SOCless security eliminates the traditional analyst queue by routing alerts directly to engineers responsible for the systems affected. Organizations using SOCless models in tandem with AI SOC agents, like Mysten Labs, have cut alert noise by 99% and reduced alert investigation time from 30 minutes to one minute.
The approach responds to a familiar problem: too many alerts, too few analysts, and too much time lost to false positives. When engineers own alerts directly, AI SOC analysts like Dropzone AI make it sustainable by surfacing only what deserves attention. Here's how the model works and why more teams are adopting it.
What Does a SOCless Model Mean for Security Teams?
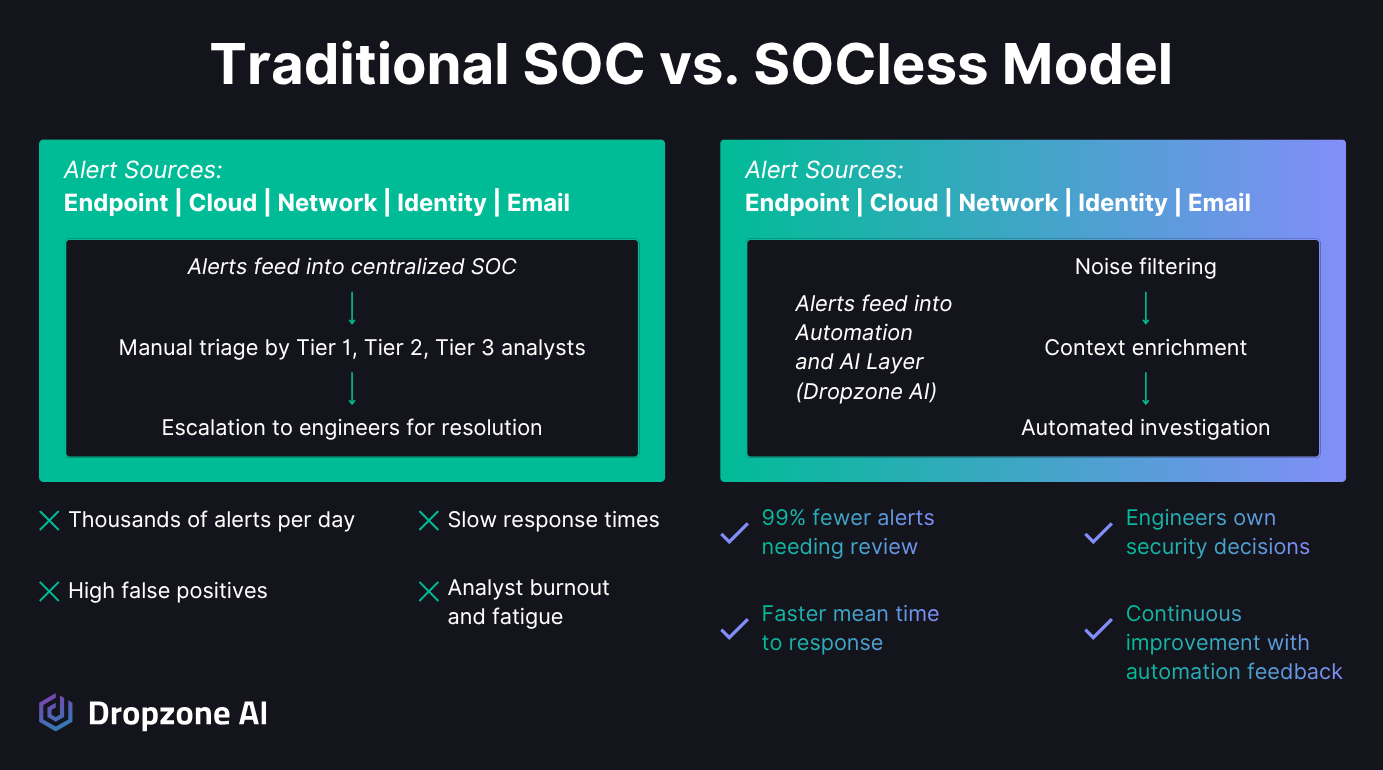
The SOCless approach rethinks how security operations should be structured. Instead of funneling every alert through a centralized team, it pushes ownership to the engineers closest to the systems. Here's how that plays out and why the model is catching on.
Want to dig deeper? Download the paper, SOCless Operating Model Report: Smashing the SIEM Stack for Fun and Profit.
How Does SOCless Differ from Traditional SOC Operations?
