The growing challenges of investigating endpoint alerts
Endpoint protection plays a significant role in cybersecurity defense. As a result, endpoint security solutions are a key component in every Security and Operations Center (SOC). However, SOC teams face several challenges when investigating endpoint alerts, often arising from a combination of the following key factors:
- Flood of alerts: Modern Endpoint Detection and Response (EDR) solutions collect large volumes of data - event logs, file actions, registry keys, information about software applications, and more. With hundreds or thousands of endpoints generating alerts in an organization, it is not uncommon to have large volumes of alerts that the SOC teams can handle. The sheer volume of alerts and data can quickly overwhelm SOC teams.
- Security tool limitations: While EDR solutions collect a variety of telemetry data, these alerts may lack crucial contexts like user behavior, network interactions, the organizational context of the host, and other forensic artifacts. For example, take the PrintNightmare exploit (CVE-2021-34527). The EDR system may alert to an exploit attempt on a system that matches the signature of this vulnerability. However, if the impact extends beyond managed hosts, the EDR will not provide details of the extent of the impact within the network. This makes it difficult for analysts to assess the severity and urgency readily. The onus then falls on the SOC teams to juggle data from various security tools, endpoints, and network sources, then run queries to correlate evidence and, finally, paint a complete picture of the incident. This consumes analyst time, leading to extended investigation time and delayed action on critical threats.
- Resource constraints: SOC teams are already overstretched and understaffed. Adding more analysts to the problem isn't a scalable solution. Adding more tools to integrate data and simplify workload ends up generating new types of alerts that analysts have to deal with. Security Orchestration, Automation, and Response (SOAR) solutions may offer promise, but they fail to deliver comprehensive end-to-end security automation. Read our blog post Moving Beyond the Limits of SOAR Playbooks for Automation, for more details.
Under the weight of these challenges, it is unsurprising that security teams are able to get to only 50% of alerts in a typical workday, leaving gaps in defenses. Manual analysis further cripples their efforts with 81% reporting that manual investigations slow down their overall threat response times.
Leveraging the power of Gen AI for endpoint alert investigations
Advancements in Gen AI and Large Language Models (LLMs) can completely transform alert investigations for SOC teams. Gen AI systems can be trained to replicate the thought processes and techniques of Tier 1 analysts, autonomously investigate 100% of alerts, and help analysts focus on true positives faster.
Requirements for effective AI-based investigations
To accurately and autonomously analyze endpoint alerts, it is critical that the AI system meets the following key requirements:
- Pre-training: The system should be pre-trained and as a result, know how to investigate endpoint alerts from day one of deployment rather than learning from human analysts after deployment.
- Extensive integrations with existing security tools: It should seamlessly integrate with the customer’s existing tools so it can tap into organization-specific data, understand context, and identify with improved precision.
- Human-in-the-loop: It should be built with a human-in-the-loop mindset. Transparency is key. Every single action, investigation, and deduction should be traceable to real data, not black box algorithms. The system should be able to prove its action and avoid hallucinating to maintain trust and confidence.
These above-mentioned criteria are precisely what guide Dropzone’s approach to autonomous alert investigations.
Accelerate endpoint security investigations with Dropzone AI
Dropzone helps SOC teams leverage the power of pre-trained AI security analysts to perform autonomous alert investigations. The AI analysts replicate expert human analysts’ decision-making process, understand your team and company’s context, and adapt to an ever-changing threat landscape to thoroughly and autonomously investigate all alerts. As part of the autonomous alert investigation, the system swivel-chairs and collects data from various sources such as EDR, SIEM, network logs, and threat intel, conducts inquiries through an AI chatbot, gathers context to perform detailed analysis, and determines if an alert is a genuine threat or a false positive. No playbook or code deployment is needed.
Investigating endpoint alert with Dropzone AI: A real-life example
This section below shows in detail how Dropzone conducts a thorough end-to-end investigation of a real-world Microsoft Defender alert emulating the thought process of an expert SOC analyst.
In this example, Microsoft Defender has blocked a malicious executable file and sent an alert to the security team for review.
