Blockchain and web3 startups operate with small, highly skilled teams that move quickly across distributed infrastructure. Their threat exposure, however, mirrors that of much larger enterprises, with constant scanning, sprawling cloud assets, and advanced nation-state adversaries. Traditional SOC structures that rely on staffing and manual triage that don't align with lean engineering cultures, and probably wouldn’t work well for that threat environment anyway. In this article, we'll look at how a SOCless model, powered by AI SOC Agents, gives blockchain and web3 teams the automation and visibility they need to stay secure without slowing down development.
The Realities of Defending a Lean Web3 Stack
Why Do Web3 Teams Struggle With Alert Overload?
Web3 and blockchain teams receive thousands of monthly alerts from endpoints, identity systems, cloud infrastructure, and blockchain telemetry. In a SOCless model, these alerts go directly to the engineers responsible for building the infrastructure and applications.
Each false positive demands context checks and log analysis that pulls engineers away from development work. When small teams spend more time triaging than building, both security and productivity suffer, and genuine threats get buried in noise.
For most web3 engineering teams, alert fatigue is not the worst outcome. Each monitoring system endpoint, identity, smart contract, cloud, or blockchain telemetry feed creates noise that distracts these infrastructure and application engineers from their jobs, slowing the organization down.
What should help protect assets quickly becomes noise:
- False positives demand immediate attention - Every alert requires context checks, log pulls, and Slack threads
- Engineers diverted from core work - Time spent triaging instead of building features and infrastructure
- Security and productivity both decline - Alert fatigue leads to ignored warnings and buried genuine threats
- Response time stretches - What should take minutes extends to hours as backlogs grow
- The pattern repeats - More tools generate more alerts with less clarity
For teams without a team of full-time SOC analysts, this gap grows wider every week. The pattern repeats: more tools, more alerts, less clarity. That's how alert volume quietly becomes a security risk in itself.
How Have State-Backed Actors Changed Web3 and Blockchain Security Threats?
The threat profile for blockchain and web3 companies has changed dramatically in the past two years. Adversaries once limited to phishing and wallet exploits are now using automation and AI-driven reconnaissance to move faster and blend in more effectively.
As Anthropic's August 2025 threat report notes, state-backed actors are scaling up with AI:
- Automated reconnaissance - Groups linked to North Korea now scale operations with AI assistance
- Developer impersonation - Adversaries pose as legitimate contributors to infiltrate Bitcoin, Ethereum, Solana, and other projects
- Surgical precision targeting - Focus on wallets and infrastructure with sophisticated techniques
- Subtle attack patterns - Single login anomalies or GitHub access requests that appear legitimate
- Increased operational tempo - Attacks happen faster, requiring immediate validation with incomplete context
For lean web3 teams, this kind of activity raises the operational tempo. The difference between a nuisance alert and a targeted intrusion can be subtle, a single login pattern or a GitHub access request that looks slightly off. With limited bandwidth, infrastructure engineers have to prioritize quickly, often with incomplete context.
The result is more stress, slower validation, and higher stakes. The attackers are scaling their operations through automation, and the defenders need technology that can match that pace without adding more people to the equation.
Traditional SOCs Can't Keep Up With Web3's Tempo
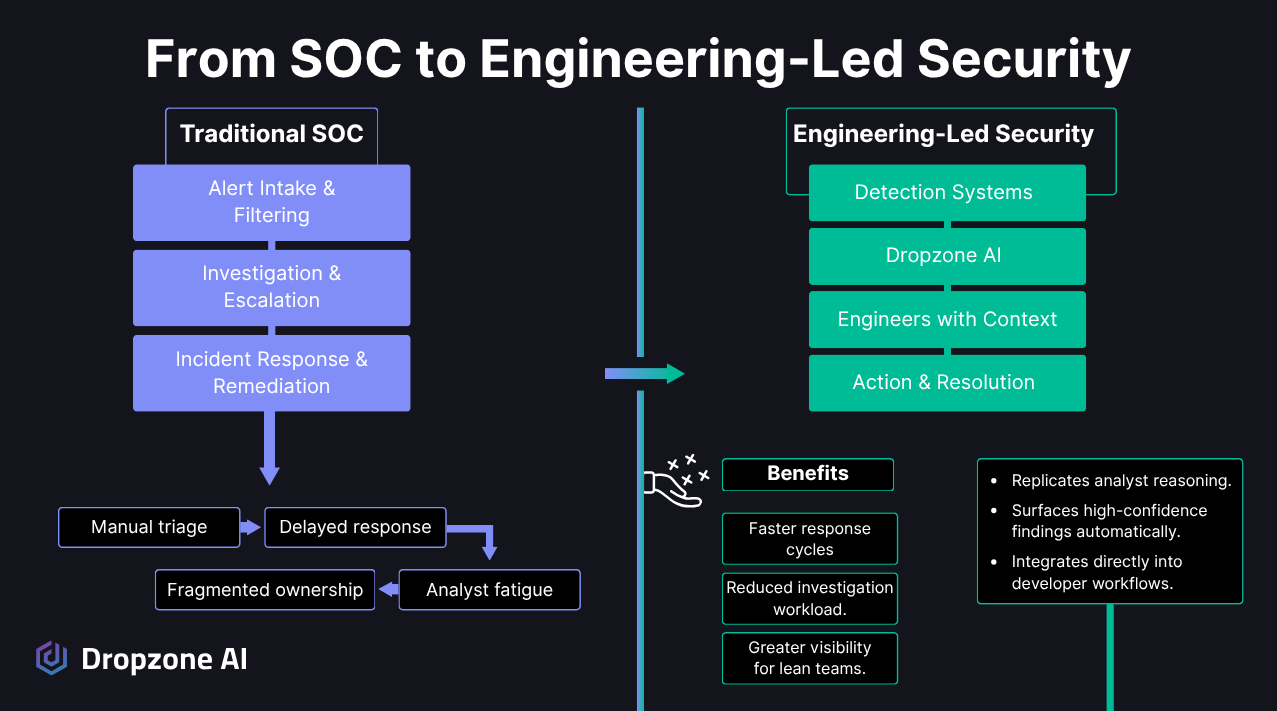
Why Must Security Operations Match Engineering Velocity?