A SOCless model takes a different view of how security should work. Instead of a large team of analysts sitting in a centralized SOC, security ownership is pushed closer to the people building and maintaining the systems. These engineers know the systems they are protecting intimately and are able to more quickly identify strange or suspicious activity than a SOC analyst would.
In forward-thinking organizations, AI automation handles the repetitive, time-consuming triage, and escalated alerts go straight to the engineers who can take action. It's a leaner setup designed for teams that already run fast and value direct accountability.
Behind the scenes, the model relies on practices like detections-as-code, where detection rules are written, tested, and versioned just like software. Those rules generate high-fidelity alerts that are routed automatically with clear next steps. When alerts turn out to be noisy, they're tuned quickly and redeployed, creating a continuous improvement loop that keeps detection quality high. It fits naturally with DevOps and security-as-code practices, where engineers use automation and data pipelines to manage both reliability and security in the same workflow.
Why Are Companies Making the Shift?
Many startups use the SOCless model, but some more traditional organizations are moving toward SOCless operations because traditional SOCs simply can't keep up. Alert volume has exploded, while the pool of experienced analysts hasn't grown fast enough. Teams are spending too much time reacting to low-value alerts and not enough time improving detection logic or building better defenses.
A SOCless model helps reduce that noise by routing alerts directly to domain experts, supported by automation that filters and enriches data before it ever reaches them. The payoff includes:
- Faster response times with alerts going straight to the people who understand the systems
- Engineers addressing real issues instead of chasing false positives
- Security teams shifting focus from triage to building stronger detections
- Better alignment with how modern engineering teams already operate
The model does require a mindset change. Engineers take on more responsibility for responding to alerts, and automation has to be mature enough to handle routine work. When those pieces line up, the result is a security operation that's faster, more accurate, and sustainable at scale.
How Does SOCless Security Work in Practice?
Theory is one thing. Execution is another. Mysten Labs offers a clear example of what SOCless security looks like when it's running well, and what it took to get there.
What Challenges Do SOCless Teams Face?
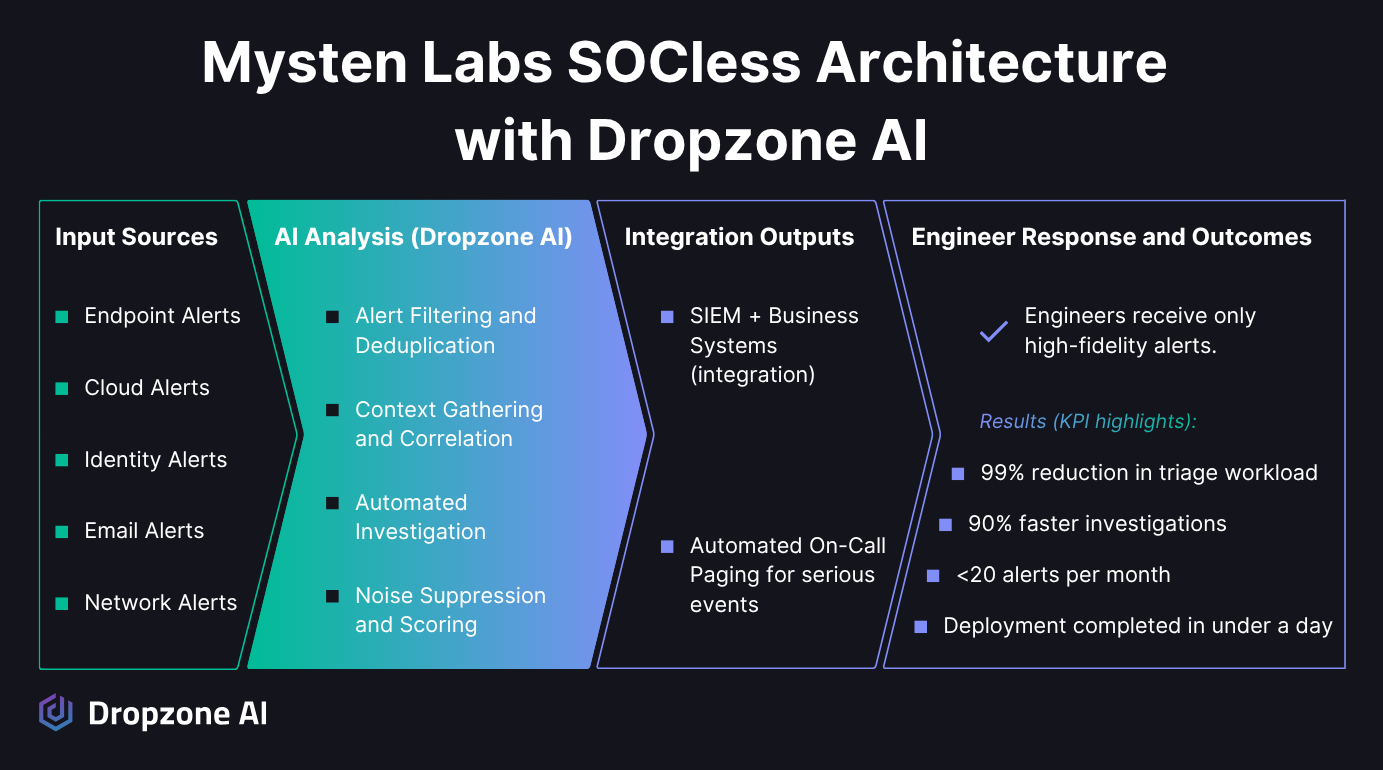
Mysten Labs provides a practical demonstration of how the SOCless model operates, incorporating autonomous AI agents. The web3 infrastructure company runs with a lean, senior engineering team where every member is staff level or higher, averaging more than fifteen years of experience. Rather than relying on a traditional SOC, security alerts flow directly to the engineers who own the systems.