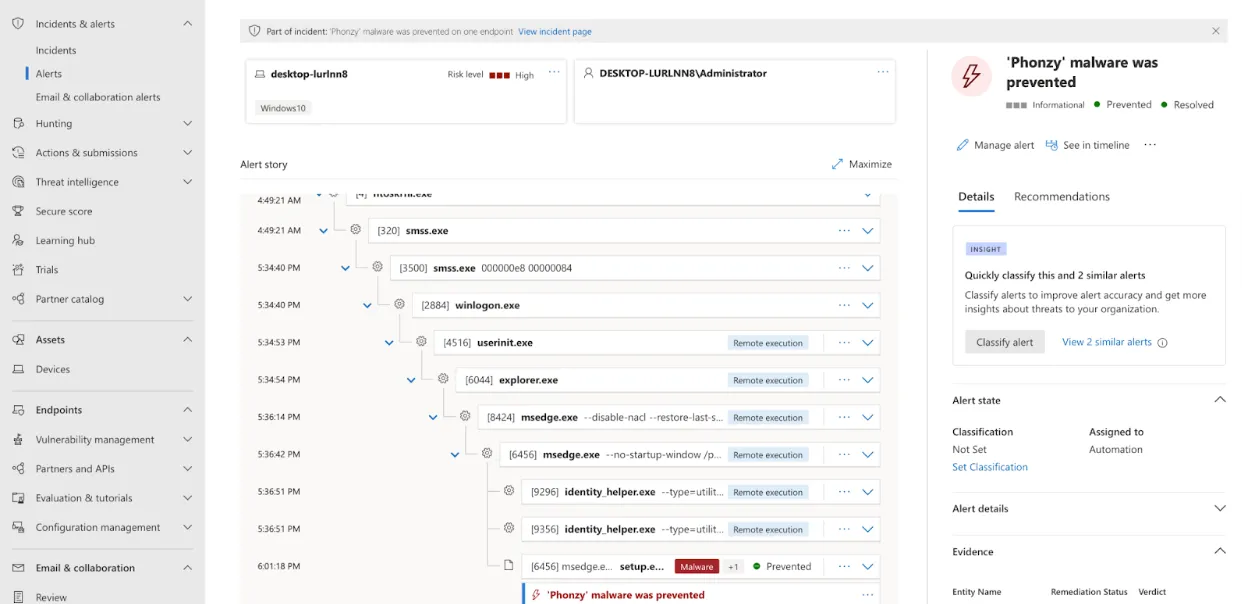
Before a human analyst could intervene, Dropzone AI determined that this alert required immediate action, picked it up for review, and analyzed it within 12 minutes. No human clicks, coding, or playbook execution was needed. The investigation was completely autonomous and tailored for the specific alert swivel chairing across endpoint logs, sandbox analysis, and network logs.
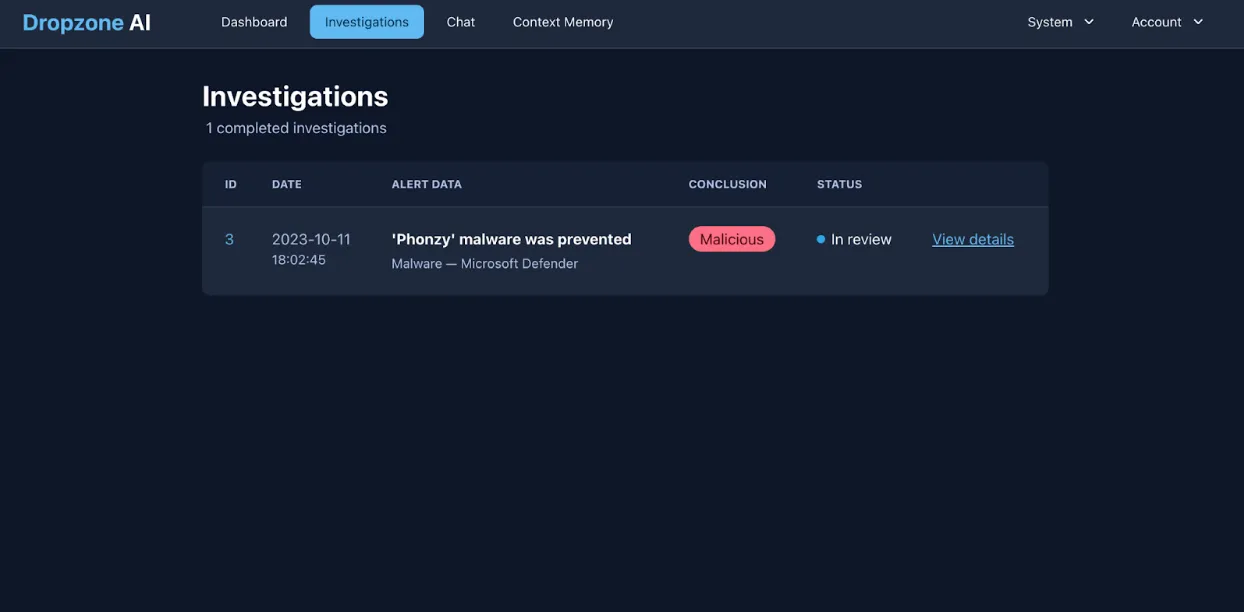
The system then generated a comprehensive report, with the conclusion, executive summary, step-by-step process, and key factors that Dropzone AI used to arrive at the conclusion that it was malicious.