Traditional SOCs rely on ticket queues, escalation tiers, and analyst handoffs that require volume, headcount, and repeatable staffing patterns that don't exist in lean web3 teams. Web3 engineers own systems end-to-end and make real-time changes, requiring security to operate at the same velocity. A SOCless structure embeds security directly into engineering workflows where context lives and decisions happen.
Traditional SOCs are built around ticket queues, escalation tiers, and handoffs between analysts. That structure depends on volume, headcount, and repeatable staffing patterns, none of which exist in lean blockchain teams.
Web3 and blockchain engineers tend to own their systems end-to-end and make changes in real time. Security has to follow the same rhythm. The people who write and maintain the code are also the ones best positioned to investigate and respond when something looks strange or suspicious.
Adopting an engineering-driven model means treating detection and response the way site reliability engineers treat uptime. Toil gets automated. Human attention is directed toward impact, not repetition.
A SOCless structure brings security operations into the same workflows as DevOps, where context lives and change happens. Engineers stay in their own environment, CI/CD, GitHub, Slack, or cloud dashboards, and security intelligence moves with them, rather than being trapped in a separate SOC stack.
What Are the Bottlenecks in Manual Security Response?
Even with deep expertise into the systems they are defending, engineers cannot manually keep up with the volume and complexity of today's alerts. Manual investigation requires correlating multiple data sources, authentication logs, API traces, access control data, and network paths, a time-consuming process that creates fatigue and increases the chance that genuine threats go unnoticed while false positives continue demanding attention.
Each event pulls context from multiple systems:
- Authentication logs and API traces - Tracking user and service behavior across systems
- Access control data - Validating permissions and authorization patterns
- Network traffic paths - Understanding communication patterns and anomalies
- Cloud infrastructure telemetry - Monitoring resource usage and configuration changes
- Time-intensive correlation - Manually connecting signals takes significant effort
When everything has to be checked by hand, time is wasted and response slows down. Over time, that delay increases the chance that a real issue will go unnoticed while false positives continue to demand attention.
What lean teams need is software that can think like an analyst and handle the repetitive parts of investigation on its own. Autonomous systems that can collect data, test hypotheses, and flag the handful of alerts that truly require human decision-making.
That kind of autonomy doesn't replace judgment; it amplifies it. With repetitive work offloaded, engineers can focus on improving detections, hardening systems, and staying ahead of the next attack rather than being buried in yesterday's alerts.
