Effective identity protection measures are no longer optional, they are essential for securing an organization’s critical assets and ensuring its long-term success. The rise in identity attacks, with a staggering 4,000 per second, is indeed a worrying trend. Recent identity-related high-profile security incidents such as the Okta breach from a compromised Single Sign-On account, or the Blackcat/ALPHV ransomware attacks on MGM with access to privileged accounts further highlight the importance of building stronger defenses against this threat. This article explores the Security and Operations Center (SOC) team's challenges in investigating identity-related alerts, the application of generative AI to automate investigations, and how Dropzone AI analysts autonomously investigate identity alerts with a real-world Okta event.
Security teams' challenges with identity alert triaging
Detecting identity attacks is a complex and difficult task. SOC teams face a number of challenges when it comes to triaging and investigating identity-related alerts.
- Fatigue from a high volume of alerts: Identity detection and protection systems generate a large number of alerts, often triggered by brute force scanners from the internet that are employed by malicious actors attempting to crack credentials.
- False positives: SOC teams are inundated with false positives, triggered by harmless events or misconfigurations. This wastes precious analyst time and takes focus away from real threats.
- Staffing shortages: Investigations are time-consuming as they require analysts to log in to different IAM, IDP, SSO logs, and application logs and manually piece data together, gather evidence, conduct user interviews, and correlate to paint a full picture. SOC teams are often understaffed, making it difficult to keep up with the volume of alerts and investigations.
While these challenges are common across other security incidents, there are some unique hurdles specific to identity alert investigations that make it arduous for analysts:
- User behavior context: User behavior is dynamic and unpredictable. It can be hard to distinguish between a legitimate activity and a malicious one without the knowledge of user context and intent. This becomes even more complex when an insider threat is involved as the user activities blend in with normal user behavior.
- Identity data sprawl: User identities are often scattered across multiple systems, HR applications, SaaS solutions, Directory services with inconsistent user privileges that make correlating events a monumental task.
- Extensive skills: It requires staff to be well versed in analyzing logs not only from identity and security tools but also log formats and schema of various applications that the enterprise uses.
- Evolving threats: Social engineering tactics such as Account Takeover (ATO) attacks involve tricking users into revealing sensitive information. With Generative AI, it now takes less than 3 seconds to write a phishing email or clone someone’s voice making it easy to scam unsuspecting humans. It can be difficult to detect these types of identity threats with traditional controls and requires deeper investigation.
- Broader collaboration: Investigating identity-based alerts requires collaboration with IT and other associated entities related to the alert for successful incident resolution.
Using Agentic AI for faster, more efficient identity threat alert investigations
Agentic AI I has emerged as a game changer that can transform the way SOC teams respond to alerts by automating alert investigations. AI agents can handle large volumes of alerts, automate repetitive tasks of gathering data from various sources, analyze vast amounts of data and context at greater speed, and identify if an event is malicious or not - almost replicating the thought process of a Tier 1 analyst. By effectively filtering out the noise, Gen AI can significantly reduce the time spent on false alerts and free up time to address critical threats.
Accurate, autonomous identity threat alert investigations with Dropzone AI
Dropzone AI was developed to augment your SOC with AI analysts that can thoroughly and autonomously investigate every single alert, replicating hours of expert analysis. As part of the autonomous alert investigation, the system performs detailed multi-hop log analysis across different log types and sources regardless of the variations in data formats. It takes the investigation further by conducting inquiries and interviewing the parties involved through an interactive AI chatbot to gather context. It uses a recursive reasoning process vs if-else type automation, does not rely entirely on threat intel, and can recognize unusual patterns and unknown threats to definitively conclude if an event is malicious.
Key factors for effective agentic AI investigation
Dropzone AI’s unique ability to conduct effective autonomous investigations with precision is driven by the following key criteria:
- Pre-training: Our AI systems are pre-trained and as a result, know how to investigate identity-based alerts from day one of deployment rather than learning from human analysts after deployment.
- Extensive integrations with existing security tools: It seamlessly integrates with customers’ existing tools so it can tap into organization-specific data, understand context, and draw conclusions with improved precision.
- Human-in-the-loop: It is built with a human-in-the-loop mindset. Transparency is key. Every single action, investigation, and deduction is traceable to real data, not black box algorithms. The system is able to prove its recommendations in the form of a detailed report with a severity conclusion, executive summaries, and key evidence that instills confidence that it isn’t hallucinating.