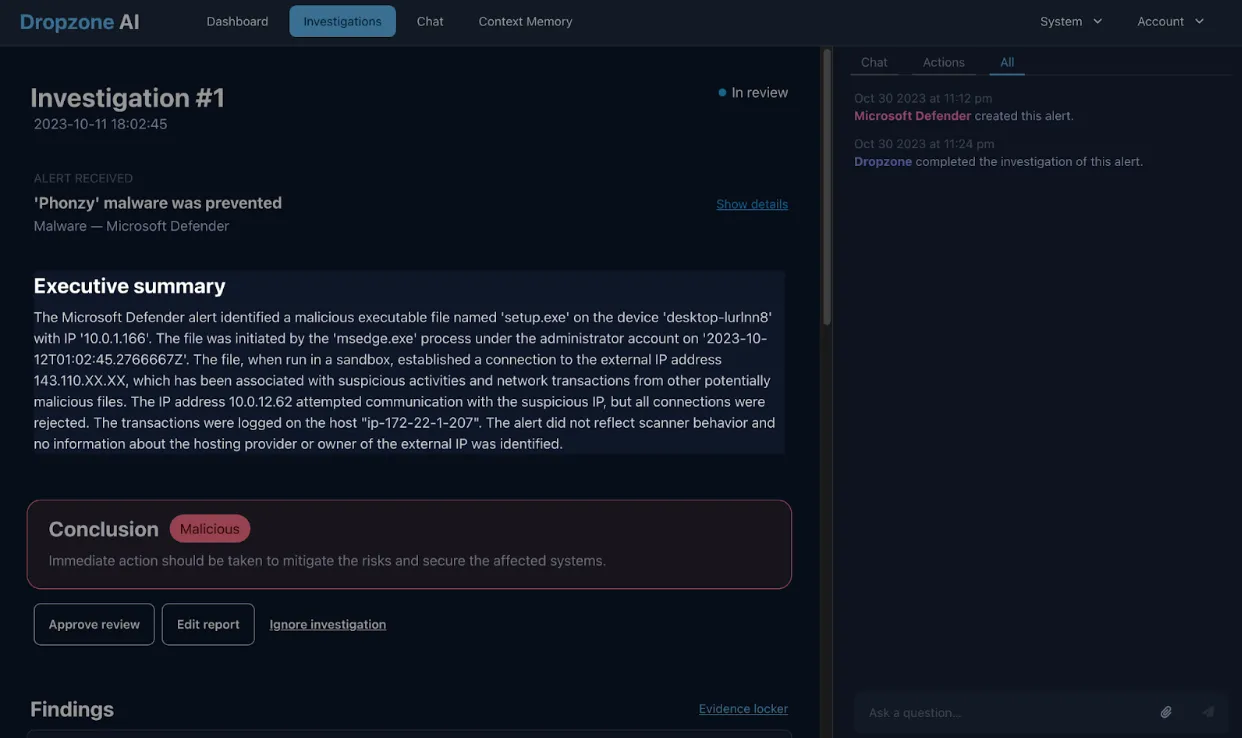
First, the AI analyst identified that the user tried to execute a malicious executable from MS Edge, which is typical for Drive by Download attacks. Then, it looked to gather further evidence of this activity.
