Introduction
Your SOC team knows MITRE ATT&CK. They understand the Pyramid of Pain. They've studied the Cyber Kill Chain. But turning framework knowledge into repeatable and well-executed threat hunts? That's where most teams struggle. Manual framework application requires deep expertise, time-intensive correlation across tools, and sustained focus that 24/7 operations make impossible. AI-augmented platforms change the equation by automating the systematic application of threat hunting methodologies while keeping analysts in control of strategy and response.
Why Threat Hunting Frameworks Matter
What is a threat hunting framework? It's a structured methodology that guides security analysts in proactively searching for hidden threats that evade automated detection.
Unlike ad hoc hunting (aimlessly searching logs hoping to find something), frameworks provide a common way to describe attacker behavior. Threat hunters can use frameworks to plan hunts based on:
- Adversary behaviors
- Indicator durability
- Attack progression patterns
Why They Matter
Frameworks provide a common lingua franca for security professionals to describe attacker activity, and threat hunters can use IOCs and TTPs in threat reports to plan hunts.
Behavior-based detection is essential: 81% of intrusions from July 2024 through June 2025 were malware-free, requiring behavior analysis rather than signature matching.
Consistency across teams: 79% of SOCs operate 24/7 (SANS 2025), often with mixed experience levels. Frameworks ensure investigation quality doesn't vary by analyst or shift timing.
Efficiency through structure: Ad hoc hunting wastes time. Frameworks prioritize high-impact activities (TTPs that take adversaries months to change vs. indicators they change in seconds).
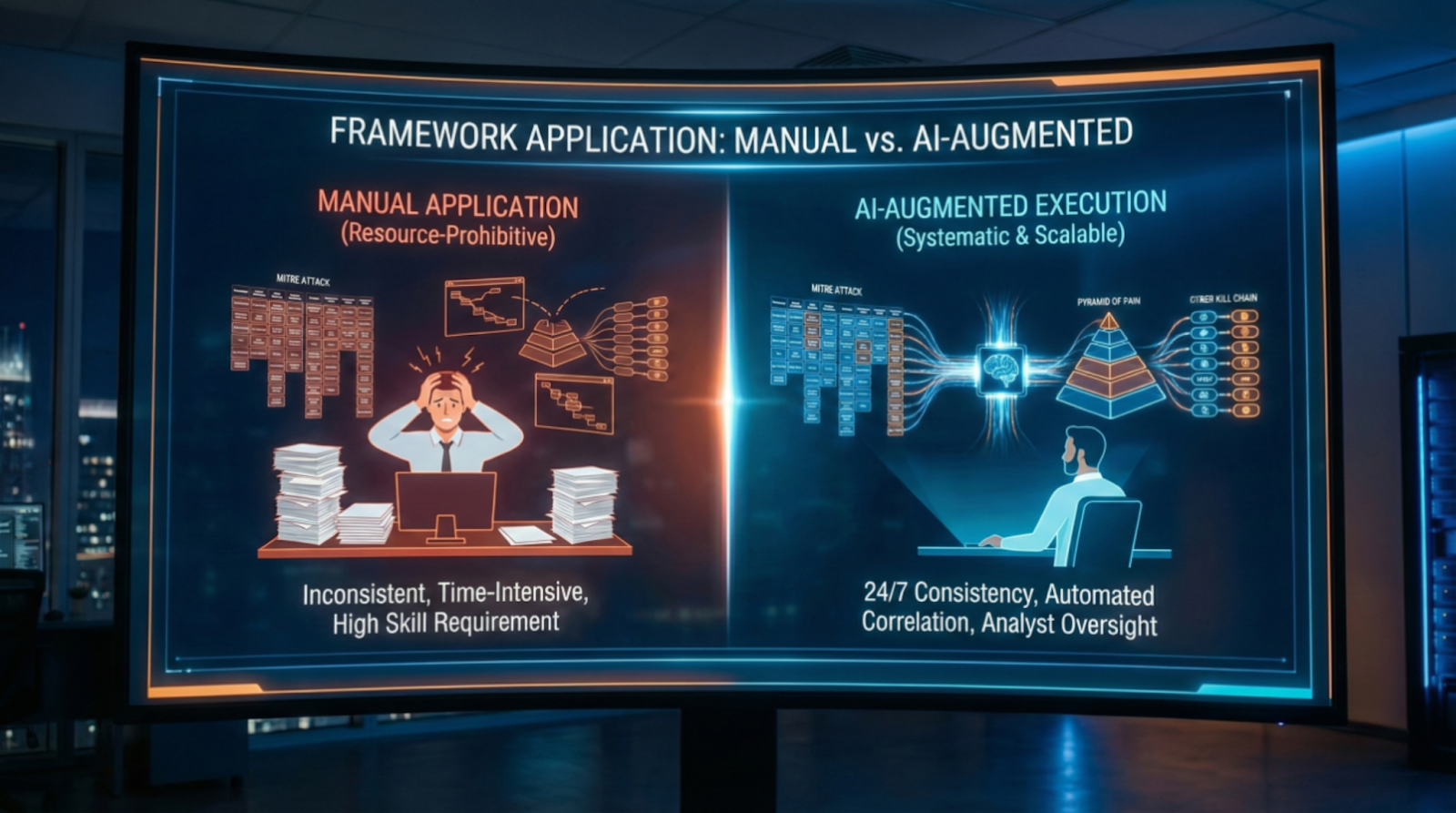