How Dropzone AI Makes the SOCless Model Work
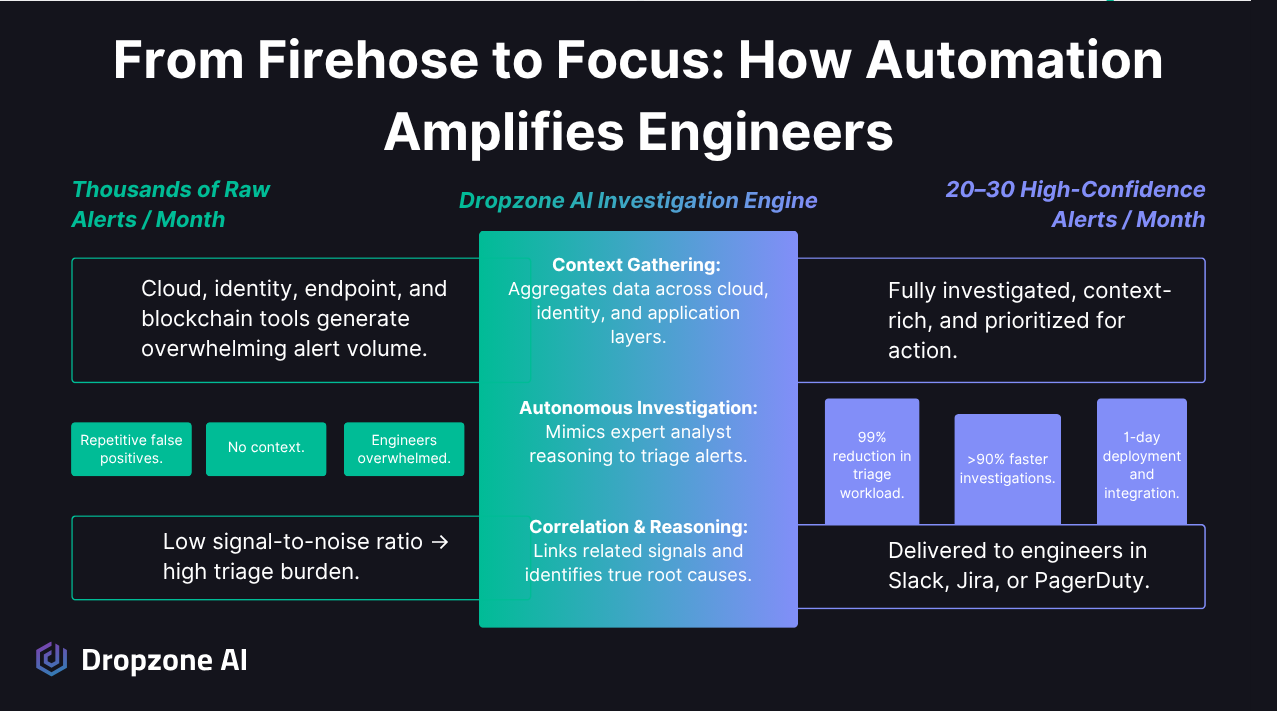
How Does AI Automation Replace Traditional SOC Functions?
Dropzone's AI SOC Agents perform end-to-end alert investigations autonomously, gathering context from identity, endpoint, and cloud sources, analyzing behavior, and surfacing only findings that require human review. The platform integrates seamlessly with tech stacks including Panther, AWS, GitHub, and Slack, delivering investigated alerts directly into engineering workflows rather than separate SOC systems.
Dropzone's AI SOC Agents are built to think and operate like experienced analysts, only faster and without fatigue. Each alert that enters the system is investigated end-to-end: gathering context from identity, endpoint, and cloud sources, analyzing behavior, and surfacing only the findings that actually require human review. Instead of a static queue, engineers see a small, focused stream of high-quality alerts that already include relevant evidence and reasoning.
The platform integrates cleanly into web3 and blockchain security stacks:
- Panther or other SIEM - Detection and alerting
- AWS - Cloud infrastructure monitoring
- GitHub - Code repository security
- Slack - Team communication and notifications
That makes the workflow natural for engineering-led teams. Alerts are automatically investigated in the background, with summaries delivered to where teams already work. The result is less noise, faster detection, and fewer wasted cycles chasing false positives. Security operations are part of the build process rather than a separate overhead task.
Can Web3 and Blockchain Teams Maintain Security Without a Traditional SOC?
Mysten Labs, a Web3 infrastructure company, demonstrates that lean teams can achieve enterprise-grade security without dedicated SOC analysts. After integrating Dropzone AI, their alert volume dropped 99% and investigation time decreased by over 90%, enabling their small engineering team to maintain comprehensive security coverage while focusing on infrastructure development rather than manual triage.
Mysten Labs relies on a small, highly experienced engineering team and has no dedicated SOC. They integrated Dropzone to handle the continuous stream of alerts across their environment.
Once deployed, the difference was immediate: alert volume dropped by 99%, and the time engineers spent investigating each alert was reduced by more than 90%. What had once been hours of manual triage became minutes of quick validation.
As Mysten Labs' Head of Software and Infrastructure Security, Paul Padilla, put it:
"You can't hire your way out of alert overload. The only way to scale is to eliminate toil."
That mindset reflects what many web3 teams are realizing. Automation isn't a shortcut; it's how senior engineers keep security aligned with the pace of development. With Dropzone’s AI SOC analysts handling the noise, engineers can return their focus to strengthening infrastructure and planning, rather than reacting to yesterday's alerts.
Conclusion
For lean web3 and blockchain teams, the question isn't whether to move fast or stay safe; it's how to do both at once. The SOCless model, powered by AI SOC Agents, gives engineers the freedom to build quickly while staying protected from advanced threats. Automation handles the noise, surfaces real issues, and turns investigation into a fast, reliable part of daily work instead of a burden. The next step is simple: see it firsthand and take the self-guided demo of Dropzone AI.
Key Takeaways
- Alert overload affects lean web3 teams disproportionately, with thousands of monthly data points creating noise
- State-backed actors now use AI for reconnaissance and impersonation, increasing threat sophistication
- Traditional SOC structures don't align with engineering-led workflows that require real-time decision-making
- AI SOC Agents investigate autonomously, eliminating 99% of alert noise while maintaining full coverage
- Mysten Labs achieved 90%+ time savings without hiring dedicated security analysts
- SOCless security enables enterprise-grade protection at startup scale through intelligent automation