The setup provides speed and clear accountability, but it also presents a challenge: managing thousands of alerts without overwhelming the infrastructure builders. Their tooling generated thousands of alerts monthly, with most being false positives. Engineers were spending valuable hours triaging noise instead of building and improving core infrastructure. Mysten needed a way to maintain observability and strong security coverage without burying the people driving their technology.
Engineers at Mysten Labs faced:
- Thousands of monthly alerts to review manually
- High false positive rates consuming investigation time
- 30-minute average investigation time per alert
- Reduced focus on core infrastructure development
How Did Dropzone AI Solve the Alert Overload Problem?
Paul Padilla, Head of Software and Infrastructure Security, wanted to protect his engineers' time without raising risk. After finding traditional SOAR tools too rigid, he turned to Dropzone AI, drawn to how it automates alert triage by replicating the techniques of elite human analysts. Deployment took less than a day, connecting to Mysten's SIEM and alert sources across endpoint, identity, cloud, email, and network.
The results were immediate. "We went from a fire hose where it feels like you're reading The Matrix to receiving only a few things a week, and each of those things matters," said Padilla.
Key Stat: Mysten Labs reduced monthly alerts from thousands to fewer than 20, a 99% reduction in noise, while cutting investigation time from 30 minutes to approximately one minute per alert.
After implementing Dropzone AI, Mysten Labs saw:
- 99% reduction in alert noise, from thousands per month to fewer than 20
- Investigation time cut from 30 minutes to approximately one minute per alert
- Engineers freed to focus on building rather than triaging
- Scalable security coverage without adding headcount
The company now runs a low-toil SOCless model that pairs automation with human expertise, built for how senior teams actually work.
How Do AI Analysts Make SOCless Security Work?
A SOCless model only works if something handles the investigative heavy lifting. That's where AI SOC analysts come in, bridging the gap between raw alerts and actionable findings.
What Role Does AI Play in Alert Investigation?
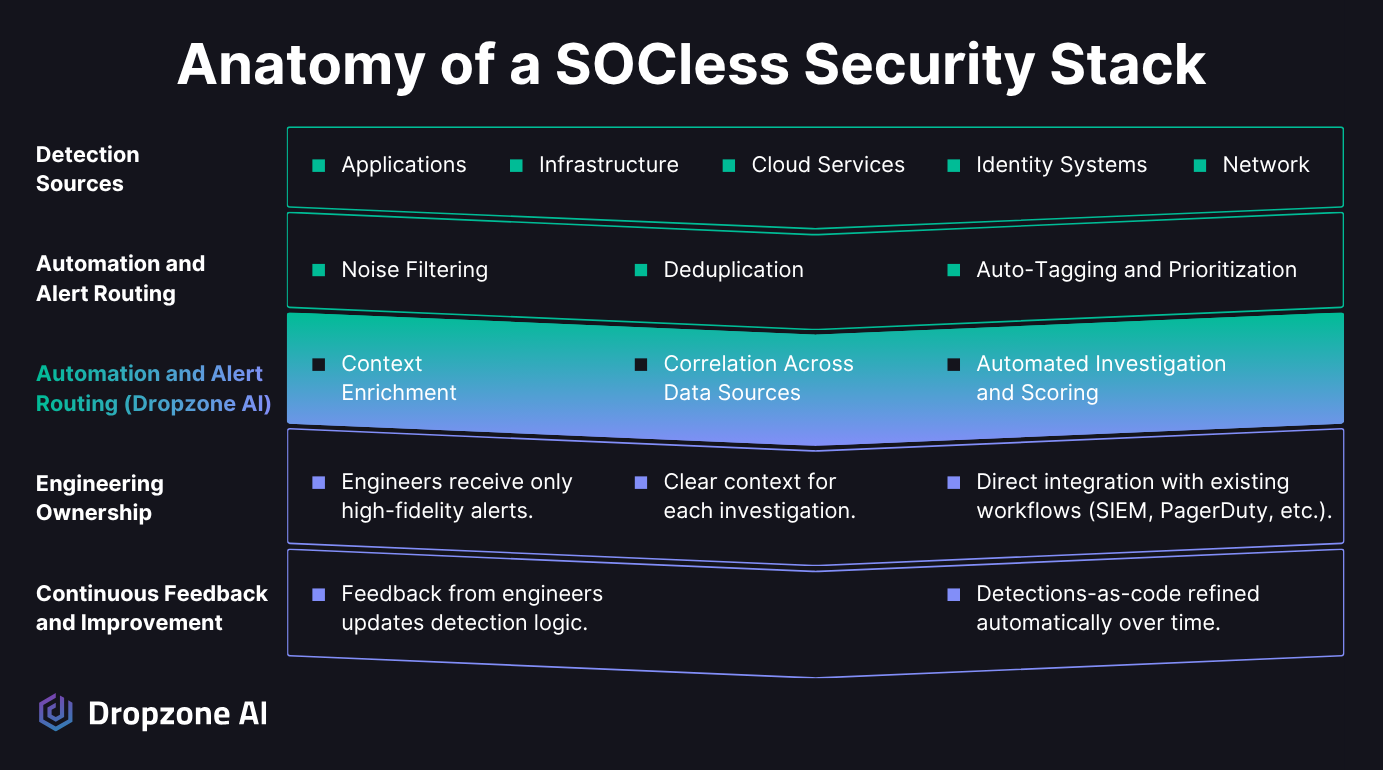
AI SOC analysts are what make a SOCless model practical for real teams. Dropzone AI works around the clock like your best analyst, but without the fatigue or the limitations of scale. It connects to more than 80 security tools across endpoint, cloud, identity, email, and network environments, automatically pulling the context you'd normally have to dig for. Instead of raw alerts, you get clear, evidence-backed findings that tell you exactly what matters.
