Key Takeaways:
- Dropzone AI automates deep investigations across GCP SCC alerts, connecting identity, access, and behavior without manual effort.
- It detects subtle threats, such as privilege escalation and unusual logins, by validating them through real-time log queries, IP analysis, and user context.
- SOC teams no longer need to pivot between audit logs, IAM consoles, and threat intel tools. Dropzone brings all that insight together autonomously.
- Structured, explainable outputs include raw evidence, AI reasoning, and timelines, making it easy to trust, verify, and act.
- With fast setup and immediate value, Dropzone AI turns cloud alert queues into resolved outcomes without playbooks or analyst burnout.
Introduction
Google Cloud Platform's Security Command Center (SCC) does a great job of surfacing unusual activity, such as:
- Logins from unfamiliar geographies
- Suspicious IAM permission changes
- Unusual compute provisioning
But for most security teams, the alert is just the beginning. Determining whether it's a false positive or the first sign of a real compromise requires significant manual effort.
Analysts must dig through:
- GCP audit logs
- User roles and histories
- Activity timelines
- IP reputation data
And when an alert involves sensitive identity activity, such as unauthorized permission elevation or privileged resource access, that investigation becomes both urgent and complex.
That's where Dropzone AI comes in. The autonomous Dropzone AI SOC analyst takes over the heavy lifting the moment a GCP SCC threat is detected. It reasons like an expert human analyst:
- Maps out user roles
- Evaluates behavioral patterns
- Queries relevant logs
- Identifies indicators of compromise
The result is a comprehensive, evidence-based determination of whether the alert is genuine and what to do about it.
What was once a time-consuming manual process is now fast, consistent, and actionable. Dropzone turns raw signals into clear outcomes, no digging required.
What Challenges Do SOC Teams Face Without AI Investigation?
Even when Google Cloud's Security Command Center generates high-fidelity alerts, those alerts often lack the full context analysts need to make a confident decision.
A login from a new geography. A sudden change to IAM roles. An unexpected flurry of compute activity. On the surface, these might suggest trouble, but confirming malicious intent requires hours of investigation.
Security teams are left to manually pivot between:
- GCP consoles and datasets
- Audit logs
- IAM policies
- Google Workspace user history
- IP threat intelligence
It's a fragmented process that demands both deep context and constant focus.
And it's not just about the noise. The most dangerous threats often hide in plain sight: legitimate-looking administrative actions, carried out with just enough subtlety to escape surface-level review. A clever attacker doesn't need to exploit a vulnerability; they just need to:
- Gain access
- Quietly elevate privileges
- Move laterally
The result? Alerts get triaged but not fully investigated. SOC teams, already overwhelmed, are forced to choose between:
- Chasing every lead
- Keeping up with their queues
In that environment, real threats can be missed, and benign anomalies can burn hours of analyst time.
Without AI-powered support, even well-meaning alerts become just another drain on time, attention, and trust.
How Does Dropzone AI Investigate GCP Security Command Center Alerts?
When GCP Security Command Center raises an alert, such as a login from an unusual location or a suspicious IAM role change, Dropzone AI doesn't wait for a human to step in. It immediately launches a full, autonomous investigation, reasoning through the situation like an experienced cloud analyst would.
User Context Analysis
The process begins with user context. Dropzone pulls metadata from Google Workspace to establish a baseline understanding of the user involved. In one case, it recognized that "Bucky Bennett," the account tied to the alert, was an accountant, not someone who should be making IAM policy changes.
Activity Timeline Construction
From there, it dives into activity analysis. Dropzone queries the GCP audit logs surrounding the alert and uncovers a series of actions, such as:
- Creation of multiple compute instances
- Assignment of elevated permissions to another user (EmilyE)
- Configuration changes outside normal patterns
Privilege Escalation Detection
The AI then applies logic for detecting privilege escalation. It notices that Emily's permissions were escalated to "Owner," a significant and unusual jump from her previous role. This type of elevation is a classic red flag for:
- Insider threat
- Compromised account behavior
- Lateral movement attempts
Risk Validation
To validate risk, Dropzone also analyzes the login source, identifying that Bucky's activity came from:
- A Tor exit node
- An anonymized IP address
- A location that doesn't match their historical login behavior
This additional layer of signal reinforces the suspicion.
Evidence-Based Verdict
Finally, Dropzone reaches a verdict one backed by logic, telemetry, and evidence. It compiles everything into a structured, decision-ready report:
- What happened
- Who was involved
- What actions were taken
- Why it matters
No guesswork. No alert backlog. Just clarity.
Dropzone doesn't just investigate across systems. It stitches together identity, behavior, and access patterns to reveal the true nature of the threat.
What Are the Key Benefits for Security Teams?
For most SOC teams, cloud investigations come at a steep cost: hours spent combing through audit logs, correlating IAM role changes, and piecing together timelines across fragmented tools. Dropzone AI eliminates that burden by handling every step of the process automatically, delivering not just speed but depth and confidence in every conclusion.
Faster Alert Resolution
What once took hours of manual effort, including:
- Digging through audit logs
- Reviewing permissions
- Validating IP addresses
Now it happens in minutes. Dropzone investigates as soon as the alert fires, so analysts receive answers without delay. Read how AI SOC analysts compress MTTR.
Context-Rich Insight
Every report is built on more than raw data. Dropzone adds context, highlighting:
- Who the user is
- How their behavior deviates from normal patterns
- What privilege changes occurred
- Whether login IPs align with past activity
No Manual Queries
Analysts no longer need to write custom queries or sift through endless logs. Dropzone automatically:
- Queries GCP audit logs to gather evidence
- Interprets the results
- Stitches them into a narrative that makes sense for the investigation
Structured Evidence
Each investigation is packaged with:
- A clear timeline
- Raw log excerpts
- AI reasoning
- Queries used along the way
Providing transparency, auditability, and confidence in the outcome.