Investigating identity threat alert with Dropzone AI: A real-life example
This section below shows in detail how Dropzone AI conducts a thorough end-to-end investigation of a real-world Okta Threat Insight alert emulating the thought process of an expert SOC analyst.
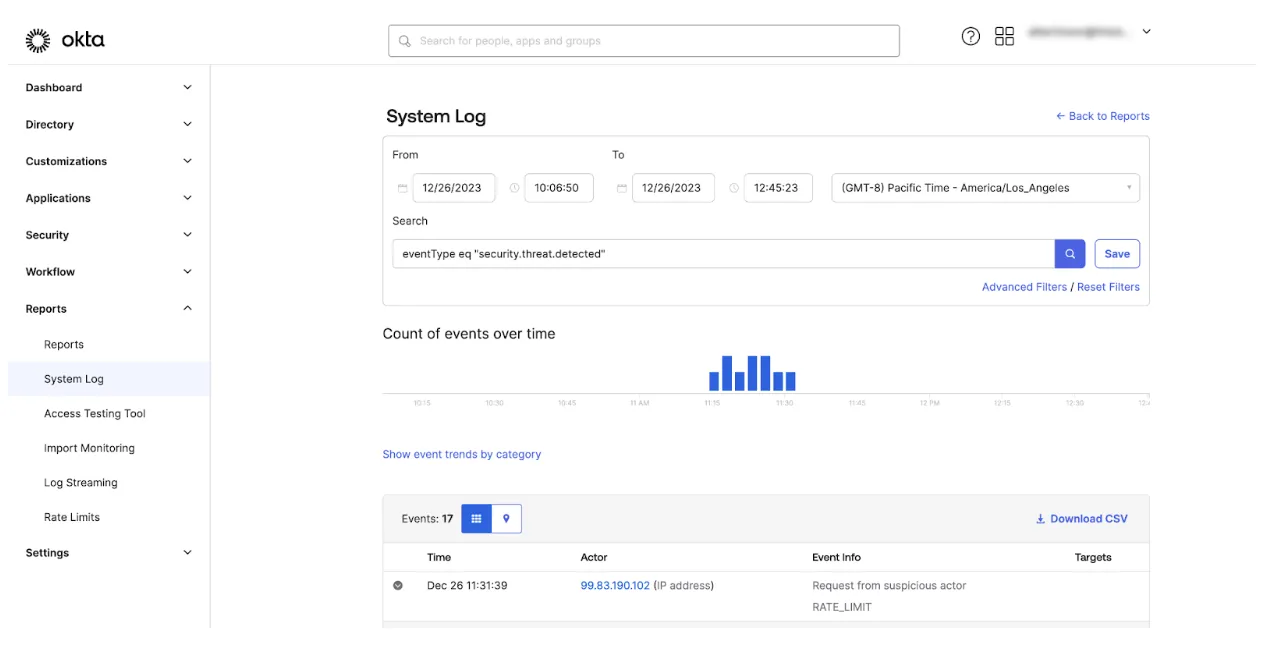
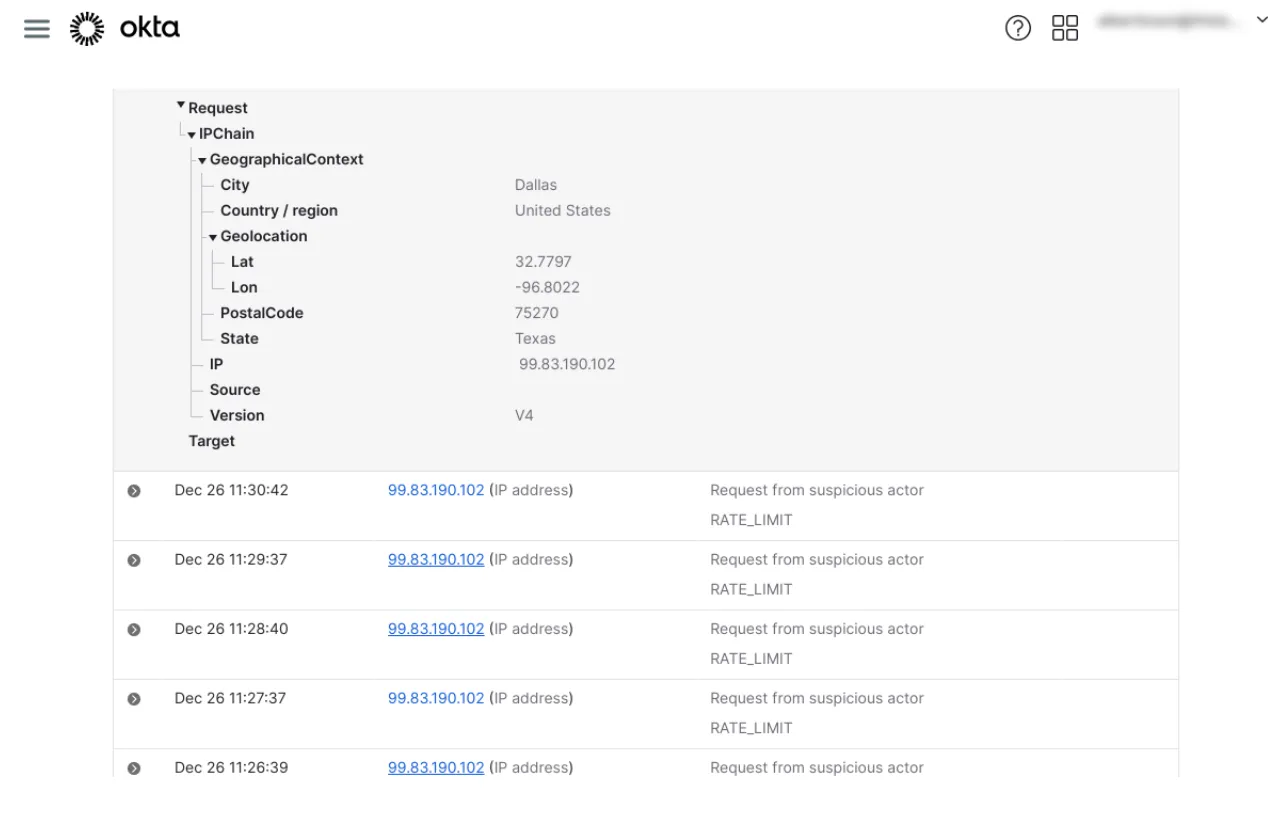
In this example, Okta flagged a series of login attempts and rate-limited them. But it is difficult to tell in this view whether they