through a live demonstration of an investigation, from an alert in the SIEM, confirming network telemetry in NDR, pivoting to the EDR, then the file share, and eventually, cross-referencing with the HR system for insider threat possibilities. ‘You see, Edward,’ Michael remarked as the stopwatch hit over fifteen minutes, ‘Surfacing an alert doesn’t change the game. You need to help me understand them.’”
The Dropzone Effect: Spend More Time on Proactive Tasks
Dropzone’s AI-powered SOC analyst technology is designed to address precisely this need to quickly understand alerts. Dropzone AI helps SOCs manage alerts more effectively by significantly improving the triage and investigation processes. We closely monitor and optimize each customer’s key performance metrics, such as Mean Time to Conclude (MTTC). Our results are compelling: we routinely achieve MTTC times under 10 minutes.
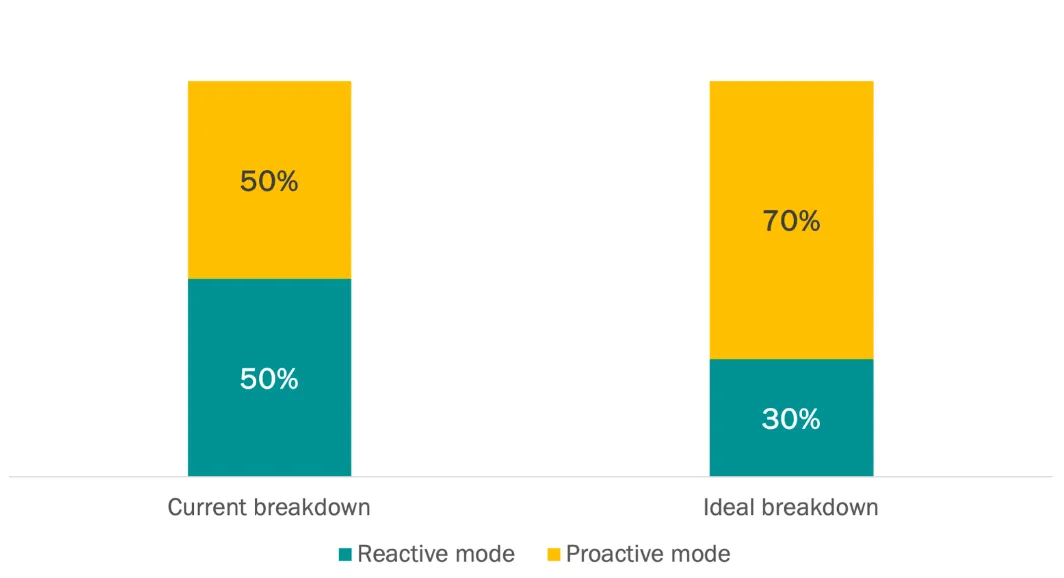
Moreover, our AI SOC analysts are not capacity constrained and can ensure that no alert goes unchecked. With Dropzone AI saving them time, our SOC customers are able to adopt a more proactive security posture—a transformation that SOCs increasingly aspire to, as evidenced by our Osterman survey findings (See Figure 5).
The Impact on SOC Analysts
The integration of AI in alert triage relieves analysts from the tedious and repetitive tasks that dominate their workload, particularly in Tier 1 operations. This shift not only enhances the efficiency and value of SOCs but also significantly improves the job satisfaction and well-being of the analysts. By freeing up their time, analysts can focus on more complex and proactive security tasks, reducing work-related stress and burnout, a prevalent issue highlighted in Figure 6.
Dropzone is excited to continue providing technology that boosts SOC efficiency and significantly enriches the analyst experience. As we advance, our commitment remains strong: to deliver solutions that meet the critical needs of modern SOCs.
Schedule a demo today and discover how an AI SOC analyst can take your SOC operations to the next level.