Confidence Without Complexity
Instead of second-guessing or repeating work, analysts receive decision-ready intelligence they can act on quickly, knowing the heavy lifting has already been done.
With Dropzone AI, cloud security teams no longer have to choose between speed and depth. They get both clarity delivered at machine speed, with the rigor of a seasoned analyst built in.
What Makes This Integration Different?
Most tools that claim to "automate" cloud alert triage are only as good as the rules or scripts behind them. They run checks, apply pre-set filters, and move on, often missing the nuance that separates a real threat from a false positive.
Dropzone AI takes a fundamentally different approach.
Instead of following a rigid playbook, Dropzone reasons dynamically through each alert using the OSCAR investigative methodology. It begins with a hypothesis:
Was this login suspicious, or just unusual?
And adjusts its path based on what it finds. That means every investigation is shaped by context:
- The user's role
- Historical behavior
- Privilege changes
- Network indicators
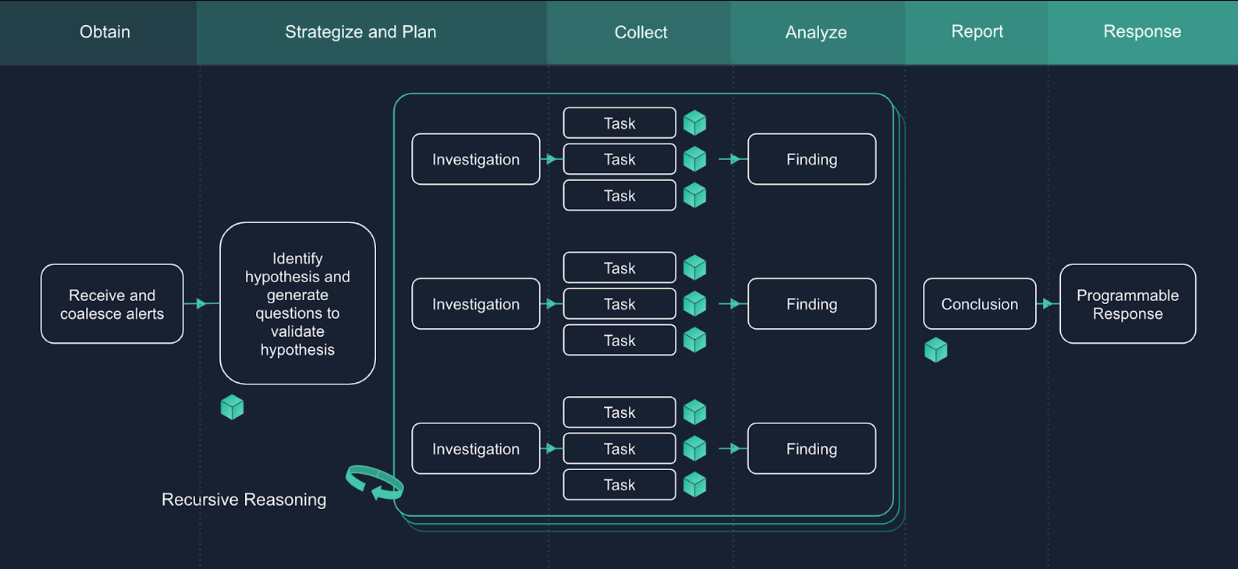
Dropzone doesn't stop at identity or activity. It moves fluidly across layers:
- Querying GCP audit logs
- Examining IAM changes
- Inspecting IP reputation
- Correlating behavior across time and systems
And as analysts provide feedback or validate its findings, Dropzone learns to improve accuracy and adapt to your environment.
This isn't rules-based automation. It's human-like investigative reasoning at machine speed, purpose-built for the complexity of cloud environments like GCP.
How Does Setup & Deployment Work?
Getting Dropzone AI up and running with Google Cloud Security Command Center is designed to be as seamless as possible, with no long ramp-up, no complex configuration, and no heavy lift for your team.
Connect to GCP SCC
Start by establishing secure, read-only API access. This gives Dropzone the visibility it needs to investigate threats without introducing any risk to your environment.
Define Alert Scope
Choose which types of alerts to investigate, such as:
- Geolocation anomalies
- Suspicious IAM activity
- Abnormal resource provisioning
You stay in control of what gets prioritized.
Go Autonomous
Once connected, Dropzone immediately begins triaging alerts and running investigations behind the scenes. There's no need for analysts to:
- Initiate workflows
- Write queries
- Monitor dashboards
Refine Over Time
As analysts review and validate findings, their feedback loops back into Dropzone's learning process, sharpening the AI's logic and making investigations even smarter over time. The Dropzone AI system also learns on its own from investigations, adding new items to context memory. This helps improve accuracy as time goes on.
The result? A frictionless deployment that delivers real impact from day one, while continuously improving.
Turn GCP Signals into Swift, Confident Action
The GCP Security Command Center does a solid job of surfacing alerts, but signals alone aren't enough. Determining whether an unusual login or a suspicious IAM role change is truly malicious requires:
- Time
- Context
- Expertise
That most SOC teams can't spare.
That's where Dropzone AI comes in. Acting as an always-on analyst, it investigates GCP threats the way your best human would, correlating:
- Login behavior
- User intent
- Privilege escalation
- IP reputation
Into a single, coherent verdict. The result isn't just another alert. It's a decision-ready report, complete with:
- Reasoning
- Logs
- Clear next steps
If your team is still spending hours validating cloud threats or triaging ambiguous alerts, it's time to change that.
Book a demo today and see how Dropzone AI investigates GCP threats end-to-end, no playbooks, no guesswork, just clarity at speed.