correlate to a real breach. A human analyst might overlook this, assuming it is merely another random scanner on the internet. Dropzone’s pre-trained AI analyst, however, did a thorough investigation in just a few minutes and flagged this as malicious.
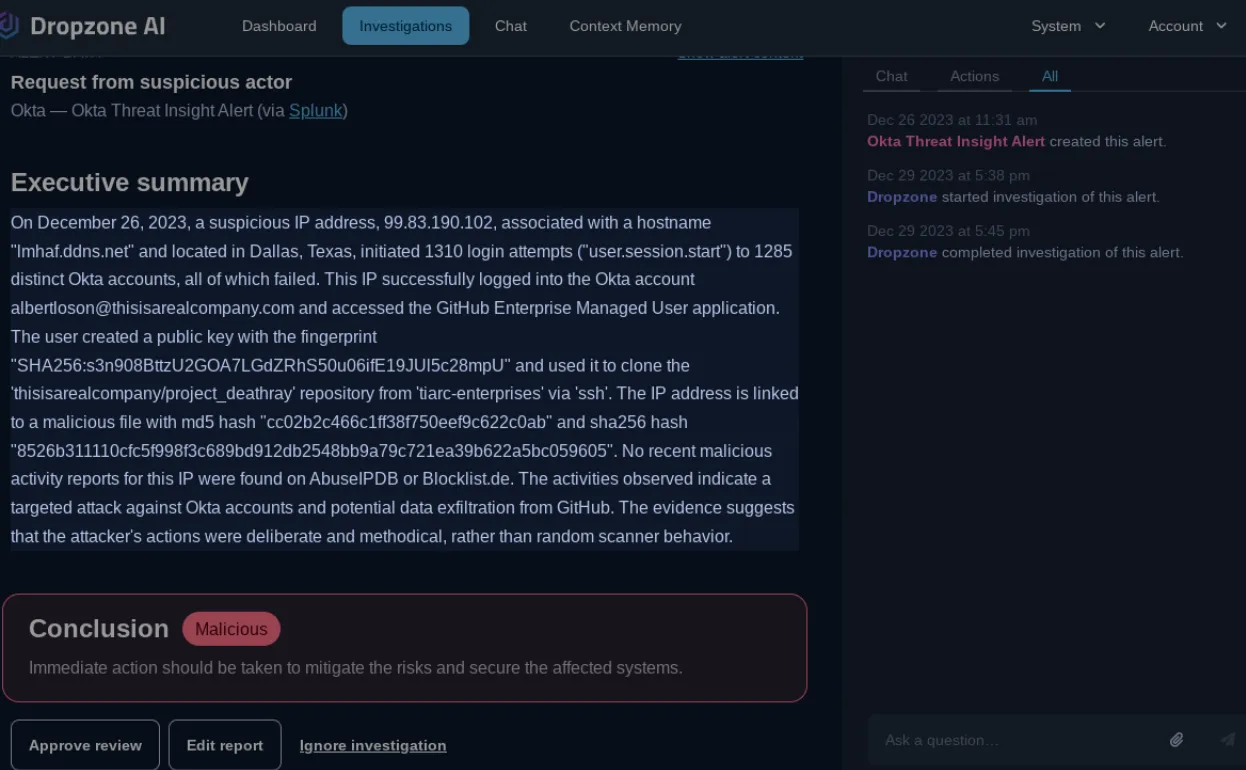
The system then generated a comprehensive report with a conclusion, executive summary, step-by-step process, and key factors that were used to arrive at the conclusion that it was malicious.