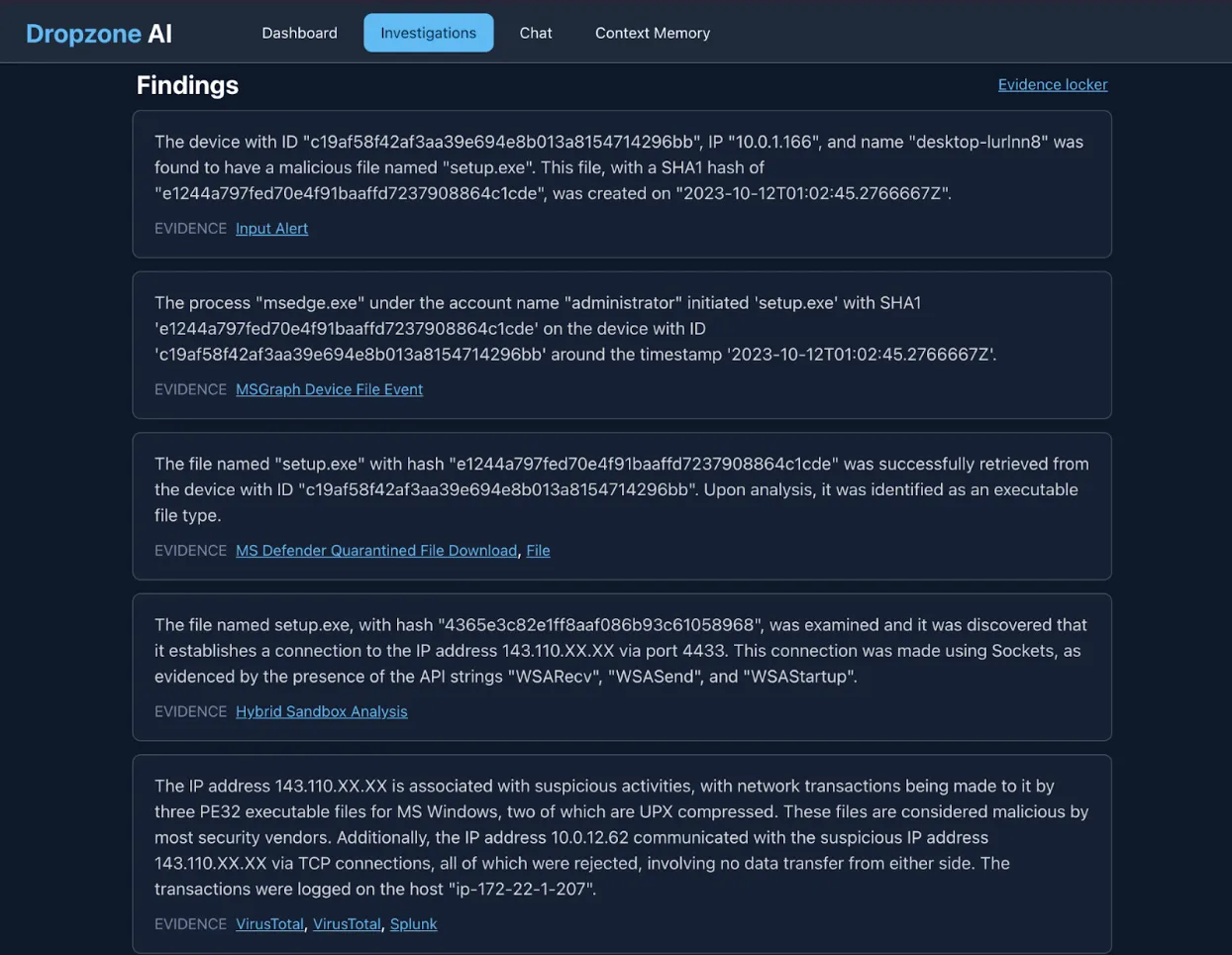
The AI analyst automatically generated relevant queries against the Microsoft 365 Defender advanced hunting API and found evidence of the user attempting to execute the file.