The reality gap: 48% of SOCs still describe hunting as "partially automated" using vendor tools (SANS 2025). Most teams understand frameworks intellectually but struggle with consistent manual application under operational pressure.
MITRE ATT&CK: The Behavior-Based Playbook
MITRE ATT&CK is the globally-accessible knowledge base of adversary tactics and techniques based on real-world observations.
Version 18.1 (December 2025):
- 14 tactics across attack lifecycle
- Hundreds of specific techniques
- Organized by adversary behavior (not tools or malware)
Why It Works
Behavior-focused approach catches malware-free attacks (81% of modern intrusions). Instead of looking for specific malware signatures, you look for behavioral patterns:
- Credential access techniques (T1003)
- Lateral movement methods (T1021)
- Persistence mechanisms (T1543)
Adversaries must use these behaviors regardless of which tools they deploy.
Manual Execution Challenges
- Requires deep knowledge of hundreds of techniques across 14 categories
- Time-intensive log correlation across multiple tools per technique
- Investigation coverage depends on analyst familiarity with specific techniques
How AI Automates ATT&CK Hunting
Pre-trained knowledge: Understands techniques without per-analyst training
Extracts TTPs: Analyzes threat reports and threat intelligence to extract TTPs
Federated hunts: Hunts across SIEM, EDR, identity tools
Framework mapping: Investigation summaries mapped to ATT&CK
Example: AI detects suspicious PowerShell execution, automatically correlates activity across endpoint and identity logs, maps to T1059.001 (PowerShell), checks for related techniques (credential access, lateral movement), presents ATT&CK-mapped investigation in under 5 minutes (vs. 30-45 minutes manual).