To perform this analysis, the system programmatically generated SPL queries based on the investigation needs. In this case, relevant Okta audit logs were automatically retrieved and analyzed to build a clearer picture of the backstory.
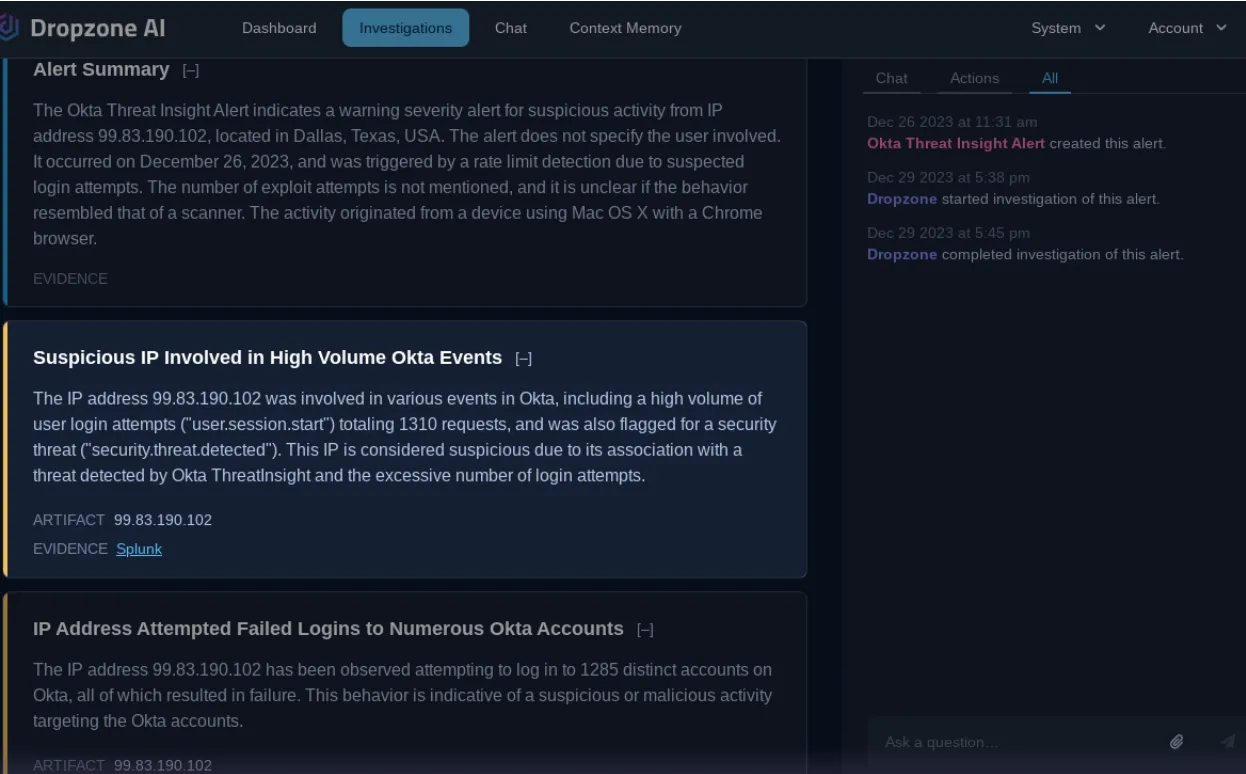
The AI analyst confirmed through log analysis that the attacker successfully authenticated with the account “albertloson@thisisarealcompany.com” in Okta. With that info, it proceeded to figure out what actions the attacker took after gaining access. It examined which Single Sign-On applications the IP address accessed through Okta and identified that it was Github.
