Introduction
Most security teams operate reactively:waiting for alerts to fire, responding to incidents, investigating what automated tools flag. Meanwhile, sophisticated threats operate undetected for months, moving laterally through networks, escalating privileges, and positioning for maximum impact. The shift to proactive threat hunting changes this dynamic entirely. Instead of waiting for detection tools to catch threats, your team actively searches for evidence of compromise, behavioral anomalies, and attack patterns that automated defenses miss.
What Is Threat Hunting and Why It Matters in 2026
Threat hunting is the proactive process of searching through networks, endpoints, and datasets to identify and mitigate cyber threats that have evaded traditional security measures. Unlike reactive approaches that depend on automated alerts, threat hunting assumes compromise has already occurred and actively searches for evidence of malicious activity.
The mean time to identify a breach is 181 days (IBM 2025). While your security team waits for alerts, threats lurk undetected in your network: moving laterally, escalating privileges, exfiltrating data. Traditional reactive security (waiting for automated tools to trigger alerts) misses the sophisticated attacks that matter most.
Why 2026 Changes Everything
Identity-focused attacks have overtaken malware as the primary attack vector.
Breakout times (the window between initial compromise and lateral movement) have dropped below one hour for advanced threat actors.
Internal detection matters: 50% of breaches are identified by organization's security teams through proactive investigation, not automated detection (IBM 2025).
Proactive threat hunting directly attacks the 181-day problem. By actively searching for threats instead of waiting for alerts, security teams reduce dwell time, uncover advanced persistent threats (APTs) before damage occurs, and improve overall security posture through continuous learning.
Core Threat Hunting Approaches
Hypothesis-Driven Threat Hunting
Hypothesis-Driven Threat Hunting starts with a theory. Based on threat intelligence, industry trends, or observed anomalies, hunters form a hypothesis about potential threats lurking in their environment, then use data and analysis to confirm or deny suspicions.
Indicators of Compromise (IOC) Threat Hunting
Indicator-Based (IOC) Threat Hunting uses known indicators of compromise from threat intelligence feeds. Hunters search for matches to known malicious signatures, IP addresses, domains, or file hashes. This provides an accessible starting point for organizations building capabilities.
Baseline and Anomaly Hunting
Baseline and Anomaly Hunting establishes what "normal" looks like for users, systems, and networks, then searches for deviations. This leverages behavioral analysis and machine learning to detect novel threats and insider risks.
Most effective programs integrate all three: hypothesis-driven for strategic work, IOC for tactical intelligence, anomaly detection for unknown threats.
Essential Frameworks: MITRE ATT&CK, Kill Chain, Diamond Model
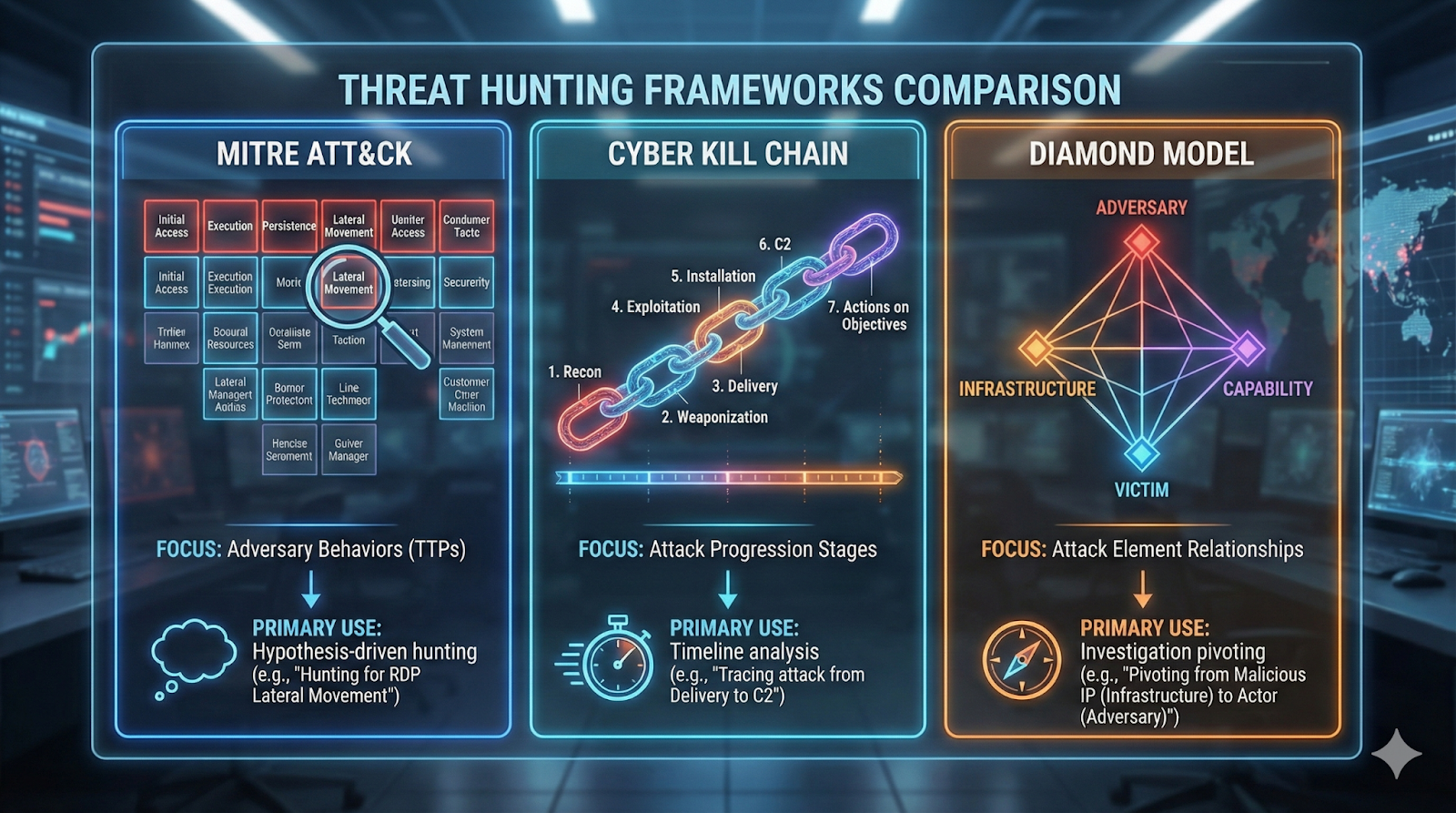
MITRE ATT&CK
MITRE ATT&CK is the industry-standard knowledge base of adversary tactics, techniques, and procedures (TTPs). It organizes threat behaviors into 14 tactical categories (from Initial Access through Exfiltration) based on real-world observations. MITRE ATT&CK enables hypothesis-driven hunting by providing a common language for discussing adversary behaviors.