Pyramid of Pain: Prioritizing High-Impact Detection
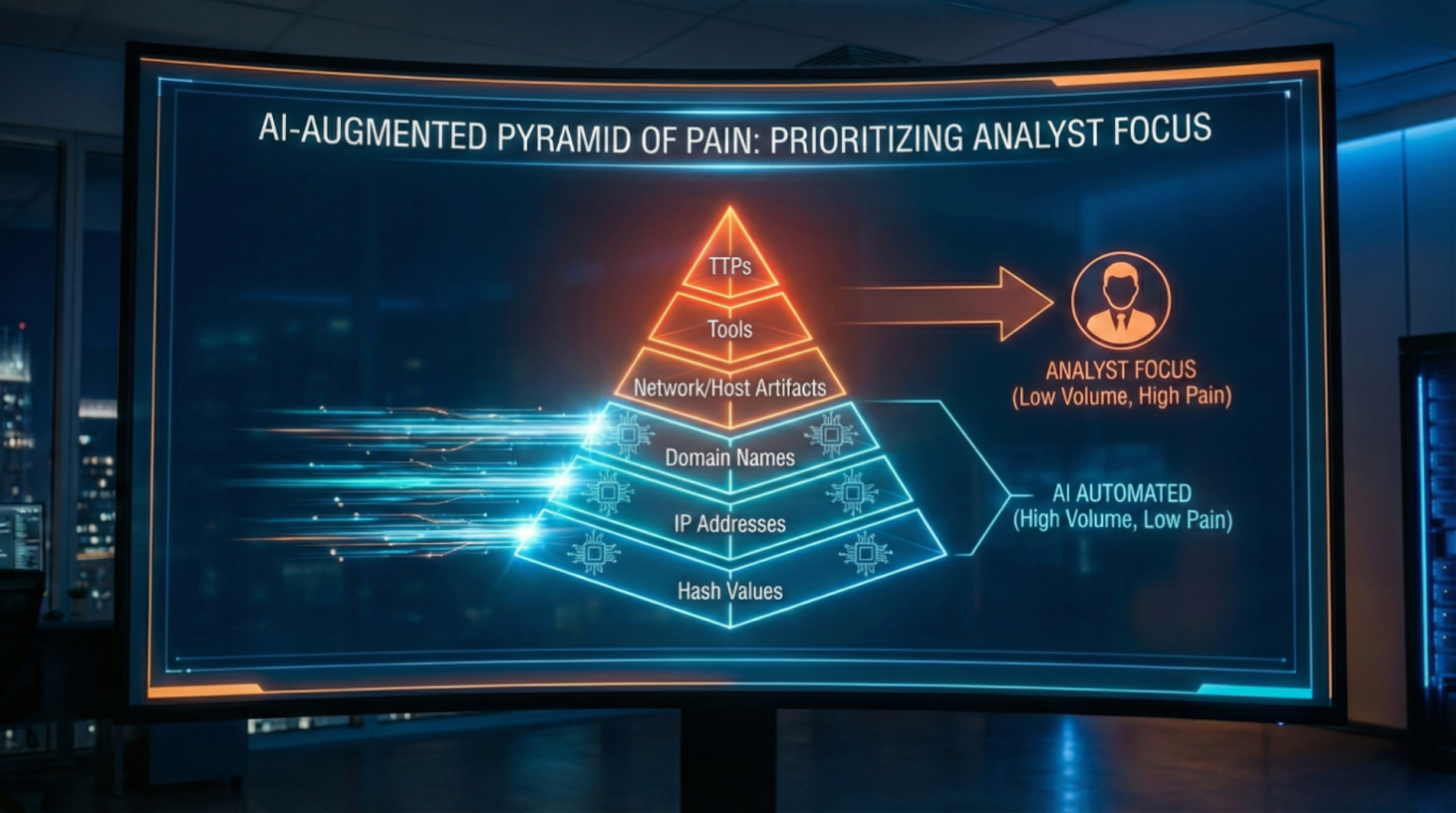
Created by David Bianco, this framework categorizes threat indicators by difficulty for adversaries to change.
The Six Levels
Why It Works
Detecting high-pyramid tactics, techniques, and procedures (TTPs) inflicts maximum pain on adversaries. When you catch and block TTPs, adversaries can't just recompile malware or change an IP. They must rethink their entire approach.
Modern SOCs report 60% reduction in successful attacks when prioritizing TTP-level detection over hash and IP hunting.