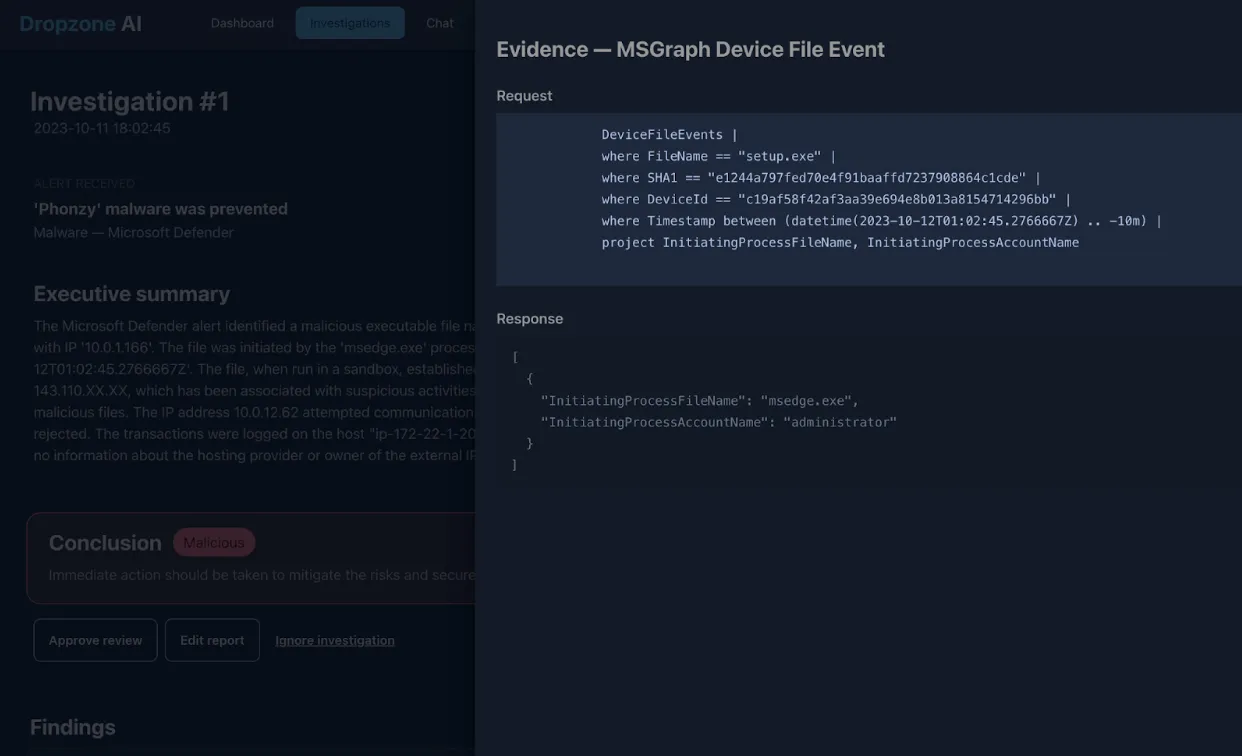
Now, most analysts would have stopped at this point because the malware was successfully blocked before any execution.
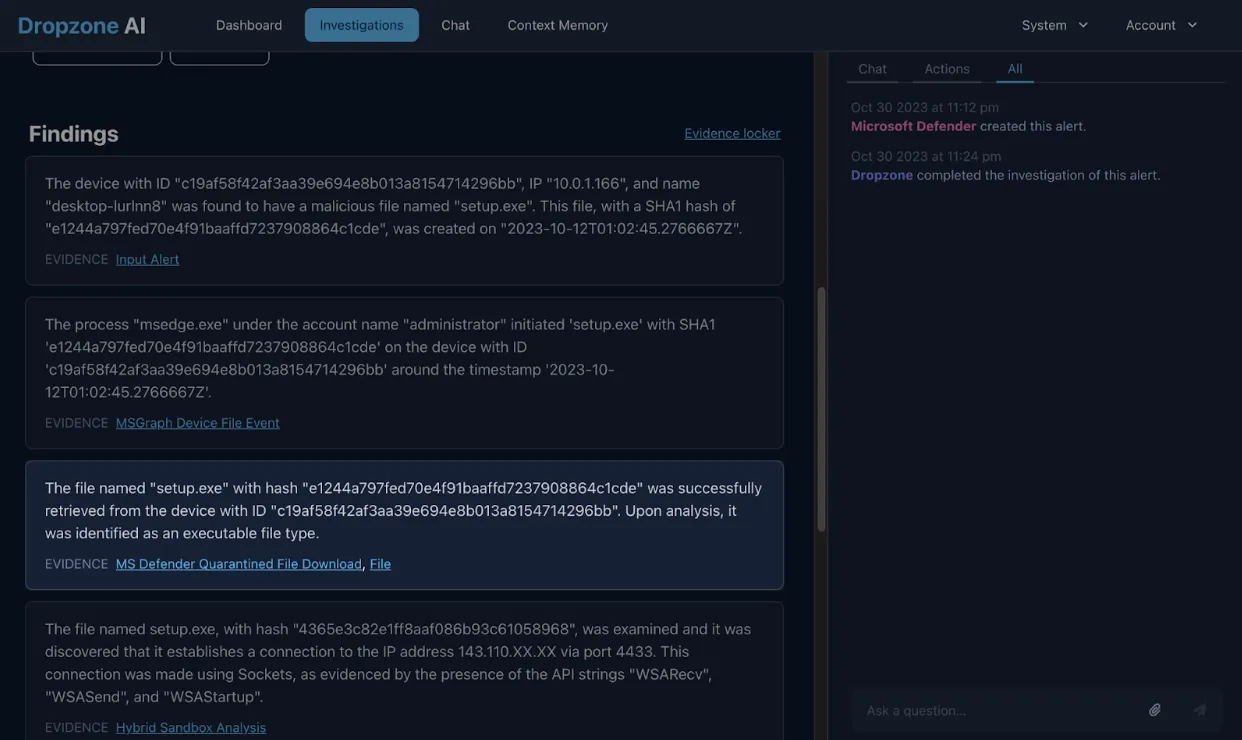
However, the AI analyst further examined the file through the sandbox and discovered that the file reached out to an external IP after execution.