The AI analyst further examined Github logs associated with the compromised user and found that the user account has been actively creating and verifying a public key in the Github Enterprise Managed User application.
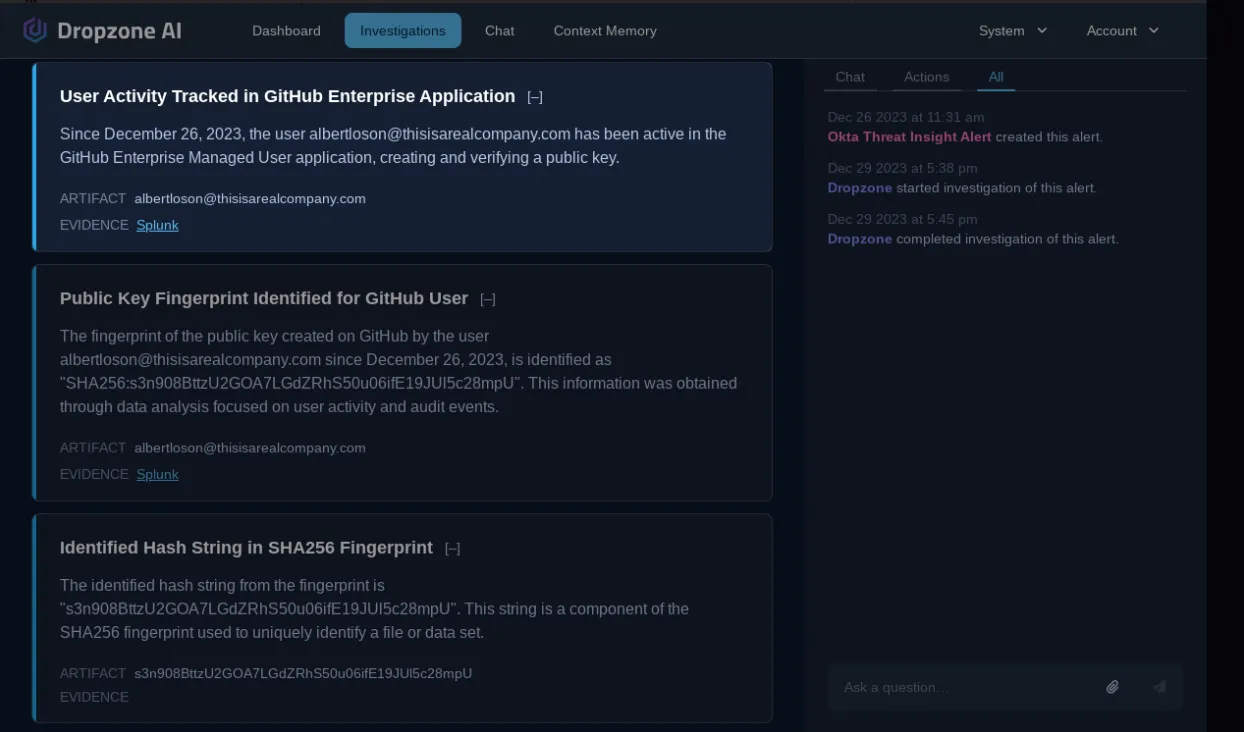
Then, it traced the fingerprint of the new public key in Github logs that showed that the attacker had successfully gained access to a code repository. This type of multi-hop application log analysis is time-consuming and challenging due to the familiarity required with Okta and Github log formats. With AI augmentation, the security team can significantly speed up investigations without being a log analytics guru.