Manual Execution Challenges
Each pyramid level requires different detection approaches:
- Continuous rule refinement at every level
- Labor-intensive artifact/tool/TTP database maintenance
- Analysts spend disproportionate time on low-pyramid indicators (easier to automate but lower value)
How AI Automates Pyramid Hunting
Automatic escalation: Investigations prioritized by indicator sophistication
Low-pyramid processing: Hash/IP matches processed instantly with enrichment
High-pyramid escalation: TTP patterns flagged immediately for analyst review
Depth scaling: Investigation thoroughness matches pyramid level automatically
Example: 500 alerts across all pyramid levels. AI processes low-pyramid matches (known-bad IPs, hashes) instantly. Medium-pyramid alerts (artifacts, tools) batched for efficient review. High-pyramid TTP indicators escalated immediately. Result: analyst time focused on severe adversary pain points, not trivial indicators.
Cyber Kill Chain: Disrupting Attack Progression
Developed by Lockheed Martin, the Kill Chain models attack progression through seven sequential stages.
The Seven Stages
- Reconnaissance (Gathering target information)
- Weaponization (Creating attack tools)
- Delivery (Transmitting weapon to target)
- Exploitation (Triggering vulnerability)
- Installation (Installing malware/backdoor)
- Command & Control (Remote control channel)
- Actions on Objectives (Data theft, destruction)
Why It Works
Temporal context: Maps findings to attack progression
Early disruption: "Left-of-boom" hunting catches attacks before later-stage damage
Visibility assessment: Shows which stages your defenses cover and where gaps exist
Manual Execution Challenges
- Multi-system timeline reconstruction from fragmented logs
- Time pressure (late detection means attacker already established persistence)
- Quality varies with analyst experience
How AI Automates Kill Chain Analysis
Automatic timeline building: Correlates events across lifecycle stages
Stage mapping: Identifies sequences (Delivery → Exploitation → C2)
Gap highlighting: Shows where visibility might be incomplete
Coherent narratives: Unified attack stories vs. disconnected events
Example: Investigating potential lateral movement, AI correlates a phishing email from three days ago (Delivery) with credential access attempts (Exploitation) and subsequent RDP sessions to multiple hosts (C2). Hours of manual log searching happen automatically, presenting unified kill chain timeline for analyst assessment.
How AI Teams Apply Frameworks at Scale
Lack of skilled staff is the top barrier to sophisticated threat hunting (SANS 2025). AI augmentation bridges the gap between understanding frameworks and executing them consistently.
The AI Augmentation Model
Pre-trained framework knowledge
- Understands ATT&CK techniques, Pyramid levels, Kill Chain stages
- No manual training required
- Consistent application regardless of SOC workload or analyst availability
Continuous framework application
- Every alert investigation uses frameworks
- 24/7 operations (79% of SOCs) benefit from consistent methodology
- Not just the investigations experienced analysts have time for
Analyst oversight maintained
- AI handles systematic evidence gathering and framework mapping
- Analysts review framework-contextualized findings
- Human judgment drives threat assessment and response
Environment learning
- Adapts to your normal PowerShell usage
- Learns typical authentication patterns
- Understands legitimate admin tool behaviors
- Maintains framework rigor while learning environment specifics
This is systematic evidence gathering using proven methodologies, with security analysts maintaining control over hypothesis formation, threat prioritization, and response strategies.
Key Takeaways
- MITRE ATT&CK, Pyramid of Pain, and Cyber Kill Chain provide proven methodologies, but extracting TTPs from threat intelligence, creating hunt packs, and executing the hunts is resource-prohibitive for most SOC teams
- 48% of SOCs perform only "partially automated" hunting due to knowledge requirements (hundreds of techniques), time constraints (79% operate 24/7), and staffing limitations
- AI-augmented approach enables consistent framework application through automated evidence gathering while analysts maintain strategic oversight
- Operational impact: consistent investigation quality regardless of analyst experience or shift, faster response through automation, analyst focus on high-pyramid indicators