It further validated that the IP is indeed real.
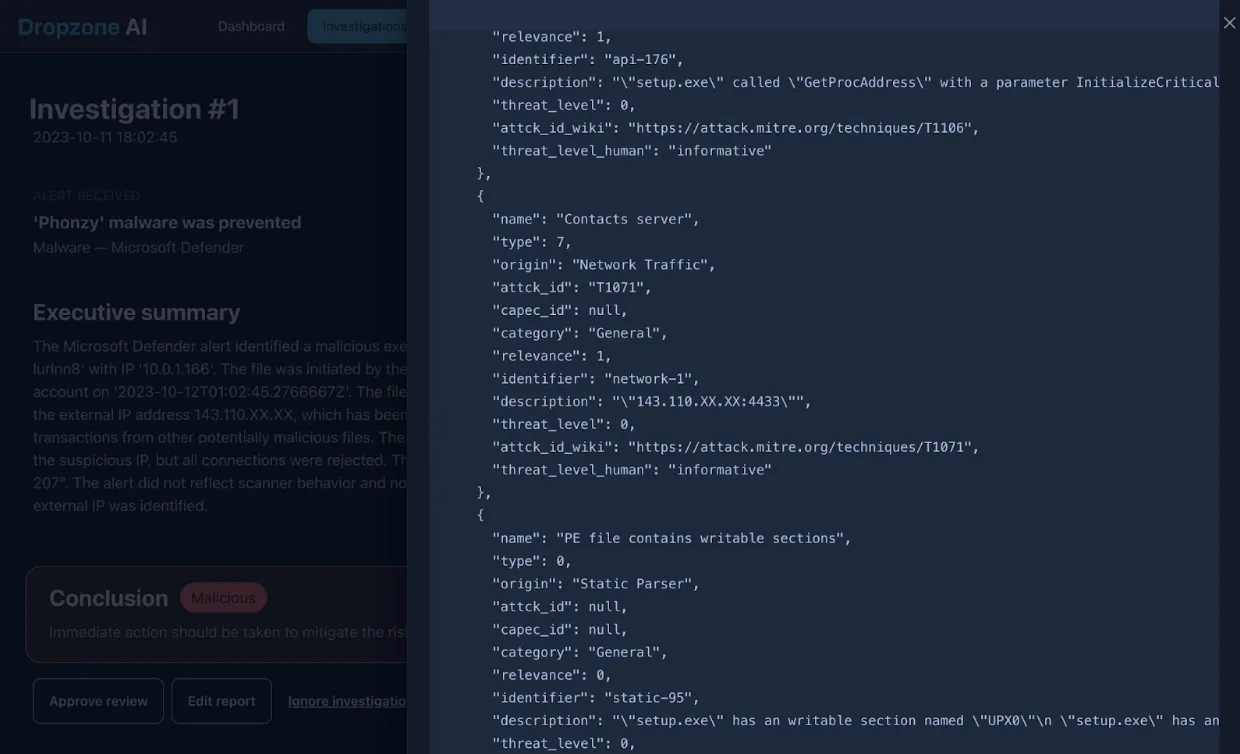
The AI analyst then verified with threat intelligence sources that confirmed that the IP address was associated with malicious executables. It also assessed its impact on the network and found evidence from network logs in Splunk that another device within the network was attempting to connect to this IP.