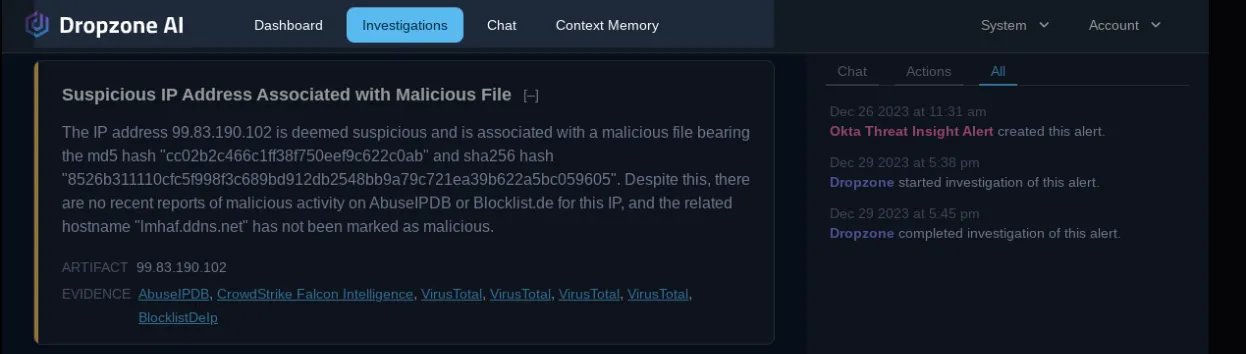
It further traced the IP address and found that it was malicious, even though this IP address is not known to scanning services VirusTotal, AbuseIPDB, and Blocklist.de. A human analyst relying only on traditional threat intel services would have missed this detail.
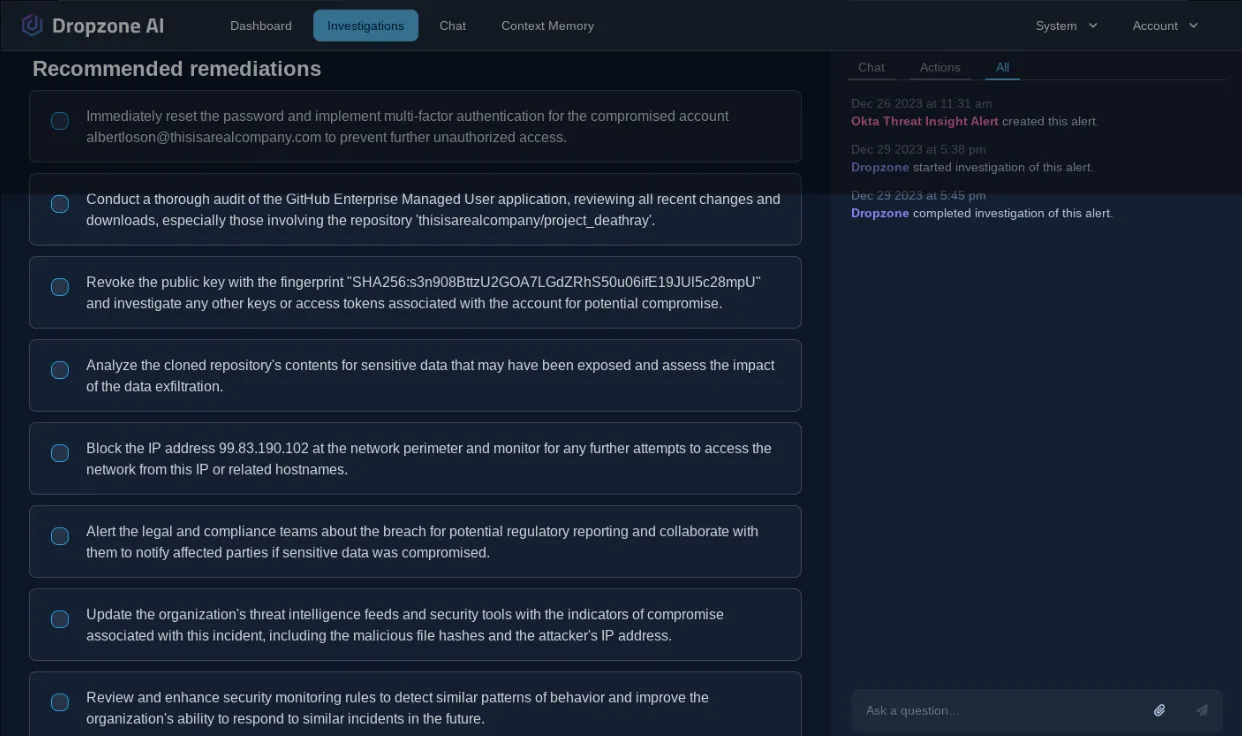
Finally, it wrapped up the investigation with remediation recommendations for the SOC analyst.
Get to the bottom of every identity alert event
Reinforce your SOC with Dropzone AI security automation and get to the bottom of every identity alert fast. No playbooks or manual interventions are needed. Request a demo or take a test drive today!