Dropzone AI automatically handles:
- Cross-platform data correlation (EDR, cloud, identity, email, network)
- Context gathering from 80+ integrated security tools
- Evidence collection and validation
- False positive filtering through Context Memory
- Investigation quality improvement over time
There are no playbooks to build or maintain, no code to write, and no prompts to configure. Dropzone works out of the box.
That's the real difference. Dropzone AI filters out false positives and learns from every investigation through its Context Memory, so the alerts that reach your engineers are accurate and worth their time. Over time, it adapts to your environment, becoming more adept at distinguishing between what's normal and what's not. The result is a system that cuts through noise and delivers high-quality detections without constant manual work.
Can Small Teams Scale Security Without Adding Headcount?
AI changes how small teams think about scale. Dropzone AI takes on the heavy lifting of investigations by running queries, validating alerts, and correlating data so engineers only see what's relevant. It lets senior teams protect large, complex environments without spending hours in triage mode.
How AI enables small team scaling:
- Automated investigation workload (no manual triage)
- Continuous learning from environment patterns
- Real-time alert validation and correlation
- Evidence-backed findings delivered to engineers
- No playbook maintenance or code requirements
This model feels natural for engineering-driven organizations. It reduces repetitive work, improves response speed, and creates a feedback loop that continually strengthens over time. Mysten Labs is proof that SOCless security powered by AI makes teams faster, sharper, and more confident in their security posture.
Key Takeaways
- SOCless shifts security to engineers. Alerts go straight to system owners, supported by automation and detections-as-code.
- AI SOC analysts make it work at scale. Dropzone AI filters noise, investigates alerts, and surfaces only what matters.
- Proven results. Mysten Labs cut 99% of alert noise and freed engineers to focus on building.
Conclusion
Security teams using the SOCless model are rethinking their approach, focusing on fewer dashboards, fewer false positives, and more time spent on real engineering. AI SOC analysts are what make that shift possible. With tools like Dropzone AI, teams can finally cut through the noise, automate investigations, and focus on what actually moves security forward. It's a smarter, faster way to stay protected without burning out your people.
Want to learn more about the SOCless operating model and how AI fits in? Download the paper, SOCless Operating Model Report: Smashing the SIEM Stack for Fun and Profit.