The Cyber Kill Chain
The Cyber Kill Chain models cyberattack progression through seven stages:
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command & Control
- Actions on Objectives
The Kill Chain helps hunters focus investigations on different attack stages and emphasizes early-stage disruption.
The Diamond Model
The Diamond Model focuses on four core features (Adversary, Infrastructure, Capability, Victim) and relationships between them. Useful for pivoting during investigations when you discover one element and need to find related attack components.
For deeper exploration of how AI automates framework application, see our guide on [threat hunting frameworks](link to Feb 7 piece).
The AI-Augmented Threat Hunting Model
The Challenge:
- 79% of SOCs operate 24/7 (SANS SOC Survey 2025)
- Alert fatigue overwhelms analysts
- Lack of skilled staff is the top barrier to sophisticated threat hunting (SANS 2025)
- Reactive triage consumes time needed for proactive hunting
The Solution: AI Augmentation
AI-augmented SOC platforms automate routine Tier-1 alert investigation. When AI handles the repetitive work (correlating logs, enriching context, determining if alerts represent genuine threats), it frees experienced analysts to focus on what humans do best:
- Forming hunting hypotheses
- Investigating complex attack chains
- Making strategic security decisions
Augmentation, Not Replacement
AI investigates alerts autonomously 24/7, but analysts maintain oversight:
- AI gathers evidence and correlates data
- Analysts review investigations and make decisions
- AI doesn't replace judgment (it enhances capacity)
Measurable Impact:
- AI and automation shorten breach lifecycle by 80 days (IBM 2025)
- Analysts spend less time on reactive triage
- More time on proactive hunting that reduces risk
Building a Threat Hunting Program: Key Considerations
Team Structure and Staffing
Typical SOC: 10 full-time equivalents (SANS 2025)
Required Skills:
- Network analysis
- Malware analysis
- Digital forensics
- Threat intelligence
Reality Check: Lack of skilled staff is the top barrier to sophisticated threat hunting (SANS 2025). AI-augmented tools extend capabilities while you build expertise.
Data Requirements
Essential log sources:
- SIEM aggregation
- EDR endpoint telemetry
- Network traffic analysis
- Cloud environment logs
Critical: Data retention policies that support historical analysis. You can't hunt for evidence that's been deleted.
Tool Integration
85% of SOCs rely on endpoint security alerts as their primary response trigger (SANS 2025). Your hunting program must integrate with existing stack through API connectivity to SIEM, SOAR, EDR, and XDR platforms.
Success Metrics
Track what matters:
- Mean Time to Detect (MTTD) for hunted threats
- Threats discovered beyond automated detection
- False positive reduction
- Analyst time saved through automation
- Environment coverage percentage
Key Takeaways
- Threat hunting is the proactive process of searching for threats that evaded traditional security measures, directly addressing the 181-day detection problem
- Essential in 2026 as threat actors operate at machine speed using identity-focused attacks that bypass signature-based detection
- Three core approaches work together: hypothesis-driven for strategic hunting, IOC-based for tactical intelligence, anomaly detection for unknown threats
- Industry-standard frameworks (MITRE ATT&CK, Cyber Kill Chain, Diamond Model) provide structured methodologies for systematic hunting
- AI-augmented SOC platforms handle routine Tier-1 alert triage autonomously, freeing analysts to focus on proactive threat hunting
Learn More About AI-Augmented Threat Hunting
Dropzone AI's autonomous alert investigation platform handles routine security alerts 24/7, freeing your SOC team for proactive threat hunting. Our AI SOC analysts integrate with your existing tools, adapt to your environment, and generate decision-ready reports. No playbooks, code, or prompts required.
Explore AI-augmented investigation at dropzone.ai/threat-hunting.