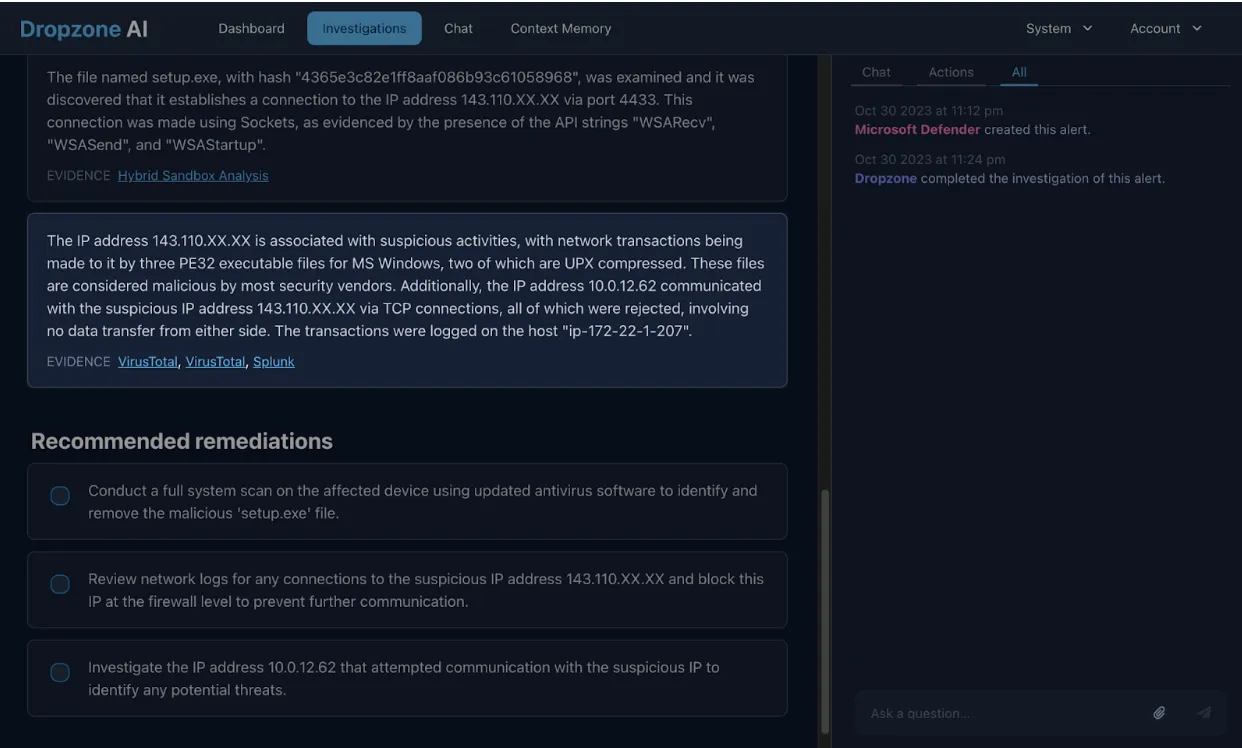
It concluded that the event was malicious and wrapped up the investigation with recommended remedial actions all in a matter of 12 minutes. This would have taken a human analyst up to 30 minutes or even longer if they were not familiar with the tooling involved.
Augment your SOC team with Dropzone AI
Dropzone AI substantially reduces the investigation time of each alert, which means SOC teams can process many more alerts every hour. With the ability to scale on-demand, backlogs that previously took hours to clear can be resolved within minutes. Furthermore, Dropzone enhances alert investigation capabilities with existing security tools, eliminating the need for costly and complex data integrations to simplify SOC workload.
Empower your SOC team with Dropzone AI, offload mundane investigation tasks, and significantly reduce your mean time to respond to threats. Request a demo or take a test drive today!















